03_旁挂负载分担组网场景
拓扑:1
二层交换配置:
拓扑:5
二层交换配置
使用传统三层架构中MSTP+VRRP组网形式
VLAN 2--->SW3,SW4作为备份
VLAN 3--->SW4,SW3作为备份
MSTP设计--->SW3、4、5运行
实例1:VLAN 2
实例2:VLAN 3
SW3是实例1的主根,实例2的备份根;SW4是实例2的主根,实例1的备份根
IP地址规划:
SW3:
VLAN 2:192.168.2.1/24
VLAN 3:192.168.3.1/24
SW4:
VLAN 2:192.168.2.2/24
VLAN 3:192.168.3.2/24
虚拟IP:
VLAN 2:192.168.2.254/24
VLAN 3:192.168.3.254/24
vlan配置:
sw3:
[sw3]sysname sw3 ----修改名称
[sw3]vlan batch 2 3 ----创建vlan2,3
interface GigabitEthernet0/0/3
port link-type trunk
port trunk allow-pass vlan 2 to 3
interface GigabitEthernet0/0/4
port link-type trunk
port trunk allow-pass vlan 2 to 3
sw4:
[Huawei]sysname sw4
[sw4]vlan batch 2 3
[sw4]interface GigabitEthernet 0/0/3
[sw4-GigabitEthernet0/0/3]port link-type trunk
[sw4-GigabitEthernet0/0/3]port trunk allow-pass vlan 2 3[sw4-GigabitEthernet0/0/3]interface GigabitEthernet 0/0/4
[sw4-GigabitEthernet0/0/4]port link-type trunk
[sw4-GigabitEthernet0/0/4]port trunk allow-pass vlan 2 3
sw5:
[Huawei]sysname sw5
[sw5]vlan batch 2 3[sw5]interface GigabitEthernet 0/0/3
[sw5-GigabitEthernet0/0/3]port link-type access
[sw5-GigabitEthernet0/0/3]port default vlan 2[sw5-GigabitEthernet0/0/4]interface GigabitEthernet 0/0/4
[sw5-GigabitEthernet0/0/4]port link-type access
[sw5-GigabitEthernet0/0/4]port default vlan 3[sw5-GigabitEthernet0/0/4]interface GigabitEthernet 0/0/1
[sw5-GigabitEthernet0/0/1]port link-type trunk
[sw5-GigabitEthernet0/0/1]port trunk allow-pass vlan 2 3[sw5-GigabitEthernet0/0/1]interface GigabitEthernet 0/0/2
[sw5-GigabitEthernet0/0/2]port link-type trunk
[sw5-GigabitEthernet0/0/2]port trunk allow-pass vlan 2 3
mstp生成树配置:
sw3:
[sw3]stp enable ----开启stp
[sw3]stp mode mstp ----修改模式为mstp[sw3]stp region-configuration ----进入域配置视图
[sw3-mst-region]region-name aa ----配置域名
[sw3-mst-region]instance 1 vlan 2 ----实例1映射vlan2
[sw3-mst-region]instance 2 vlan 3 ----实例2映射vlan3
[sw3-mst-region]active region-configuration -----激活stp配置[sw3]display stp region-configuration -----查看stp信息
:2、
:2
[sw3]stp instance 1 root primary ----实例1主根
[sw3]stp instance 2 root secondary ----实例2备跟[sw3]stp instance 0 root primary ----实例0主根
实例0除了vlan2,3的其他vlan可以配可以不配因为没有用到其他vlan
sw4:
[sw4]stp enable
[sw4]stp mode mstp[sw4]stp region-configuration
[sw4-mst-region]region-name aa
[sw4-mst-region]instance 1 vlan 2
[sw4-mst-region]instance 2 vlan 3
[sw4-mst-region]active region-configuration[sw4]stp instance 1 root secondary ----实例1备根
[sw4]stp instance 2 root primary ---实例2主根
[sw4]stp instance 0 root secondary ---实例0备根
sw5:
[sw5]stp enable
[sw5]stp mode mstp[sw5]stp region-configuration
[sw5-mst-region]region-name aa
[sw5-mst-region]instance 1 vlan 2
[sw5-mst-region]instance 2 vlan 3
[sw5-mst-region]active region-configuration因为根是sw3,4所以sw5就不要配主备根
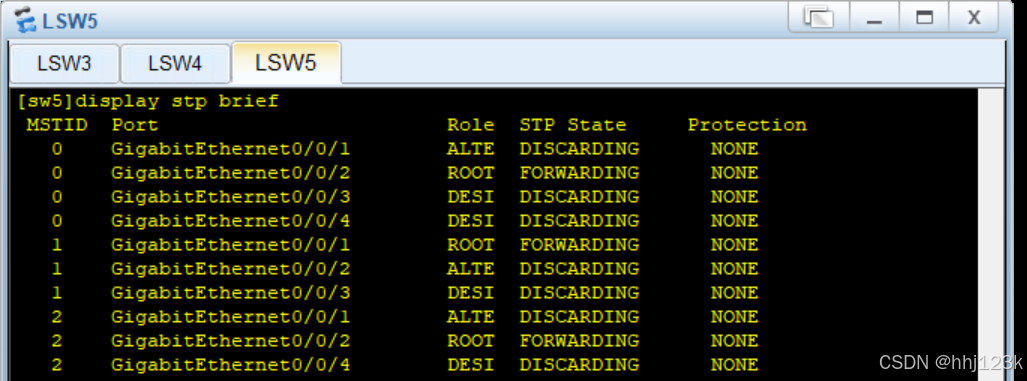
[sw5]display stp brief ----查看stp信息
:3
vlanif接口和vrrp配置
sw3:
[sw3]interface Vlanif 2 ----配置vlan2的vlanif接口
[sw3-Vlanif2]ip address 192.168.2.1 24
----sw3是vlan2的主根
[sw3-Vlanif2]vrrp vrid 1 virtual-ip 192.168.2.254 ---配置vrrp的虚拟ip为2.254
[sw3-Vlanif2]vrrp vrid 1 priority 120 ----修改优先级
[sw3-Vlanif2]vrrp vrid 1 preempt-mode timer delay 20 ---修改抢占延时
[sw3-Vlanif2]vrrp vrid 1 track interface GigabitEthernet 0/0/1 reduced 15 ----监控0/0/1和2两个接口当一个接口故障后sw3优先级减少15,这样只有当两个接口都故障后sw3的优先级才会比sw4低,sw3才会改变自身状态
[sw3-Vlanif2]vrrp vrid 1 track interface GigabitEthernet 0/0/2 reduced 15[sw3]interface Vlanif 3
[sw3-Vlanif3]ip address 192.168.3.1 24[sw3-Vlanif3]vrrp vrid 1 virtual-ip 192.168.3.254 ---配置vrrp的虚拟IP为3.254---因为sw3是vlan3的备根所以只要配置vrrp的虚拟IP就好
sw4:
[sw4]interface Vlanif 2
[sw4-Vlanif2]ip address 192.168.2.2 24[sw4-Vlanif2]vrrp vrid 1 virtual-ip 192.169.2.254 ----这里sw4是vlan2的备根所以只要配置虚拟IP
[sw4]interface Vlanif 3
[sw4-Vlanif3]ip address 192.168.3.2 24
