GaussDB 数据库架构师修炼(十三)安全管理(3)-行级访问控制
1 背景
行级访问控制特性将数据库的访问控制精确到数据表行级别 ,只允许用户查看 、更新或删除特定的行数据。
2 实例场景
实例以医生只能看到治疗的病人,不能看其它医生的病人为例:
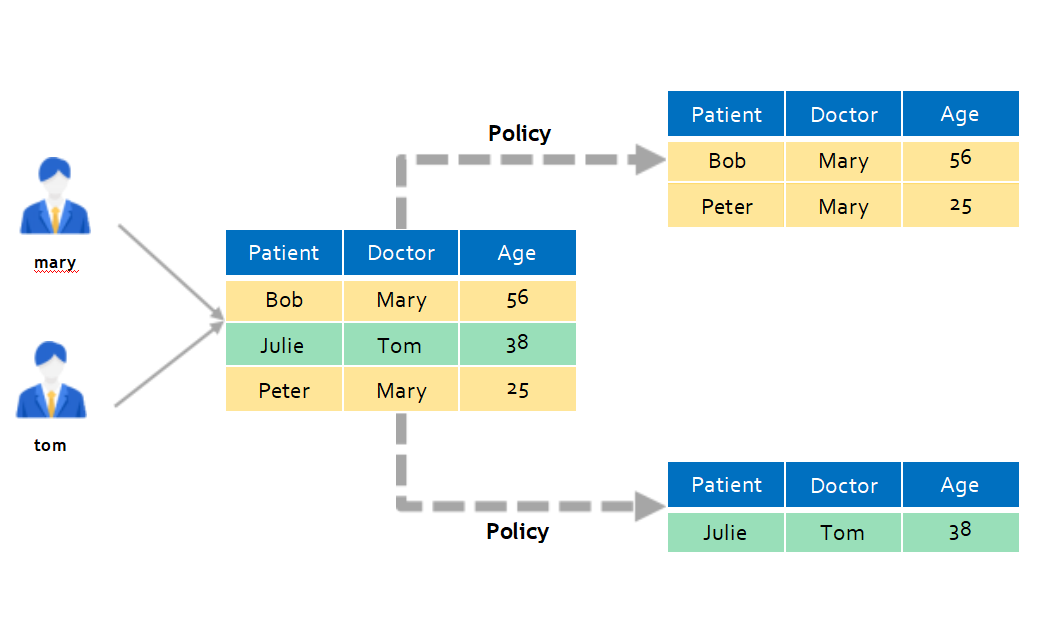
1)医院病人的信息表pat_info:
csdn=> set search_path=csdn;
SET
csdn=>
csdn=> create table pat_info(patient varchar2(64),doctor varchar2(64),age int);
CREATE TABLE
csdn=> insert into pat_info(patient,doctor,age)values('peter','mary',25),('bob','mary',56),('julie','tom',38);
INSERT 0 3
csdn=>
csdn=> select * from pat_info;patient | doctor | age
---------+--------+-----peter | mary | 25bob | mary | 56julie | tom | 38
(3 rows)csdn=>
2) 创建行级访问控制策略 ,使得医生只能查看属于自己的病 人信息 ,并打开表上的行级访问控制开关:
csdn=> CREATE ROW LEVEL SECURITY POLICY rl_select ON
csdn-> pat_info FOR select USING(doctor=current_user);
CREATE ROW LEVEL SECURITY POLICY
csdn=> alter table pat_info enable row level security;
ALTER TABLE
csdn=>
csdn=> \d+ pat_info;Table "csdn.pat_info"Column | Type | Modifiers | Storage | Stats target | Description
---------+-----------------------+-----------+----------+--------------+-------------patient | character varying(64) | | extended | |doctor | character varying(64) | | extended | |age | integer | | plain | |
Row Level Security Policies:POLICY "rl_select" FOR SELECTTO publicUSING (((doctor)::name = "current_user"()))
Has OIDs: no
Options: orientation=row, compression=no, storage_type=USTORE, segment=off, enable_rowsecurity=truecsdn=>
3) 创建两个用户tom,mary并授予usage与select权限;
[Ruby@dtest1 ~]$ gsql -h 192.168.0.71 -dcsdn -p8000 -U root -W '*******' -ar
gsql ((GaussDB Kernel 505.2.1 build 159cea95) compiled at 2024-12-27 09:22:44 commit 10161 last mr 21504 release)
SSL connection (cipher: ECDHE-RSA-AES128-