[sw4-Vlanif3]vrrp vrid 1 virtual-ip 192.168.3.254
[sw4-Vlanif3]vrrp vrid 1 priority 120
[sw4-Vlanif3]vrrp vrid 1 preempt-mode timer delay 20
[sw4-Vlanif3]vrrp vrid 1 track interface GigabitEthernet 0/0/1 reduced 15
[sw4-Vlanif3]vrrp vrid 1 track interface GigabitEthernet 0/0/2 reduced 15
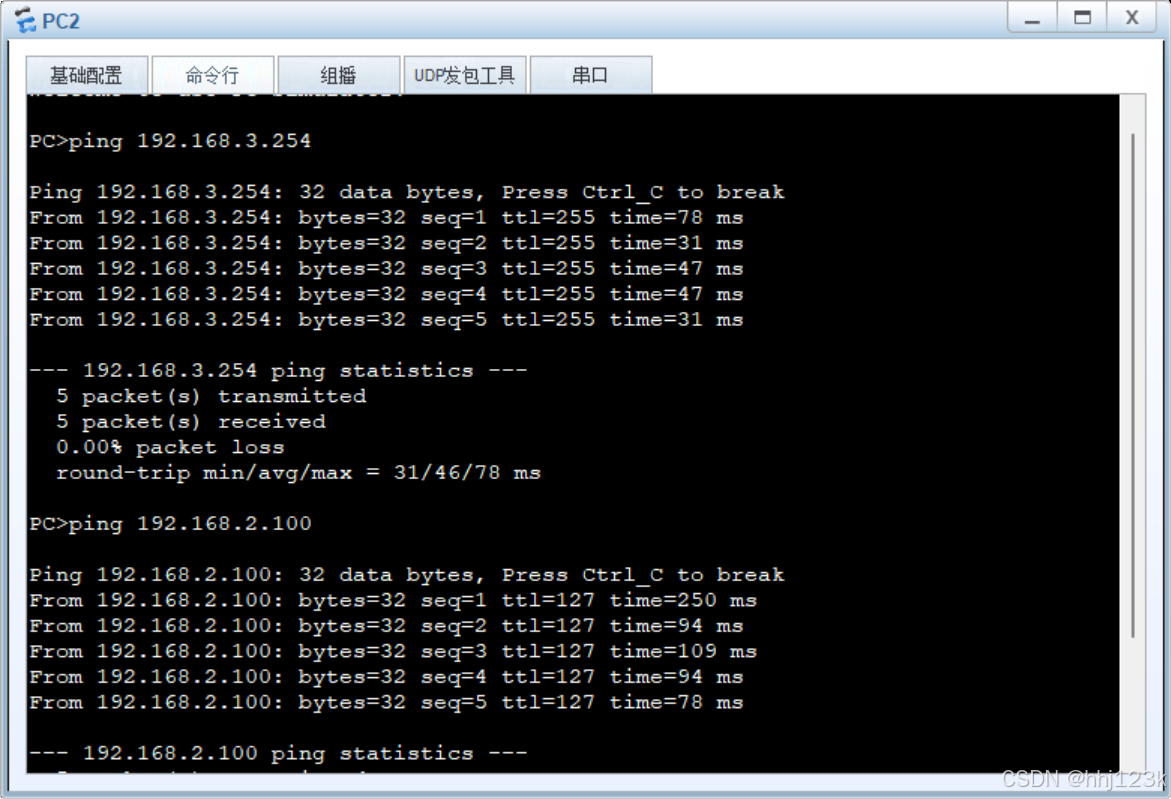
测试:pc2ping网关和pc1看是否可以ping通:4
汇聚到核心层路由配置
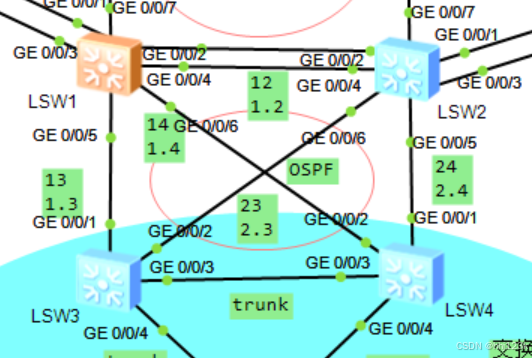
拓扑:6
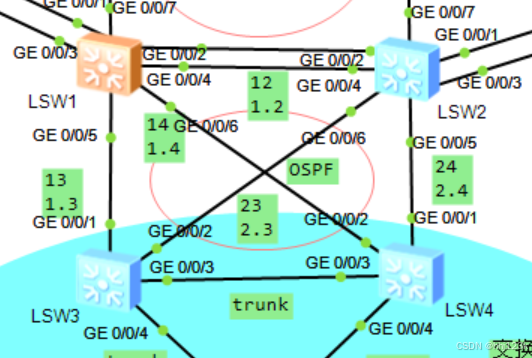
SW1-SW2:VLAN 12---10.1.2.0/24
SW1-SW3:VLAN 13---10.1.3.0/24
SW1-SW4:VLAN 14---10.1.4.0/24
SW2-SW3:VLAN 23---10.2.3.0/24
SW2-SW4:VLAN 24---10.2.4.0/24
sw4-sw5之间部建立ospf
vlan和接口配置:
sw3:
[sw3]vlan batch 13 23
[sw3]interface GigabitEthernet 0/0/1
[sw3-GigabitEthernet0/0/1]port link-type access
[sw3-GigabitEthernet0/0/1]port default vlan 13
[sw3-GigabitEthernet0/0/1]undo stp enable ----关闭stp,防止环路[sw3-GigabitEthernet0/0/1]interface GigabitEthernet 0/0/2
[sw3-GigabitEthernet0/0/2]port link-type access
[sw3-GigabitEthernet0/0/2]port default vlan 23
[sw3-GigabitEthernet0/0/2]undo stp enable[sw3]interface Vlanif 13
[sw3-Vlanif13]ip address 10.1.3.3 24[sw3-Vlanif13]interface Vlanif 23
[sw3-Vlanif23]ip address 10.2.3.3 24
sw4:
[sw4]vlan batch 14 24
[sw4]interface GigabitEthernet 0/0/1
[sw4-GigabitEthernet0/0/1]port link-type access
[sw4-GigabitEthernet0/0/1]port default vlan 24
[sw4-GigabitEthernet0/0/1]undo stp enable[sw4-GigabitEthernet0/0/1]interface GigabitEthernet 0/0/2
[sw4-GigabitEthernet0/0/2]port link-type access
[sw4-GigabitEthernet0/0/2]port default vlan 14
[sw4-GigabitEthernet0/0/2]undo stp enable[sw4]interface Vlanif 14
[sw4-Vlanif14]ip address 10.1.4.4 24[sw4-Vlanif14]interface Vlanif 24
[sw4-Vlanif24]ip address 10.2.4.4 24
sw1:
[sw1]vlan batch 12 to 14
[sw1]interface GigabitEthernet 0/0/5
[sw1-GigabitEthernet0/0/5]port link-type access
[sw1-GigabitEthernet0/0/5]port default vlan 13
[sw1-GigabitEthernet0/0/5]undo stp enable
[sw1-GigabitEthernet0/0/5]interface GigabitEthernet 0/0/5
[sw1-GigabitEthernet0/0/5]port link-type access
[sw1-GigabitEthernet0/0/5]undo stp enable
[sw1-GigabitEthernet0/0/5]port default vlan 14[sw1]interface GigabitEthernet 0/0/4
[sw1-GigabitEthernet0/0/4]port link-type trunk
[sw1-GigabitEthernet0/0/4]port trunk allow-pass vlan 12
[sw1-GigabitEthernet0/0/4]undo port trunk allow-pass vlan 1
[sw1-GigabitEthernet0/0/4]undo stp enable
vlanif接口配置在下面交换机vrf区域划分
sw2:
[sw2]vlan batch 12 23 24
[sw2]interface GigabitEthernet 0/0/5
[sw2-GigabitEthernet0/0/5]port link-type access
[sw2-GigabitEthernet0/0/5]port default vlan 24
[sw2-GigabitEthernet0/0/5]undo stp enable[sw2-GigabitEthernet0/0/5]interface GigabitEthernet 0/0/6
[sw2-GigabitEthernet0/0/6]undo stp enable
[sw2-GigabitEthernet0/0/6]port link-type access
[sw2-GigabitEthernet0/0/6]port default vlan 23[sw2]interface GigabitEthernet 0/0/4
[sw2-GigabitEthernet0/0/4]port link-type trunk
[sw2-GigabitEthernet0/0/4]port trunk allow-pass vlan 12
[sw2-GigabitEthernet0/0/4]undo port trunk allow-pass vlan 1
[sw2-GigabitEthernet0/0/4]undo stp enable
ospf配置:
sw3:
[sw3]ospf 1 router-id 3.3.3.3
[sw3-ospf-1]area 0
[sw3-ospf-1-area-0.0.0.0]network 10.1.3.3 0.0.0.0
[sw3-ospf-1-area-0.0.0.0]network 10.2.3.3 0.0.0.0
[sw3-ospf-1-area-0.0.0.0]network 192.168.2.1 0.0.0.0
[sw3-ospf-1-area-0.0.0.0]network 192.168.3.1 0.0.0.0[sw3-ospf-1]silent-interface Vlanif 2 ----开启vlan2,3的静默接口,让sw3,4之间不要建邻
[sw3-ospf-1]silent-interface Vlanif 3
创建vrf,并将对于接口划入(sw1,sw2上的vlanif接口)
因为SW1和SW2需要被分割为两台设备,分别与上下行设备连接,故需要先创建VRF空间,其中
GE0/0/3-GE0/0/6属于该空间接口。
VRF空间配置信息: 名称:VRF
RD:100:1 RT:100:1
sw1:
[sw1]ip vpn-instance VRF ---创建VRF空间
[sw1-vpn-instance-VRF]route-distinguisher 100:1 --设定RD值
[sw1-vpn-instance-VRF-af-ipv4]vpn-target 100:1 both ---设定RT值
[sw1-Vlani12]ip binding vpn-instance VRF ----将接口划入到VRF这个交换机中,在接口进行
配置之前执行
[sw1]interface Vlanif 12
[sw1-Vlanif12]ip address 10.1.2.1 24
[sw1-Vlanif12]ip binding vpn-instance vrf ----将对于接口划入vrf,最好在配置前划入,划入后会把划入前的配置移除
[sw1]interface Vlanif 13
[sw1-Vlanif13]ip binding vpn-instance vrf
[sw1-Vlanif13]ip address 10.1.3.1 24[sw1-Vlanif13]interface Vlanif 14
[sw1-Vlanif14]ip binding vpn-instance vrf
[sw1-Vlanif14]ip address 10.1.4.1 24
sw2:
[Huawei]sysname sw2
[sw2]ip vpn-instance vrf
[sw2-vpn-instance-vrf]route-distinguisher 100:1
[sw2-vpn-instance-vrf-af-ipv4]vpn-target 100:1 both
[sw2]interface Vlanif 12
[sw2-Vlanif12]ip binding vpn-instance vrf
[sw2-Vlanif12]ip address 10.1.2.2 24
[sw2-Vlanif12]interface Vlanif 23
[sw2-Vlanif13]ip binding vpn-instance vrf
[sw2-Vlanif13]ip address 10.2.3.2 24
[sw2-Vlanif13]interface Vlanif 24
[sw2-Vlanif14]ip binding vpn-instance vrf
[sw2-Vlanif14]ip address 10.2.4.2 24
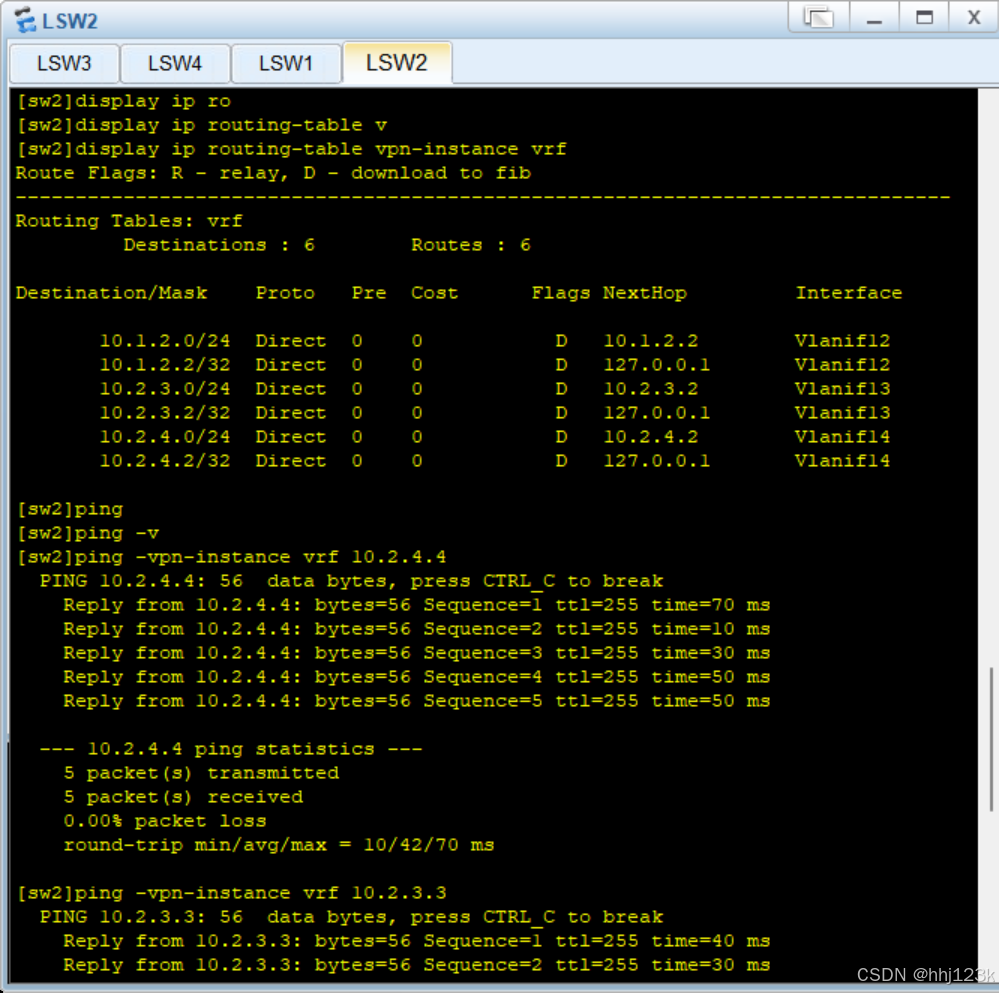
[sw2]display ip routing-table vpn-instance vrf ----查看vrf的ip信息
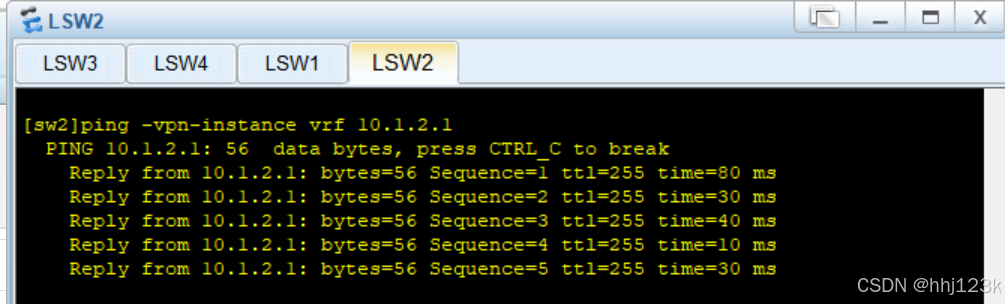
[sw2]ping -vpn-instance vrf 10.1.2.1
----pingsw1看是否能通
:7,8
:7,8
配置ospf
sw3:上面配过了
sw4:上面配过了
sw1:
[sw1]ospf 1 router-id 1.1.1.1 vpn-instance vrf
[sw1-ospf-1]area 0
[sw1-ospf-1-area-0.0.0.0]network 10.1.2.1 0.0.0.0
[sw1-ospf-1-area-0.0.0.0]network 10.1.3.1 0.0.0.0
[sw1-ospf-1-area-0.0.0.0]network 10.1.4.1 0.0.0.0
sw2:
[sw2]ospf 1 router-id 2.2.2.2 vpn-instance vrf ---宣告是在sw2的划分的那个交换机的(vrf的)
[sw2-ospf-1]area 0
[sw2-ospf-1-area-0.0.0.0]network 10.1.2.2 0.0.0.0
[sw2-ospf-1-area-0.0.0.0]network 10.2.3.2 0.0.0.0
[sw2-ospf-1-area-0.0.0.0]network 10.2.4.2 0.0.0.0
[sw1]display ospf peer brief ----查看ospf邻居表
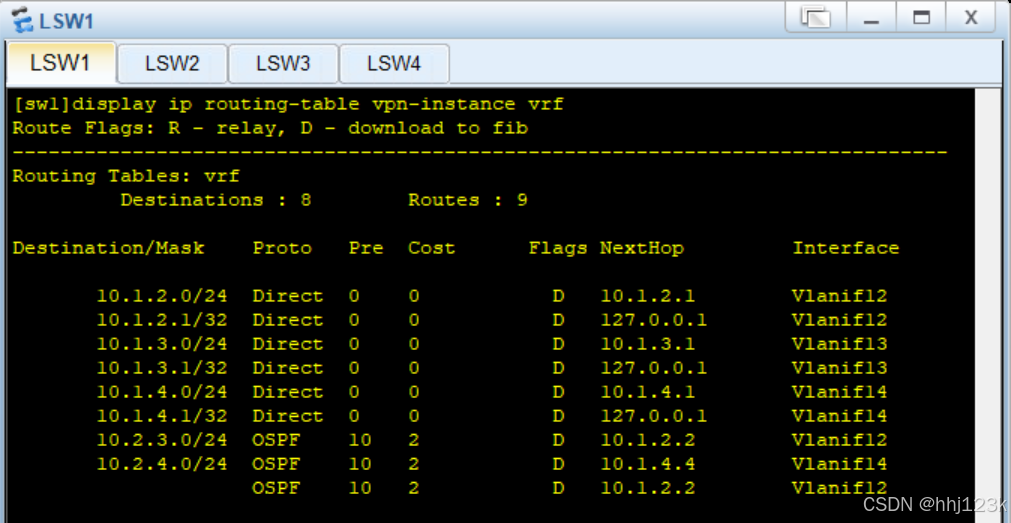
[sw1]display ip routing-table vpn-instance vrf ----查看sw1上vrf交换机的IP路由信息
:9
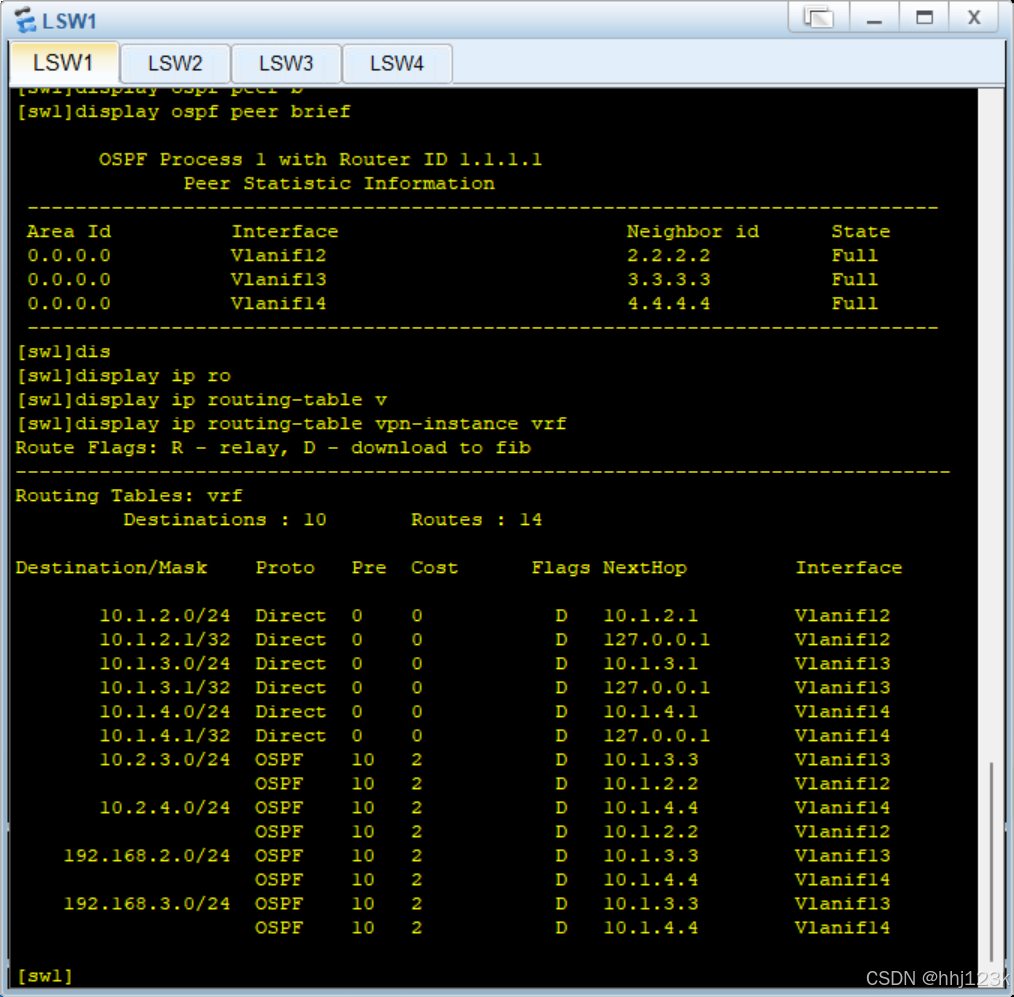
:10
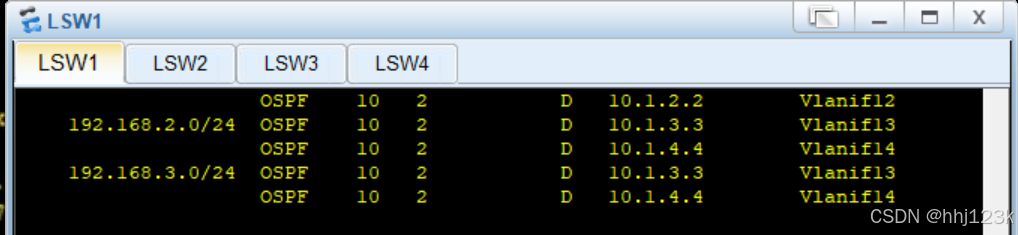
此时回程流量是等价路由,负载均衡,不符合来回路径一致要求。故需要进行路由干涉,使用路由
策略。
:6
SW3:
主要流量发送给SW1,备份发给SW2
SW4:
主要流量发送给SW2,备份发给SW1
SW1:
192.168.2.0/24--->主要发送给SW3,备份给SW4
192.168.3.0/24--->主要发送给SW4,备份给SW3
SW2:
192.168.2.0/24--->主要发送给SW3,备份给SW4
192.168.3.0/24--->主要发送给SW4,备份给SW3
W3和SW4只需要修改接口Cost数值,让SW3优选从SW1学习到的路由即可,让SW4优选从SW2学习到的路由。
sw3:
[sw3]interface Vlanif 23
[sw3-Vlanif23]ospf cost 5 -----因为原本的链路是千兆链路ospf过来开销值为1,将sw2-sw3的链路对于接口开销值改为5则192.168.2.0的信息优先选择开销值小的链路(sw1-sw3)
sw4:
[sw4]interface Vlanif 14
[sw4-Vlanif14]ospf cost 5
路由策略:
先把sw3和sw4在ospf中宣告的192.168.2.0和3.0取消宣告,因为一会会通过重发布来宣告
sw3:
[sw3-ospf-1-area-0.0.0.0]undo network 192.168.2.1 0.0.0.0
[sw3-ospf-1-area-0.0.0.0]undo network 192.168.3.1 0.0.0.0
sw4:
[sw4-ospf-1-area-0.0.0.0]undo network 192.168.2.2 0.0.0.0
[sw4-ospf-1-area-0.0.0.0]undo network 192.168.3.2 0.0.0.0
[sw1]display ip routing-table vpn-instance vrf ---在sw1上查看vrf路由信息
:11
:11
SW3:
将SW3本地发送的192.168.3.0/24路由的开销值改大
192.168.2.0/24路由开销不变
通过重发布,来调用路由策略
重发布时,不要引入其他路由信息
1、抓流量
[sw3]ip ip-prefix aa permit 192.168.3.0 24 ----抓取2.0和3.0流量
[sw3]ip ip-prefix bb permit 192.168.2.0 242、做策略
[sw3]route-policy aa permit node 10
[sw3-route-policy]if-match ip-prefix aa ---如果匹配抓取到的流量aa(3.0)
[sw3-route-policy]apply cost 5 ----开销值加5
[sw3]route-policy aa permit node 20
[sw3-route-policy]if-match ip-prefix bb----因为通过重发布,来调用路由策略
重发布时,不要引入其他路由信息 ,所以最后不要放通所有(防止有其他的路由信息)
3、调用
[sw3-ospf-1]import-route direct route-policy aaSW4:
将SW4本地发送的192.168.2.0/24路由的开销值改大
192.168.3.0/24路由开销不变
通过重发布,来调用路由策略
重发布时,不要引入其他路由信息
1、抓流量
[sw4]ip ip-prefix aa permit 192.168.2.0 24
[sw4]ip ip-prefix bb permit 192.168.3.0 242、做策略
[sw4]route-policy aa permit node 10
[sw4-route-policy]if-match ip-prefix aa
[sw4-route-policy]apply cost 5[sw4]route-policy aa permit node 20
[sw4-route-policy]if-match ip-prefix bb
3、调用
[sw4-ospf-1]import-route direct route-policy aa
查看vrrf路由表和ospf的lsdb表
[sw1]display ip routing-table vpn-instance vrf
[sw1]display ospf lsdb
:12

VRF交换机和防火墙的路由交互
拓扑:13
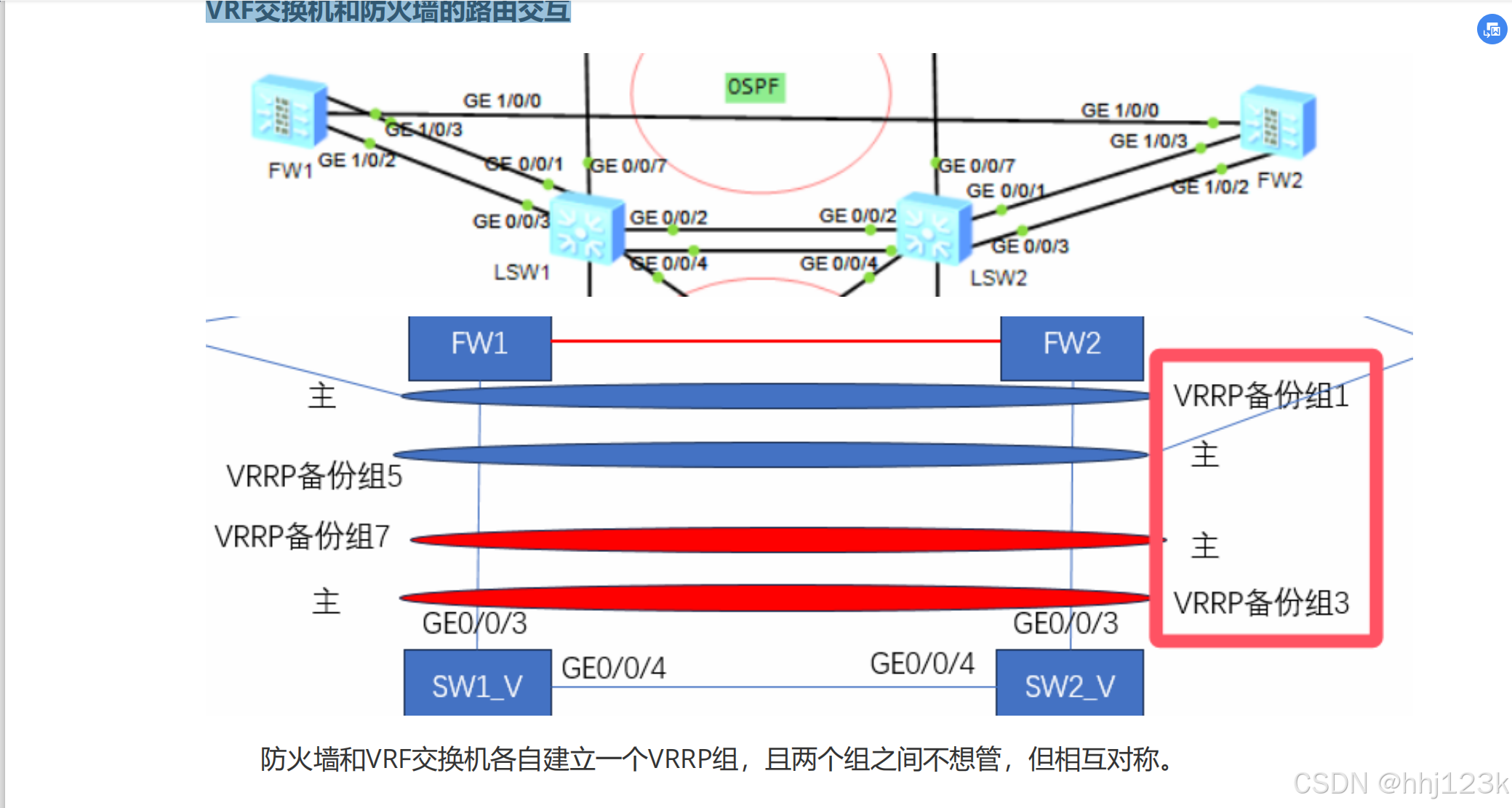
防火墙视角:
去往内部的流量,vFW路由的下一跳为交换机的VRRP备份组3的虚拟IP地址,当Master设备存在时,由
Master设备进行回复。
而当Master设备故障时,或者Master设备连接防火墙的链路故障时,VRF交换机会将Master角色进行
切换。而防火墙因为感知到接口down,也会进行主备切换。
接下来,就又备份防火墙进行数据发送,访问的下一跳还是VRRP备份组3的虚拟IP地址
VRF交换机视角:
如果流量正常来到Master设备上,将由Master设备进行路由查找,请求下一跳地址的信息,即VRRP备份
组1的虚拟IP地址,正常情况又Active设备回复
如果流量没有正常来到Master设备,即可能因为Master设备故障,那么此时不管是VRF交换机还是防火
墙都会进行主备切换。且流量还是正常转发。
如果Master路由器的下游设备链路故障,流量不得已到达Backup,但是此时Master设备还是存在的,
此时Backup设备无法通过三层转发机制转发流量,只能通过二层转发机制,将流量引导到Master设备上,此
时报文转发路径为Backup--->Master--->vFW
想要实现上述效果,需要让两台防火墙和虚拟出来的两台VRF交换机的数据转发路径同属于一个广
播域,即使用相同的VLAN和网段信息。**
拓扑:14
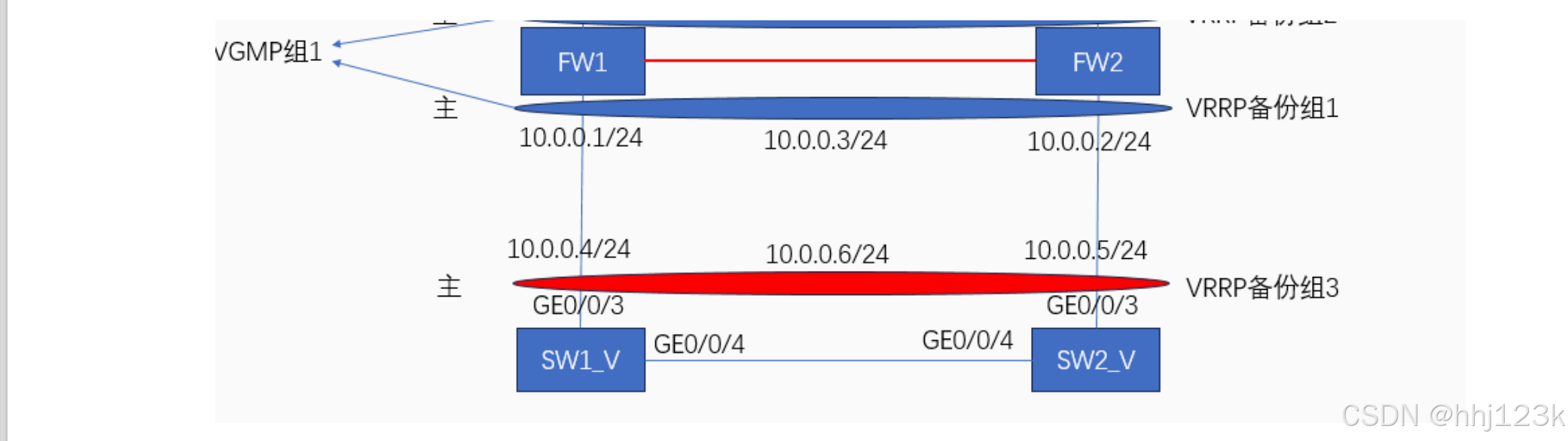
如果是负载分担组网形式,其逻辑是完全相同的,在每个设备上新添加一组VRRP信息。
下面可以参考图15:相当于把交换机变为两个交换机(vrf,poblic),然后防火墙在两个交换机中间
拓扑:15
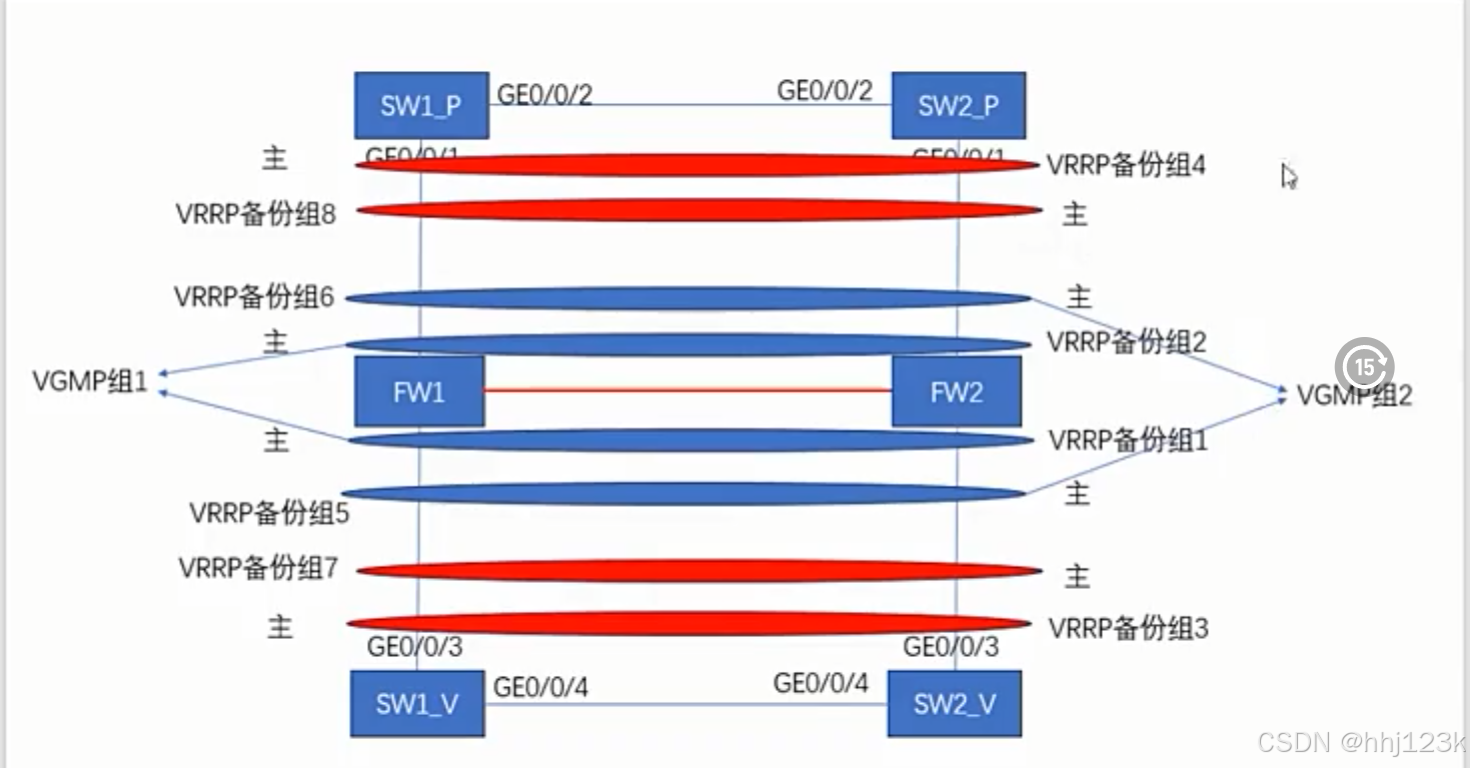
FW1为主
VRRP备份组1---VRRP备份组5
VRRP备份组3---VRRP备份组7
FW2为主
VRRP备份组2---VRRP备份组6
VRRP备份组4---VRRP备份组8
VRRP备份组1:VRF使用,SW1为Master,SW2为Backup
VLAN 41---10.4.1.0/24
SW1:10.4.1.1/24
SW2:10.4.1.2/24
虚拟地址:10.4.1.100
VRRP备份组2:VRF使用,SW2为Master,SW1为Backup
VLAN 42---10.4.2.0/24
SW1:10.4.2.1/24
SW2:10.4.2.2/24
虚拟地址:10.4.2.100
VRRP备份组3:Public使用,SW1为Master,SW2为Backup
VLAN 43---10.4.3.0/24
SW1:10.4.3.1/24
SW2:10.4.3.2/24
虚拟地址:10.4.3.100
VRRP备份组4:Public使用,SW2为Master,SW1为Backup
VLAN 44---10.4.4.0/24
SW1:10.4.4.1/24
SW2:10.4.4.2/24
虚拟地址:10.4.4.100
VRRP备份组5:防火墙使用,FW1为Master,FW2为BackupVLAN 41---10.4.1.0/24
FW1:10.4.1.10/24
FW2:10.4.1.20/24
虚拟地址:10.4.1.200
VRRP备份组6:防火墙使用,FW2为Master,FW1为BackupVLAN 42---10.4.2.0/24
FW1:10.4.2.10/24
FW2:10.4.2.20/24
虚拟地址:10.4.2.200
VRRP备份组7:防火墙使用,FW1为Master,FW2为Backup
VLAN 43---10.40.3.0/24
FW1:10.4.3.10/24
FW2:10.4.3.20/24
虚拟地址:10.40.3.200
VRRP备份组8:防火墙使用,FW2为Master,FW1为Backup
VLAN 44---10.4.4.0/24
FW1:10.4.4.10/24
FW2:10.4.4.20/24
虚拟地址:10.4.4.200
sw1:vrf:组1,2
[sw1]vlan batch 41 42 -----创建vlan
[sw1]interface GigabitEthernet 0/0/3 -----设置0/3和4口为trunk接口放通vlan41和42
[sw1-GigabitEthernet0/0/3]port link-type trunk
[sw1-GigabitEthernet0/0/3]port trunk allow-pass vlan 41 42[sw1-GigabitEthernet0/0/3]interface GigabitEthernet 0/0/4
[sw1-GigabitEthernet0/0/4]port link-type trunk
[sw1-GigabitEthernet0/0/4]port trunk allow-pass vlan 41 42备份组1:sw1为主----对于5
[sw1]interface Vlanif 41
[sw1-Vlanif41]ip binding vpn-instance vrf ----将vlanif41加入vrf交换机
[sw1-Vlanif41]ip address 10.4.1.1 24
[sw1-Vlanif41]vrrp vrid 1 virtual-ip 10.4.1.100 ---设置vrrp组的虚拟IP
[sw1-Vlanif41]vrrp vrid 1 priority 120 ----因为sw1是vrrp组1的master所以要设置优先级为120
[sw1-Vlanif41]vrrp vrid 1 preempt-mode timer delay 60 ---设置抢占延时和防火墙一样为60秒
[sw1-Vlanif41]vrrp vrid 1 track interface GigabitEthernet 0/0/3 reduced 30
---监控连接防火墙的接口0/0/3,当该接口故障了之后优先级降低30
备份组2:sw1为备----对应6
[sw1-Vlanif41]interface Vlanif 42
[sw1-Vlanif42]ip binding vpn-instance vrf
[sw1-Vlanif42]ip address 10.4.2.1 24
---这里sw1作为组2的备所以只要配置虚拟IP[sw1]ip route-static vpn-instance vrf 0.0.0.0 0 10.4.1.200 ---sw1向上的缺省路由,指向fw1
[sw1]ip route-static vpn-instance vrf 0.0.0.0 0 10.4.2.200 preference 70 ---备用指向fw2[sw1]ip route-static 192.168.0.0 16 10.4.3.200 ---pobilc向下指向sw1
[sw1]ip route-static 192.168.0.0 16 10.4.4.200 preference 70[sw1-ospf-1]default-route-advertise ----sw1下放缺省路由
sw2:vrf:组1,2
[sw2]vlan batch 41 42
[sw2]interface GigabitEthernet 0/0/4
[sw2-GigabitEthernet0/0/4]port link-type trunk
[sw2-GigabitEthernet0/0/4]port trunk allow-pass vlan 41 42[sw2-GigabitEthernet0/0/4]interface GigabitEthernet 0/0/3
[sw2-GigabitEthernet0/0/3]port link-type trunk
[sw2-GigabitEthernet0/0/3]port trunk allow-pass vlan 41 42
备份组1:sw2为备----对应5
[sw2]interface Vlanif 41
[sw2-Vlanif41]ip binding vpn-instance vrf
[sw2-Vlanif41]ip address 10.4.1.2 24
[sw2-Vlanif41]vrrp vrid 1 virtual-ip 10.4.1.100
备份组2:sw2为主---对应6
[sw2-Vlanif41]interface Vlanif 42
[sw2-Vlanif42]ip binding vpn-instance vrf
[sw2-Vlanif42]ip address 10.4.2.2 24
[sw2-Vlanif42]vrrp vrid 2 virtual-ip 10.4.2.100
[sw2-Vlanif42]vrrp vrid 2 priority 120
[sw2-Vlanif42]vrrp vrid 2 preempt-mode timer delay 60
[sw2-Vlanif42]vrrp vrid 2 track interface GigabitEthernet 0/0/3 reduced 30[sw2]ip route-static vpn-instance vrf 0.0.0.0 0 10.4.2.200 ---主要指向fw2
[sw2]ip route-static vpn-instance vrf 0.0.0.0 0 10.4.1.200 preference 70[sw2]ip route-static 192.168.0.0 16 10.4.3.200 preference 70
[sw2]ip route-static 192.168.0.0 16 10.4.4.200 ---主要[sw2-ospf-1]default-route-advertise
sw1:poblic:组3,4
[sw1]vlan batch 43 44
[sw1]interface GigabitEthernet 0/0/1
[sw1-GigabitEthernet0/0/1]port link-type trunk
[sw1-GigabitEthernet0/0/1]port trunk allow-pass vlan 43 4[sw1-GigabitEthernet0/0/1]interface GigabitEthernet 0/0/2
[sw1-GigabitEthernet0/0/2]port link-type trunk
[sw1-GigabitEthernet0/0/2]port trunk allow-pass vlan 43 44
备份组3:sw1为主----对应7
[sw1]interface Vlanif 43
[sw1-Vlanif43]ip address 10.4.3.1 24
[sw1-Vlanif43]vrrp vrid 3 virtual-ip 10.4.3.100
[sw1-Vlanif43]vrrp vrid 3 priority 120
[sw1-Vlanif43]vrrp vrid 3 preempt-mode timer delay 60
[sw1-Vlanif43]vrrp vrid 3 track interface GigabitEthernet 0/0/1 reduced 30
备份组4:sw1为备----对应8
[sw1]interface Vlanif 44
[sw1-Vlanif44]ip address 10.4.4.1 24
[sw1-Vlanif44]vrrp vrid 4 virtual-ip 10.4.4.100
sw2:poblic:组3,4
[sw2]vlan batch 43 44
[sw2]interface GigabitEthernet 0/0/1
[sw2-GigabitEthernet0/0/1]port link-type trunk
[sw2-GigabitEthernet0/0/1]port trunk allow-pass vlan 43 44[sw2-GigabitEthernet0/0/1]interface GigabitEthernet 0/0/2
[sw2-GigabitEthernet0/0/2]port link-type trunk
[sw2-GigabitEthernet0/0/2]port trunk allow-pass vlan 43 44备份组3:sw2为备----对应7
[sw2]interface Vlanif 43
[sw2-Vlanif43]ip address 10.4.3.2 24
[sw2-Vlanif43]vrrp vrid 3 virtual-ip 10.4.3.100备份组4:sw2为主----对应8
[sw2]interface Vlanif 44
[sw2-Vlanif44]ip address 10.4.4.2 24
[sw2-Vlanif44]vrrp vrid 4 virtual-ip 10.4.4.100
[sw2-Vlanif44]vrrp vrid 4 priority 120
[sw2-Vlanif44]vrrp vrid 4 preempt-mode timer delay 60
[sw2-Vlanif44]vrrp vrid 4 track interface GigabitEthernet 0/0/1 reduced 30
fw1和2:(激活1/0/2和3)(给接口配置IP在删除)(每次打开拓扑都要补配一次来激活接口)
HRP_M[fw1]interface GigabitEthernet 1/0/2 (+B)
HRP_M[fw1-GigabitEthernet1/0/2]ip address 1.1.1.1 24
HRP_M[fw1-GigabitEthernet1/0/2]undo ip addressHRP_M[fw1-GigabitEthernet1/0/2]interface GigabitEthernet 1/0/3 (+B)
HRP_M[fw1-GigabitEthernet1/0/3]ip address 2.2.2.2 24
HRP_M[fw1-GigabitEthernet1/0/3]undo ip addressHRP_S[fw2]interface GigabitEthernet 1/0/2
HRP_S[fw2-GigabitEthernet1/0/2]ip address 3.3.3.3 24
HRP_S[fw2-GigabitEthernet1/0/2]undo ip addressHRP_S[fw2-GigabitEthernet1/0/2]interface GigabitEthernet 1/0/3
HRP_S[fw2-GigabitEthernet1/0/3]ip address 3.3.3.3 24
HRP_S[fw2-GigabitEthernet1/0/3]undo ip address
fw1:组5,6,7,8
vlan和接口配置
[fw1]vlan batch 41 42 43 44
[fw1]interface GigabitEthernet 1/0/0 ---1/0/0作为与fw2之间的心跳线的心跳口
[fw1-GigabitEthernet1/0/0]ip address 10.10.10.1 24
将1/0/2分为2.41,2.42两个子接口对应组5,6
[fw1]interface GigabitEthernet 1/0/2.41
[fw1-GigabitEthernet1/0/2.41]ip address 10.4.1.10 24
[fw1-GigabitEthernet1/0/2.41]vlan-type dot1q 41[fw1-GigabitEthernet1/0/2.41]interface GigabitEthernet 1/0/2.42
[fw1-GigabitEthernet1/0/2.42]ip address 10.4.2.10 24
[fw1-GigabitEthernet1/0/2.42]vlan-type dot1q 42
将1/0/3分为3.43,3.44两个子接口对应组7,8
[fw1-GigabitEthernet1/0/2.42]interface GigabitEthernet 1/0/3.43
[fw1-GigabitEthernet1/0/3.43]ip address 10.4.3.10 24
[fw1-GigabitEthernet1/0/3.43]vlan-type dot1q 43
[fw1-GigabitEthernet1/0/2.42]interface GigabitEthernet 1/0/3.44
[fw1-GigabitEthernet1/0/3.44]ip address 10.4.4.10 24
[fw1-GigabitEthernet1/0/3.44]vlan-type dot1q 44
划分安全区域:
fw1与fw2之间dmz
fw1与vrf交换机为trust
fw1与poblic交换机为trust[fw1]firewall zone dmz
[fw1-zone-dmz]add interface GigabitEthernet 1/0/0
[fw1]firewall zone trust
[fw1-zone-trust]add interface GigabitEthernet 1/0/2.41
[fw1-zone-trust]add interface GigabitEthernet 1/0/2.42
[fw1]firewall zone untrust
[fw1-zone-untrust]add interface GigabitEthernet 1/0/3.43
[fw1-zone-untrust]add interface GigabitEthernet 1/0/3.44
防火墙双机热备配置:
----------------------------下联VRF--------------------------
VRRP备份组5:防火墙使用,FW1为Master,FW2为Backup
[fw1]interface GigabitEthernet 1/0/2.41
[fw1-GigabitEthernet1/0/2.41]vrrp vrid 5 virtual-ip 10.4.1.200 activeVRRP备份组6:防火墙使用,FW2为Master,FW1为Backup
[fw1-GigabitEthernet1/0/2.41]interface GigabitEthernet 1/0/2.42
[fw1-GigabitEthernet1/0/2.42]vrrp vrid 6 virtual-ip 10.4.2.200 standby----------------------------上联Public--------------------------
VRRP备份组7:防火墙使用,FW1为Master,FW2为Backup
[fw1-GigabitEthernet1/0/2.42]interface GigabitEthernet 1/0/3.43
[fw1-GigabitEthernet1/0/3.43]vrrp vrid 7 virtual-ip 10.4.3.200 activeVRRP备份组8:防火墙使用,FW2为Master,FW1为Backup
[fw1-GigabitEthernet1/0/3.43]interface GigabitEthernet 1/0/3.44
[fw1-GigabitEthernet1/0/3.44]vrrp vrid 8 virtual-ip 10.4.4.200 standbyhrp心跳线配置;
[FW1]hrp mirror session enable ---快速备份功能
[FW1]hrp interface GigabitEthernet 1/0/0 remote 10.10.10.2 ---定义心跳线和对端IP
[FW1]hrp enable
向上的缺省路由配置:(指向poblic交换机的)
HRP_M[fw1]ip route-static 0.0.0.0 0 10.4.3.100
HRP_M[fw1]ip route-static 0.0.0.0 0 10.4.4.100 preference 70 ---主要去往sw1的poblic(因为在备份组3中sw1为主),所以要修改只想sw2的poblic的优先级,防止等价路由向下的缺省路由配置:(指向vrf交换机的)
HRP_M[fw1]ip route-static 192.168.0.0 16 192.168.1.100 ----在备份组1中sw1为主
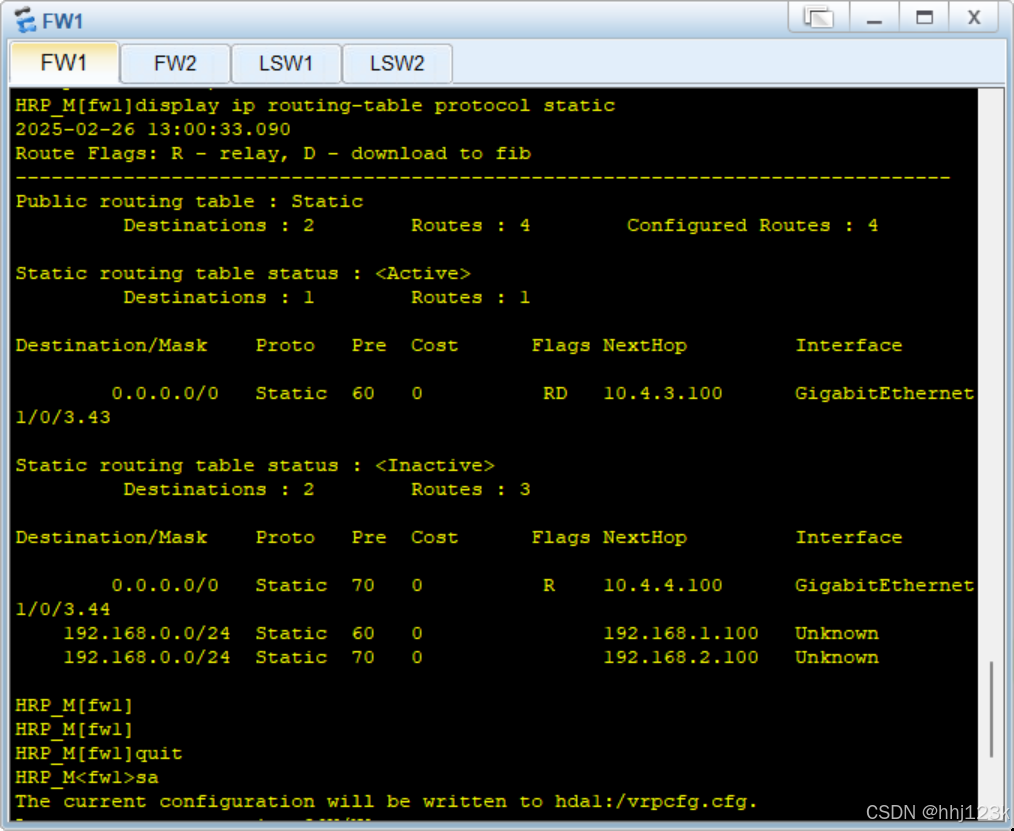
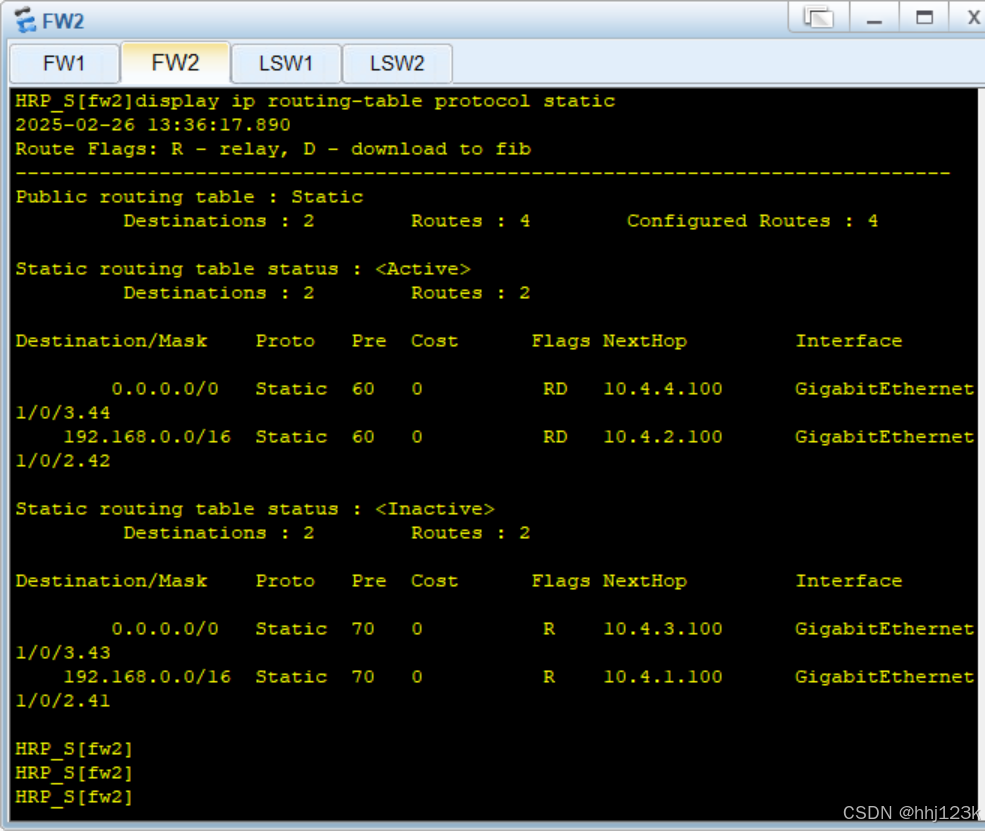
HRP_M[fw1]ip route-static 192.168.0.0 16 192.168.2.100 preference 70HRP_M[fw1]display ip routing-table protocol static ---查看静
:16
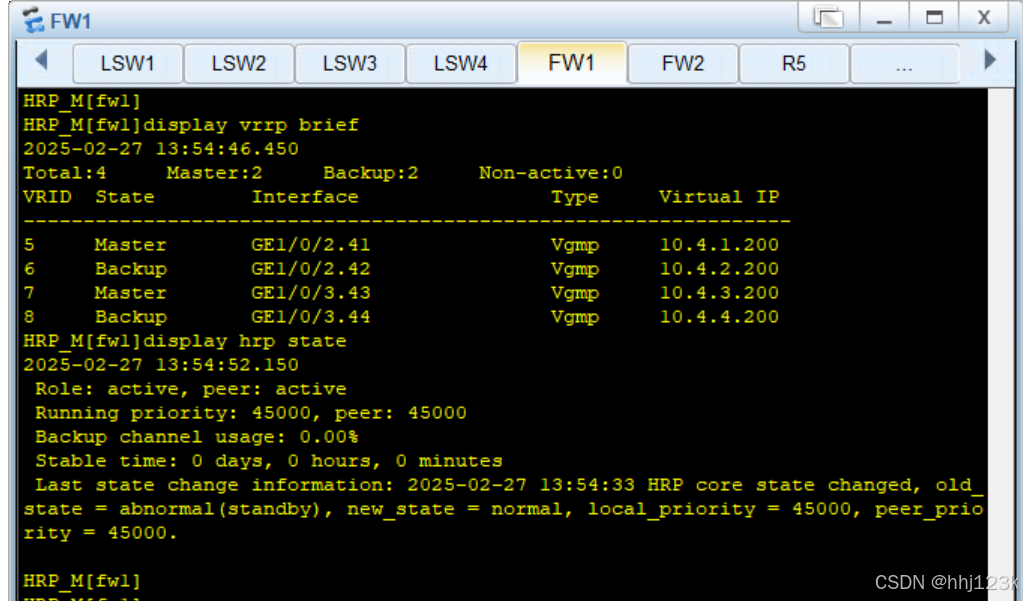
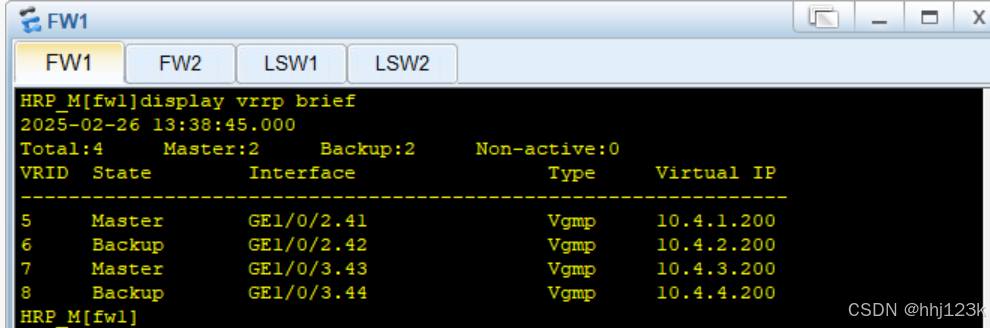
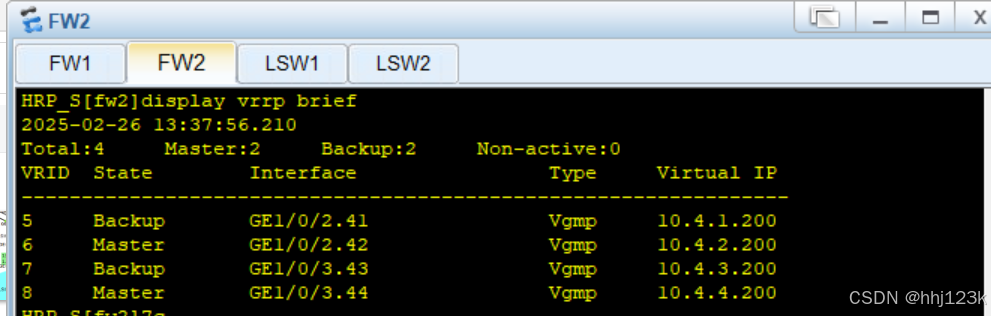
HRP_S[fw2]display vrrp brief ---查看vgmp组信息
:18
:18
安全策略:
HRP_M[fw1]security-policy (+B)
HRP_M[fw1-policy-security]rule name 1 (+B) ---从trust 到 untrust
HRP_M[fw1-policy-security-rule-1]source-zone trust (+B) ---源区域
HRP_M[fw1-policy-security-rule-1]destination-zone untrust (+B) --目的区域
HRP_M[fw1-policy-security-rule-1]source-address 192.168.0.0 16 (+B) ---源ip,目的为any不写
HRP_M[fw1-policy-security-rule-1]action permit (+B) ---动作允许然后主设备(fw1)会把安全策略同步给备设备(fw2),可以在sw2上查看
fw2:组5,6,7,8
vlan和接口配置
[fw2]vlan batch 41 to 44
[fw2]interface GigabitEthernet 1/0/0
[fw2-GigabitEthernet1/0/0]ip address 10.10.10.2 24将1/0/2分为2.41,2.42两个子接口对应组5,6
[fw2]interface GigabitEthernet 1/0/2.41
[fw2-GigabitEthernet1/0/2.41]ip address 10.4.1.20 24
[fw2-GigabitEthernet1/0/2.41]vlan-type dot1q 41[fw2-GigabitEthernet1/0/2.41]interface GigabitEthernet 1/0/2.42
[fw2-GigabitEthernet1/0/2.42]ip address 10.4.2.20 24
[fw2-GigabitEthernet1/0/2.42]vlan-type dot1q 42
将1/0/3分为3.43,3.44两个子接口对应组7,8
[fw2-GigabitEthernet1/0/2.42]interface GigabitEthernet 1/0/3.43
[fw2-GigabitEthernet1/0/3.43]ip address 10.4.3.20 24
[fw2-GigabitEthernet1/0/3.43]vlan-type dot1q 43[fw2-GigabitEthernet1/0/3.43]interface GigabitEthernet 1/0/3.44
[fw2-GigabitEthernet1/0/3.44]ip address 10.4.4.20 24
[fw2-GigabitEthernet1/0/3.44]vlan-type dot1q 44
划分安全区域:
[fw2]firewall zone dmz
[fw2-zone-dmz]add interface GigabitEthernet 1/0/0
[fw2]firewall zone trust
[fw2-zone-trust]add interface GigabitEthernet 1/0/2.41
[fw2-zone-trust]add interface GigabitEthernet 1/0/2.42[fw2]firewall zone untrust
[fw2-zone-untrust]add interface GigabitEthernet 1/0/3.43
[fw2-zone-untrust]add interface GigabitEthernet 1/0/3.44防火墙双机热备配置:
----------------------------下联VRF--------------------------
VRRP备份组5:防火墙使用,FW1为Master,FW2为Backup
[fw2]interface GigabitEthernet 1/0/2.41
[fw2-GigabitEthernet1/0/2.41]vrrp vrid 5 virtual-ip 10.4.1.200 standbyVRRP备份组6:防火墙使用,FW2为Master,FW1为Backup
[fw2]interface GigabitEthernet 1/0/2.42
[fw2-GigabitEthernet1/0/2.42]vrrp vrid 6 virtual-ip 10.4.2.200 active
----------------------------上联Public--------------------------
VRRP备份组7:防火墙使用,FW1为Master,FW2为Backup
[fw2]interface GigabitEthernet 1/0/3.43
[fw2-GigabitEthernet1/0/3.43]vrrp vrid 7 virtual-ip 10.4.3.200 standby
VRRP备份组8:防火墙使用,FW2为Master,FW1为Backup
[fw2]interface GigabitEthernet 1/0/3.44
[fw2-GigabitEthernet1/0/3.44]vrrp vrid 8 virtual-ip 10.4.4.200 activehrp配置:
[fw2]hrp mirror session enable
[fw2]hrp interface GigabitEthernet 1/0/0 remote 10.10.10.1
[fw2]hrp enable
向上的缺省路由配置:(指向poblic交换机的)
HRP_S[fw2]ip route-static 0.0.0.0 0 10.4.3.100 preference 70
HRP_S[fw2]ip route-static 0.0.0.0 0 10.4.4.100向下的静态路由配置:(指向vrf交换机的)
这里配指向192.168.0.0/16是为了方便直接包括(2.0和3.0)
HRP_S[fw2]ip route-static 192.168.0.0 16 10.4.1.100 preference 70
HRP_S[fw2]ip route-static 192.168.0.0 16 10.4.2.100
HRP_S[fw2]display ip routing-table protocol static ---查看静态路由表
:17
:17
HRP_S[fw2]display vrrp brief ---查看vgmp组信息
:19
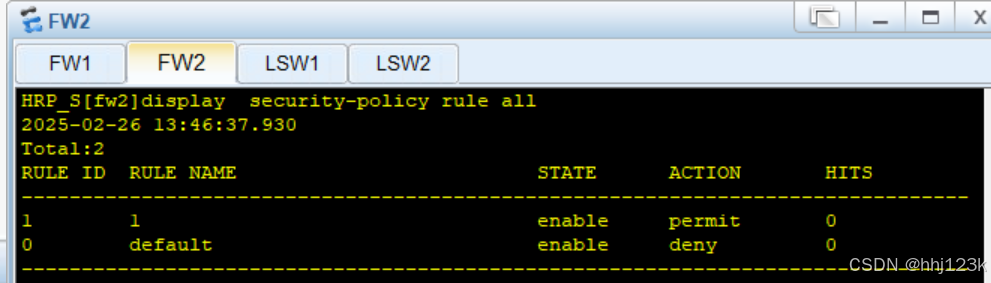
HRP_S[fw2]display security-policy rule all ---查看sw2上的安全策略
:20
核心到边界
ospf(上面那个sw1,2的poblic和路由器5,6):
SW1-SW2:VLAN 102 --- 10.12.0.0/24
SW1-R5:VLAN 105 ---- 10.15.0.0/24
SW2-R6:VLAN 206 ---- 10.26.0.0/24
R5-R6: ---- 10.56.0.0/24
sw1(poblic):
vlan和接口配置:[sw1]vlan batch 102 105
[sw1]interface GigabitEthernet 0/0/7
[sw1-GigabitEthernet0/0/7]port link-type access
[sw1-GigabitEthernet0/0/7]port default vlan 105
[sw1-GigabitEthernet0/0/7]undo stp enable[sw1]interface GigabitEthernet 0/0/2 ---之前已经配置过trunk,只要继续添加即可
[sw1-GigabitEthernet0/0/2]port trunk allow-pass vlan 102 105
[sw1-GigabitEthernet0/0/2]undo stp enable[sw1]interface Vlanif 102
[sw1-Vlanif102]ip address 10.12.0.1 24[sw1-Vlanif102]interface Vlanif 105
[sw1-Vlanif105]ip address 10.15.0.1 24
ospf2配置;
这里用进程号2来和vrf进行区分
[sw1]ospf 2 router-id 1.1.1.1
[sw1-ospf-2]area 0
[sw1-ospf-2-area-0.0.0.0]network 10.12.0.1 0.0.0.0
[sw1-ospf-2-area-0.0.0.0]network 10.15.0.1 0.0.0.0
sw2(poblic):
vlan和接口配置:
[sw2]vlan batch 102 206
[sw2]interface GigabitEthernet 0/0/7
[sw2-GigabitEthernet0/0/7]port link-type access
[sw2-GigabitEthernet0/0/7]port default vlan 206
[sw2-GigabitEthernet0/0/7]undo stp enable[sw2]interface GigabitEthernet 0/0/2
[sw2-GigabitEthernet0/0/2]port trunk allow-pass vlan 102 206
[sw2-GigabitEthernet0/0/2]undo stp enable[sw2]interface Vlanif 102
[sw2-Vlanif102]ip address 10.12.0.2 24[sw2-Vlanif102]interface Vlanif 206
[sw2-Vlanif206]ip address 10.26.0.2 24ospf2配置:
[sw2]ospf 2 router-id 2.2.2.2
[sw2-ospf-2]area 0
[sw2-ospf-2-area-0.0.0.0]network 10.12.0.2 0.0.0.0
[sw2-ospf-2-area-0.0.0.0]network 10.26.0.2 0.0.0.0
r5:
接口配置:
[r5]interface GigabitEthernet 0/0/0
[r5-GigabitEthernet0/0/0]ip address 10.15.0.5 24[r5-GigabitEthernet0/0/0]interface GigabitEthernet 0/0/1
[r5-GigabitEthernet0/0/1]ip address 10.56.0.5 24ospf1配置:
[r5]ospf 1 router-id 5.5.5.5
[r5-ospf-1]area 0
[r5-ospf-1-area-0.0.0.0]network 10.15.0.5 0.0.0.0
[r5-ospf-1-area-0.0.0.0]network 10.56.0.5 0.0.0.0
r6:
接口配置:
[r6]interface GigabitEthernet 0/0/0
[r6-GigabitEthernet0/0/0]ip address 10.26.0.6 24[r6-GigabitEthernet0/0/0]interface GigabitEthernet 0/0/1
[r6-GigabitEthernet0/0/1]ip address 10.56.0.6 24ospf1配置:
[r6]ospf 1 router-id 6.6.6.6
[r6-ospf-1]area 0
[r6-ospf-1-area-0.0.0.0]network 10.26.0.6 0.0.0.0
[r6-ospf-1-area-0.0.0.0]network 10.56.0.6 0.0.0.0
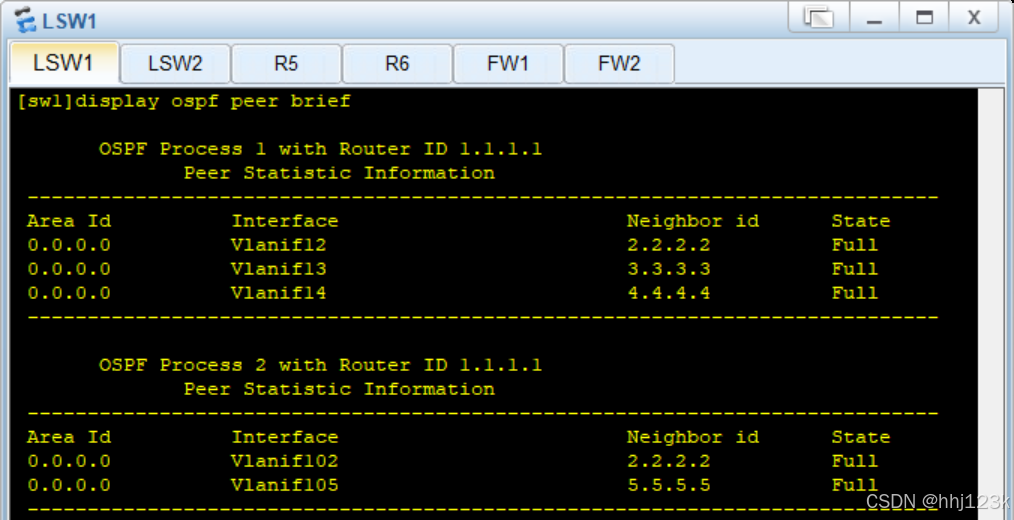
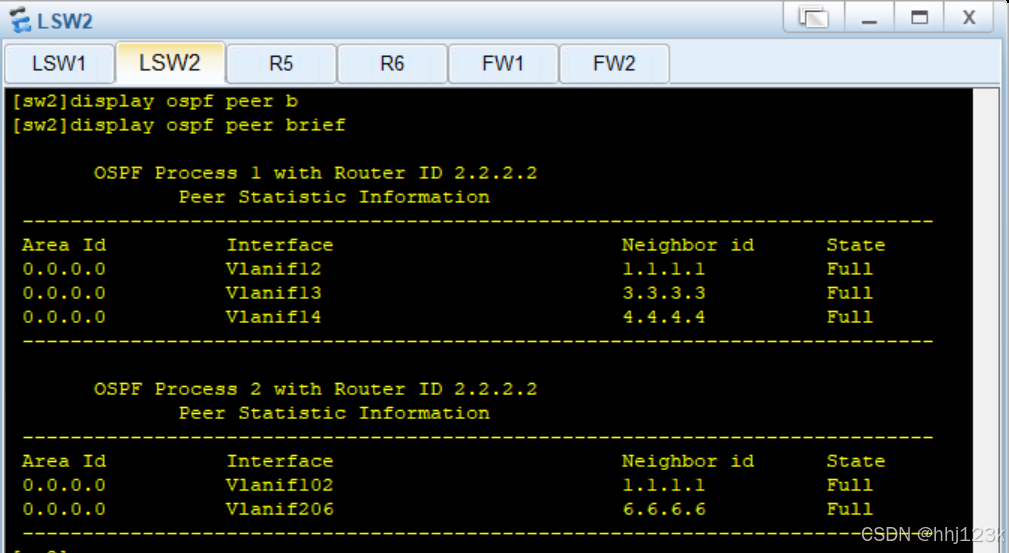
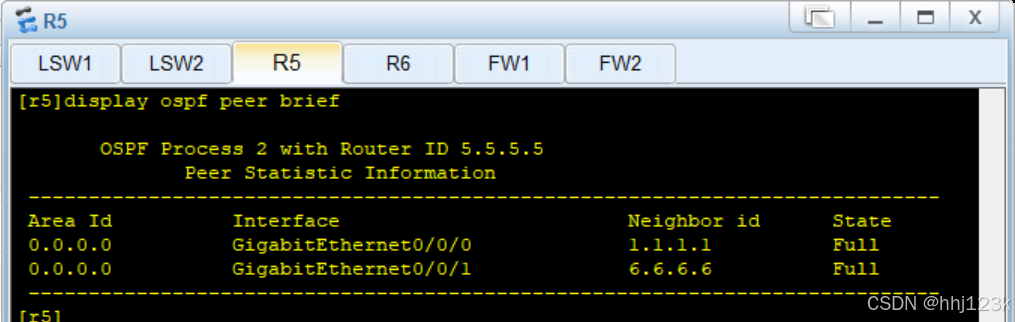
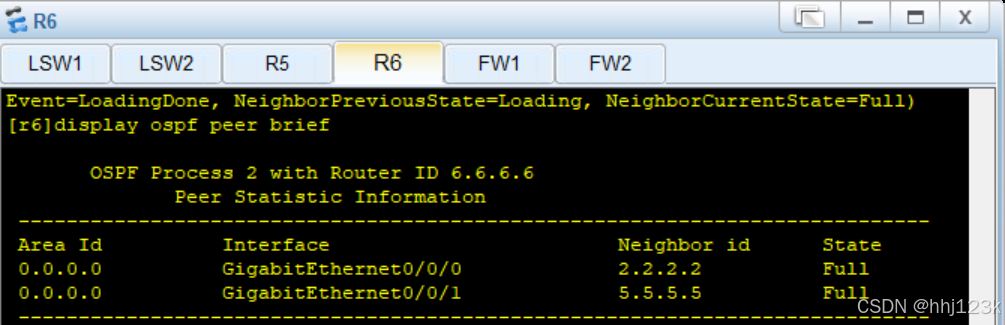
[sw1]display ospf peer brief ----查看ospf邻居表
:21,22,23,24
缺省
路由配置:(指向isp)
r5:
[r5]interface GigabitEthernet 0/0/2
[r5-GigabitEthernet0/0/2]ip address 12.0.0.5 24
[r5]ip route-static 0.0.0.0 0 12.0.0.100 ---缺省路由
[r5]ospf 1
[r5-ospf-2]default-route-advertise ----下放缺省路由[r5]acl 2000
[r5-acl-basic-2000]rule permit source 192.168.0.0 0.0.255.255 ---抓取流量[r5]interface GigabitEthernet 0/0/2
[r5-GigabitEthernet0/0/2]nat outbound 2000 ----nat配置
r6:
[r6]interface GigabitEthernet 0/0/2
[r6-GigabitEthernet0/0/2]ip address 13.0.0.6 24
[r6]ip route-static 0.0.0.0 0 13.0.0.100
[r6]ospf 1
[r6-ospf-2]default-route-advertise
[r6]acl 2000
[r6-acl-basic-2000]rule permit source 192.168.0.0 0.0.255.255
[r6]interface GigabitEthernet 0/0/2
[r6-GigabitEthernet0/0/2]nat outbound 2000
isp:
[isp100]interface GigabitEthernet0/0/0
[isp100-GigabitEthernet0/0/0]ip address 12.0.0.100 24[isp100-GigabitEthernet0/0/0]interface GigabitEthernet0/0/1
[isp100-GigabitEthernet0/0/1]ip address 13.0.0.100 24[isp100]interface LoopBack 0
[isp100-LoopBack0]ip address 100.1.1.1 24
sw3,4:
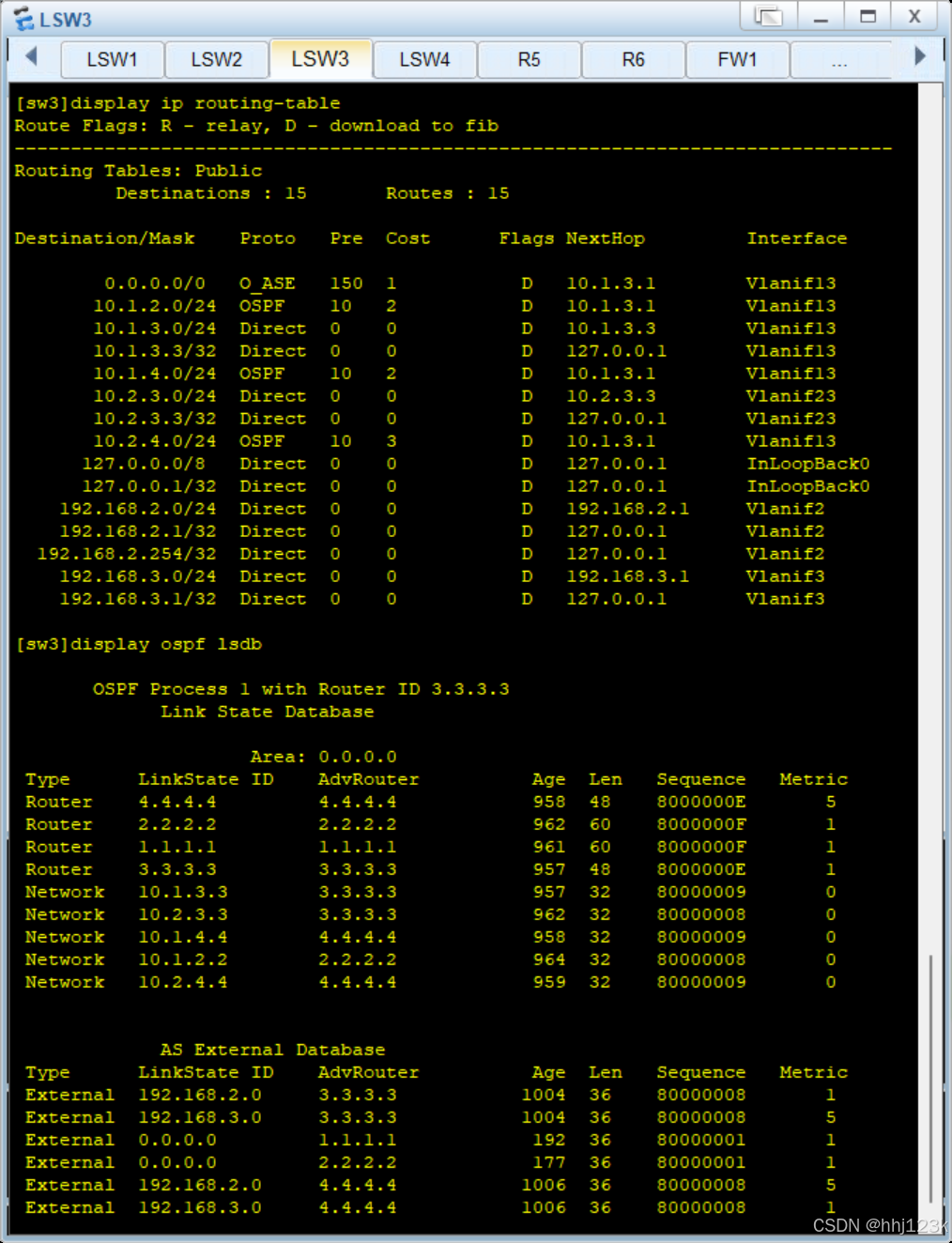
[sw3]display ip routing-table --查看路由表
[sw3]display ospf lsdb --查看lsdb表
:25,26
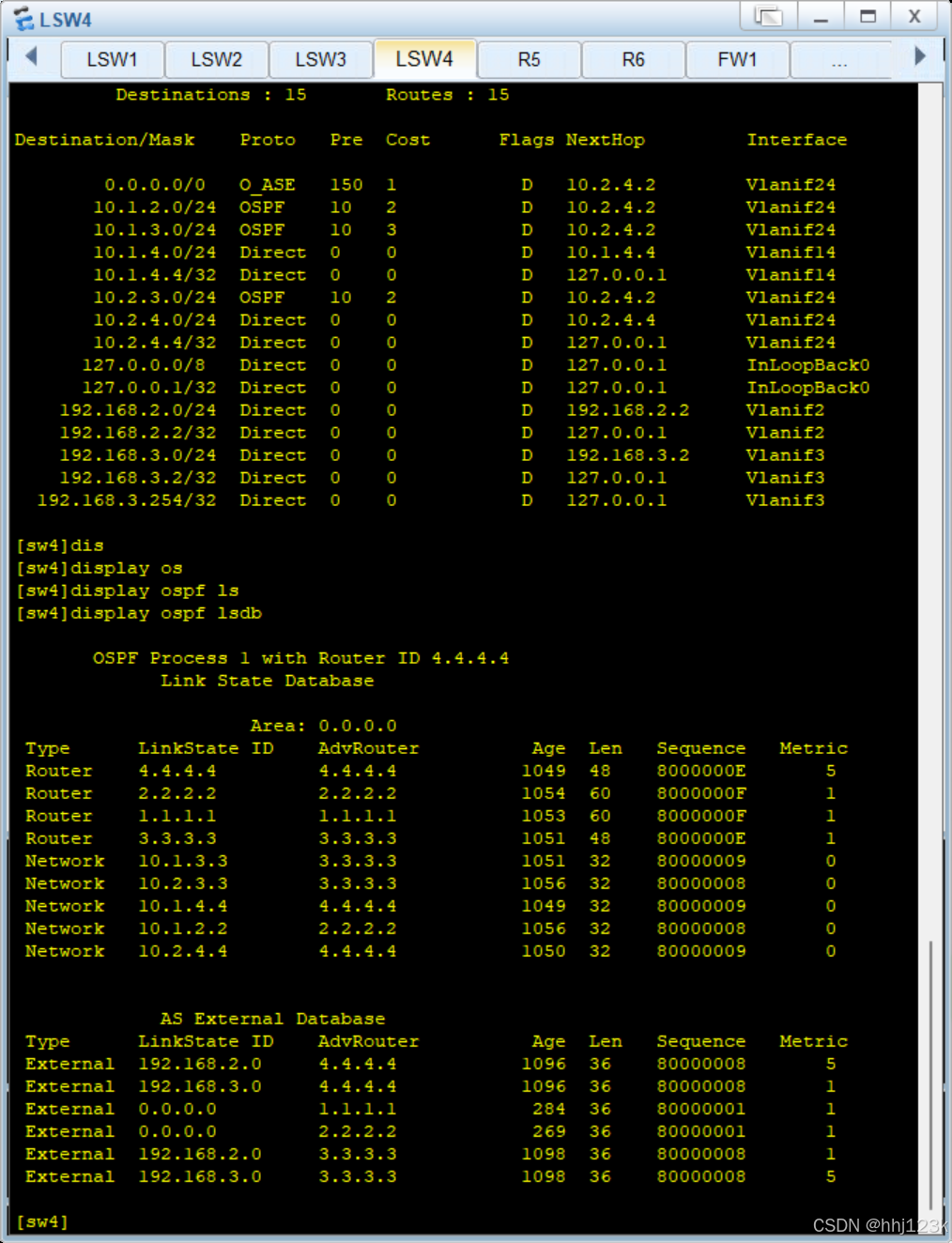
sw1,2:
[sw1]display ip routing-table vpn-instance vrf
:27,28将sw1上poblic上去往192.168.2.0和3.0的静态路由重发表给r5,6,防止r5,6因为没有回程路由丢弃来自2.0和3.0的信息
[sw1-ospf-2]import-route static
[sw2-ospf-2]import-route static
测试;
192.168.2.1-100.1.1.1
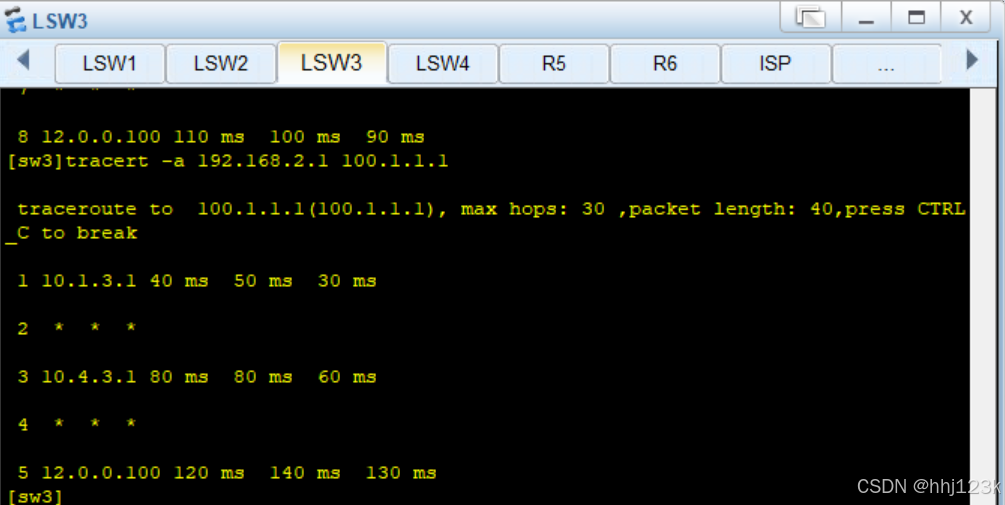
[sw3]tracert -a 192.168.2.1 100.1.1.1
去往10.4.3.1是sw1的poblic
12.0.0.100 120是路由器isp
说明可以到达
:29
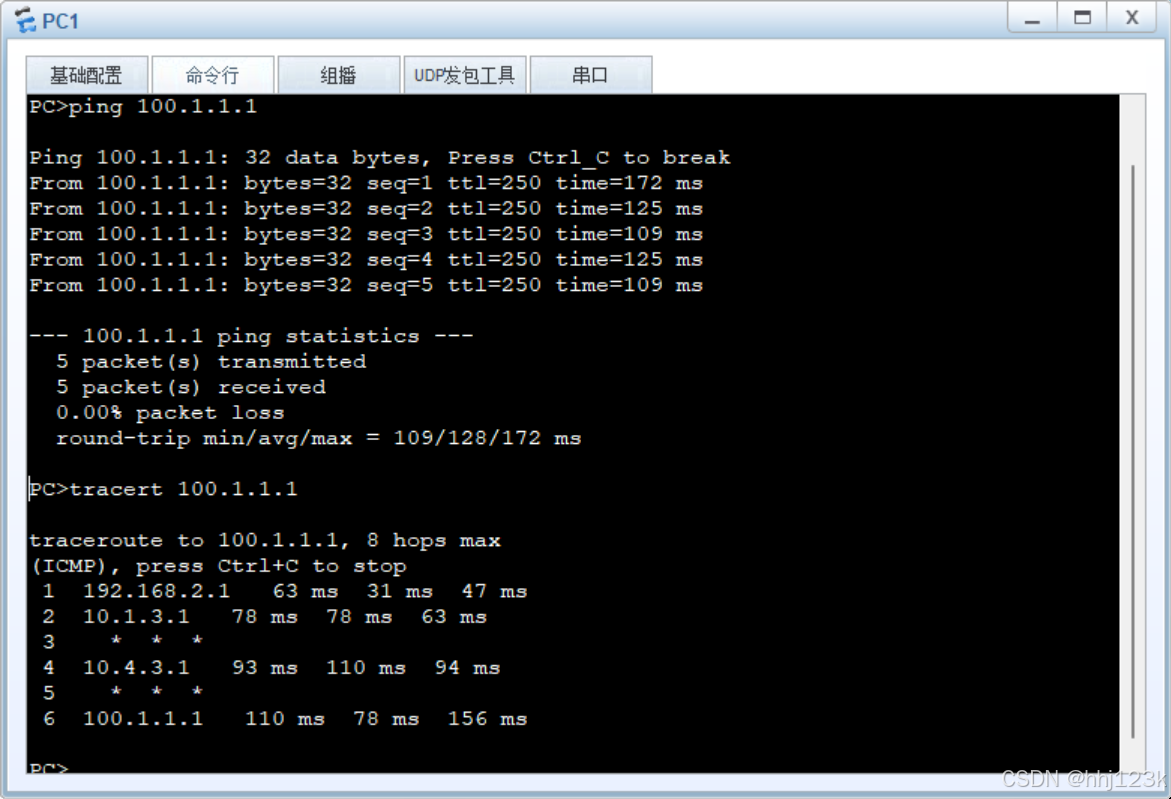
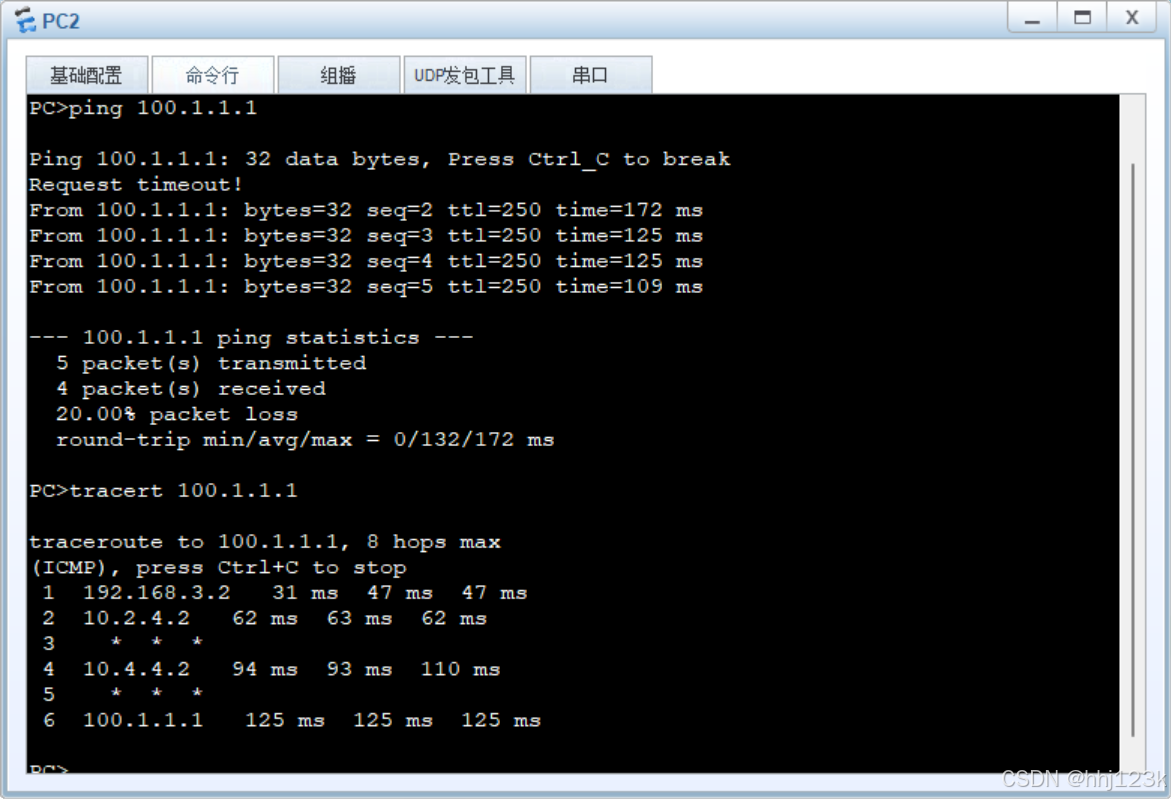
用pc1和2来测100.1.1.1
PC>ping 100.1.1.1
PC>tracert 100.1.1.1---可以看到从pc1到isp的路径
pc1-sw3-sw1的vrf-fw1(不回)-sw1的poblic-r5(边界路由器,不回)-isp
:30.31
关闭sw1上的某个接口看pc1是否可以继续ping通100.1.1.1
PC>ping 100.1.1.1 -t ---长ping100.1.1.1
然后关闭sw1的vrf的0/0/1接口
[sw1-GigabitEthernet0/0/1]shutdown没断还在继续
:32

[sw1]display vrrp brief
:33
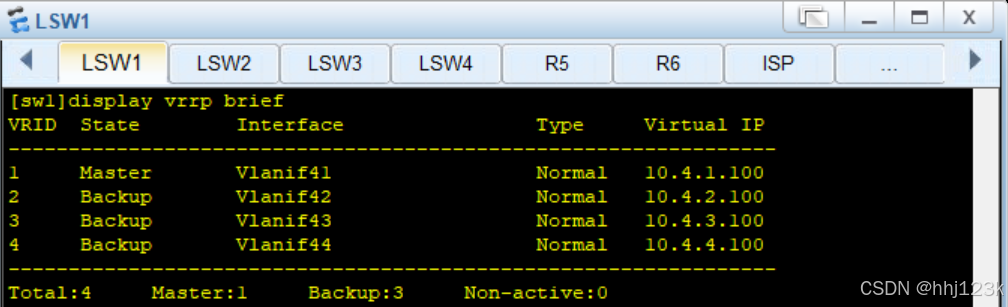
HRP_S[fw1]display vrrp brief
:34
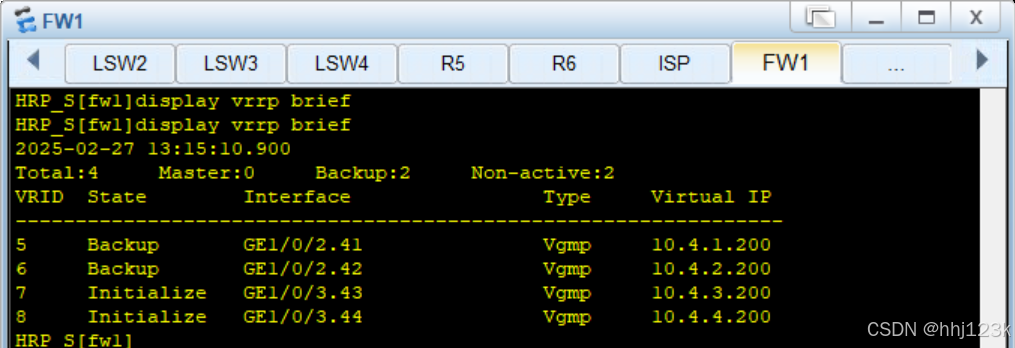
HRP_M[fw2]display vrrp brief
:35
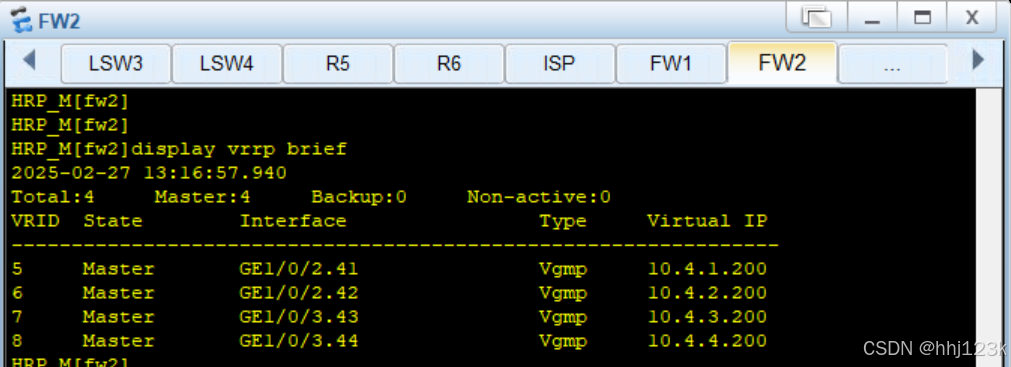
[SW2]display vrrp brief
:36
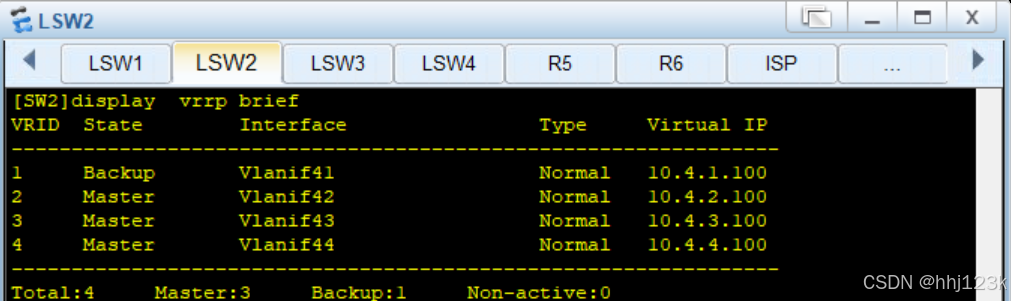
HRP_M[fw2]display hrp state ---查看现在的fw2vgmp状态
:37
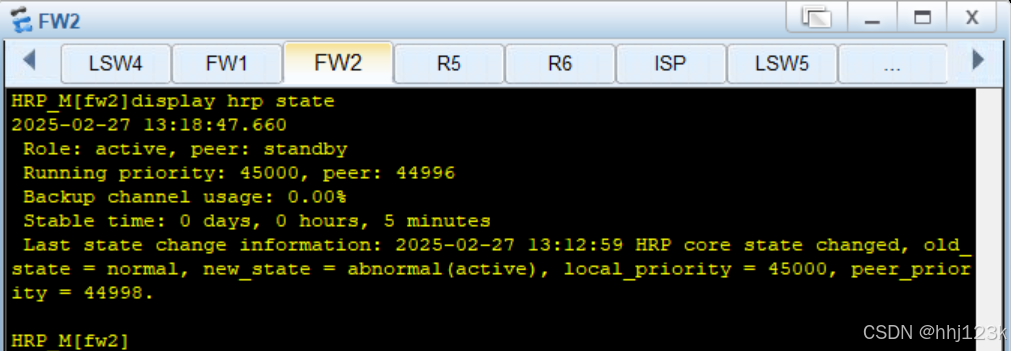
这边的peer为44996是因为在这个接口上有两个vrrp组,一个vrrp是减2,两个就是减4将sw1的vrf0/0/1接口恢复
[sw1-GigabitEthernet0/0/1]undo shutdownHRP_S[fw2]display hrp state
:39
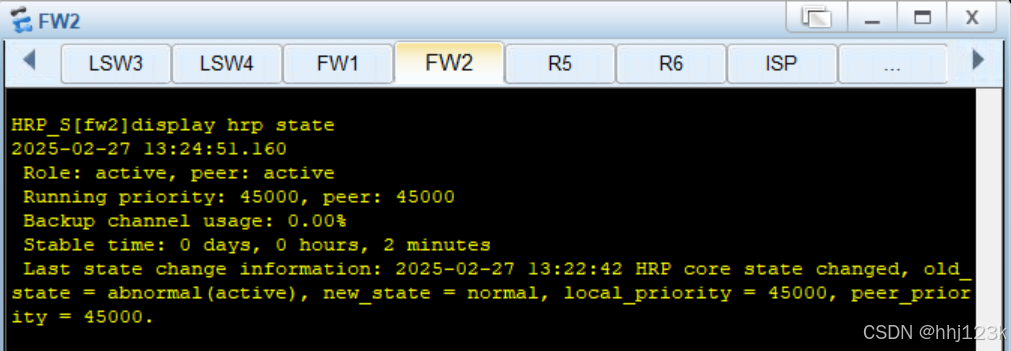
然后发现sw1对应fw1的接口有反了,因为拓扑上的接口好显示错了位置,所以要将vlanif41,43两个active的vgmp组的监控接口反过来
拓扑修改后:47
在sw1进行修改
[sw1-Vlanif41]undo vrrp vrid 1 track interface GigabitEthernet
[sw1-Vlanif41]vrrp vrid 1 track interface GigabitEthernet 0/0/1 reduced 30
[sw1-Vlanif43]undo vrrp vrid 3 track interface GigabitEthernet
[sw1-Vlanif43]vrrp vrid 3 track interface GigabitEthernet 0/0/3 reduced 30
用pc2做测试关闭sw2的0/0/3口,这里sw2没有配错
PC>ping 100.1.1.1 -t ---长ping100.1.1.1
[SW2]interface GigabitEthernet 0/0/3
[SW2-GigabitEthernet0/0/3]shutdown[SW2]display vrrp brief
:40
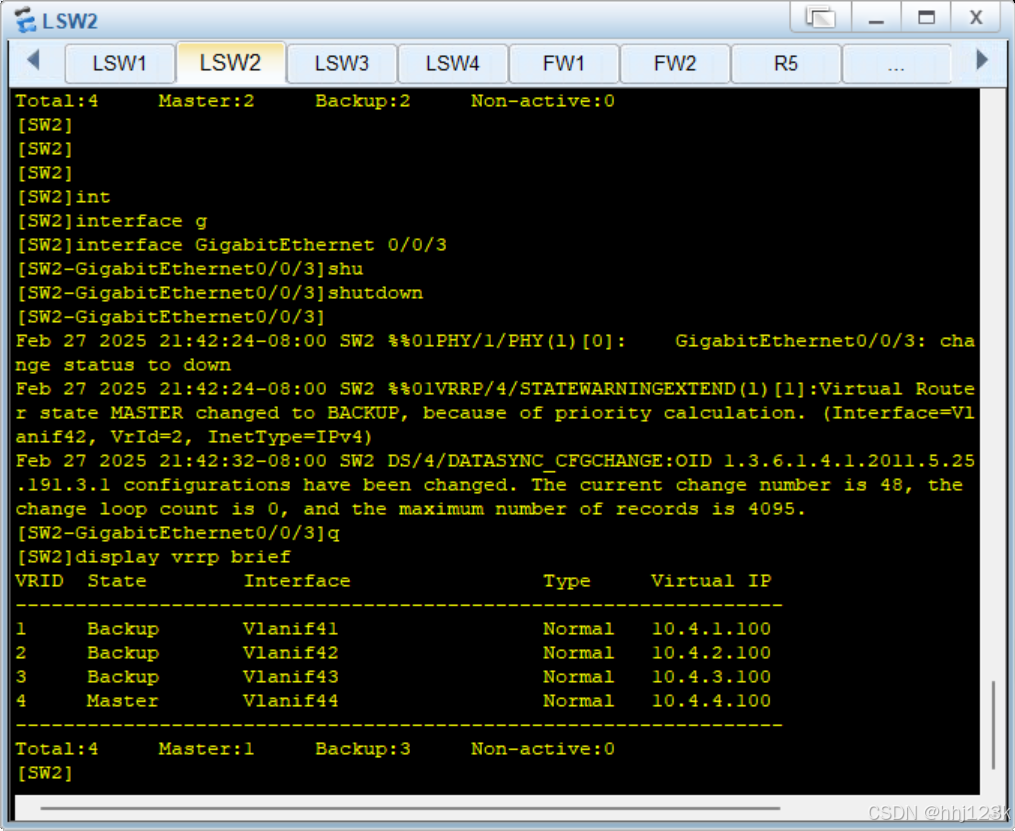
HRP_S[fw2]display vrrp brief
HRP_S[fw2]display hrp state
:41
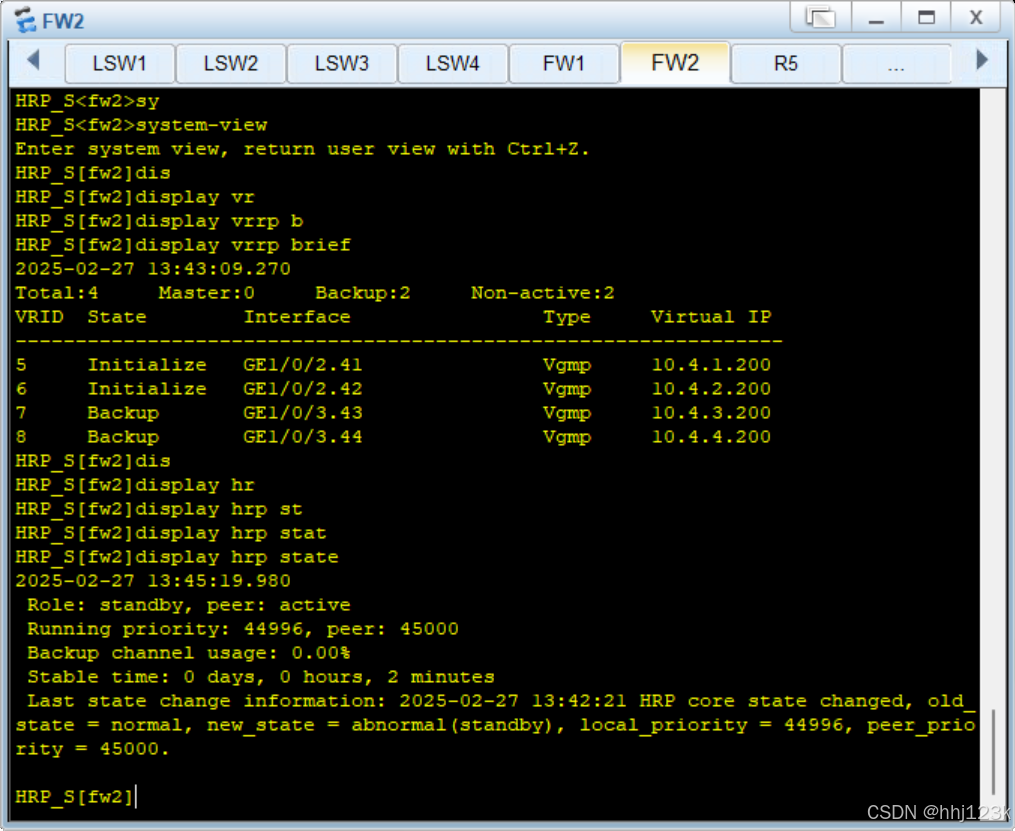
关闭fw1上的1/0/2.41子接口
HRP_M[fw1-GigabitEthernet1/0/2.41]shutdown
HRP_S[fw1]display vrrp brief
:42
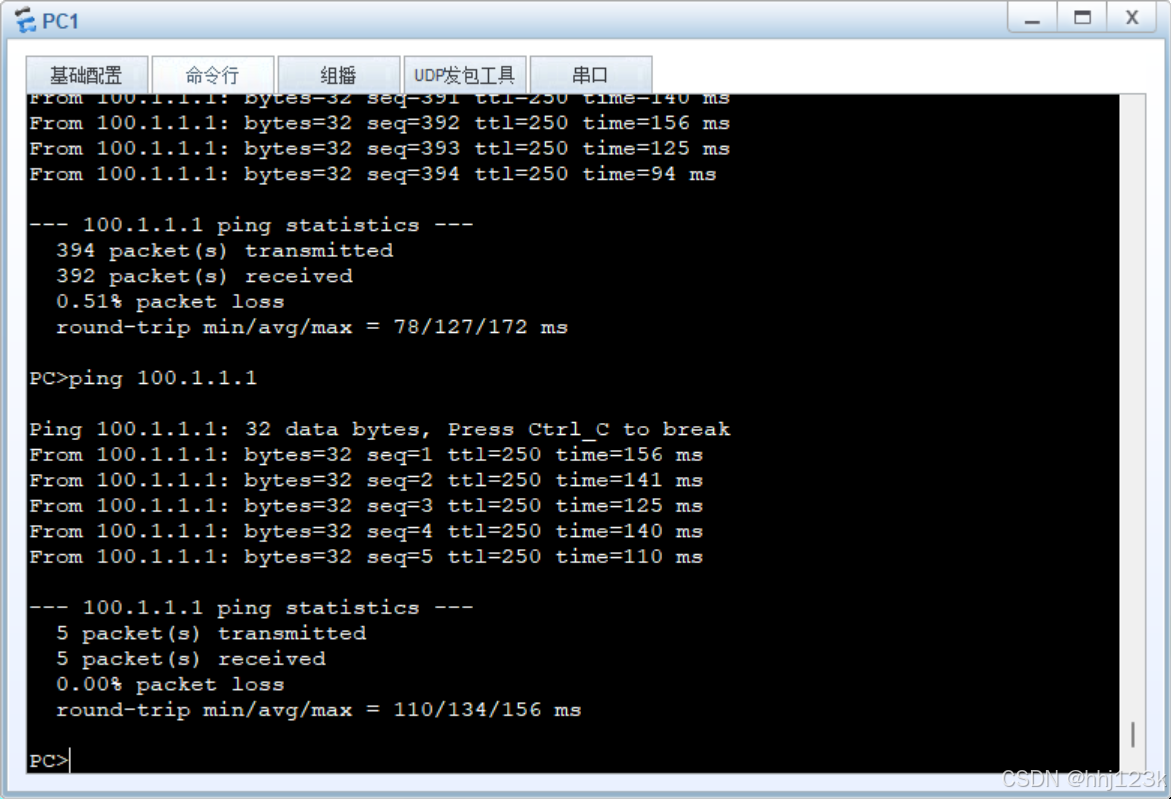
HRP_S[fw1]display hrp state
:43
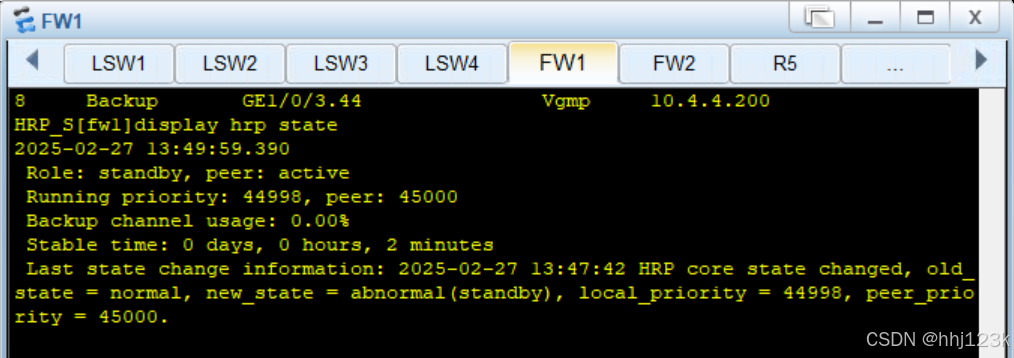
HRP_M[fw2]display vrrp brief
HRP_M[fw2]display hrp state
:44
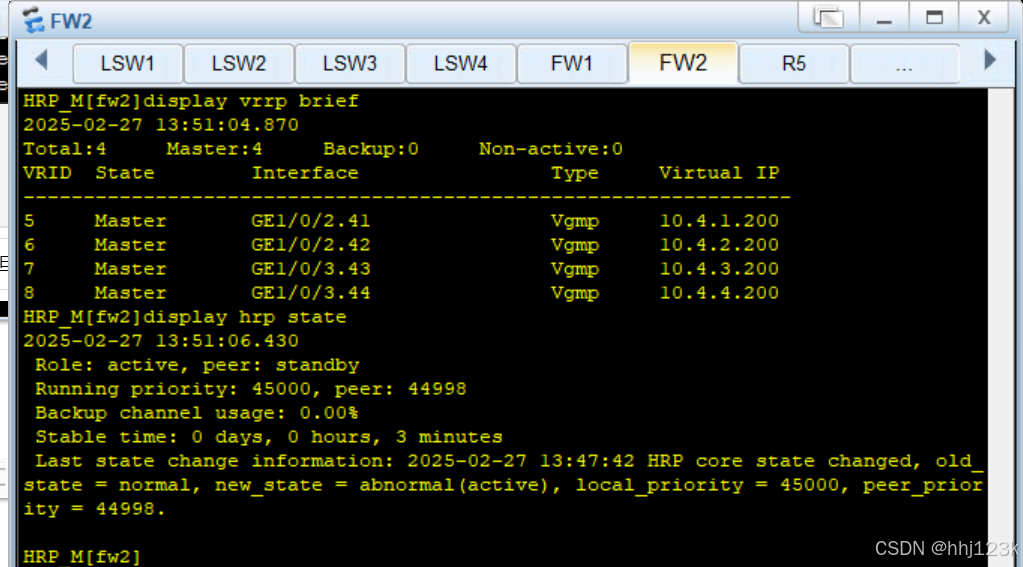
pc1长ping100.1.1.1
:45
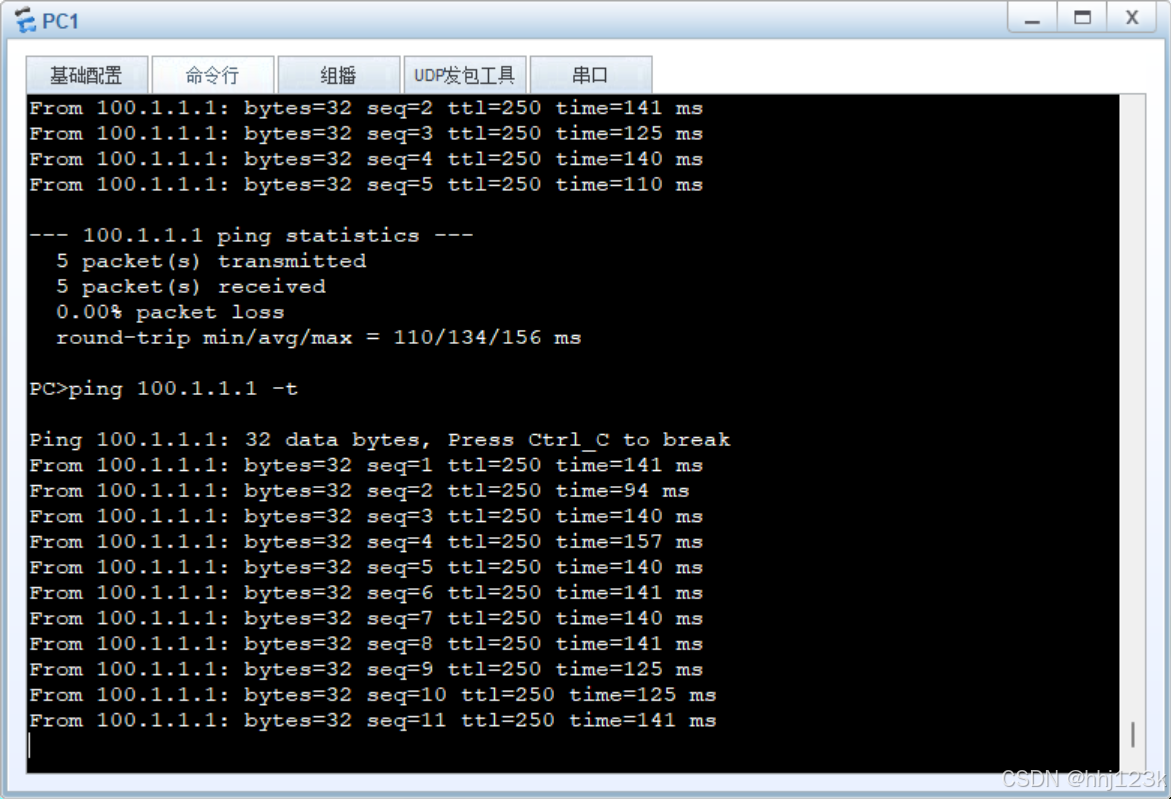
HRP_S[fw1-GigabitEthernet1/0/2.41]undo shutdown ----恢复1/0/2.41子接口HRP_M[fw1]display vrrp brief
HRP_M[fw1]display hrp state
:46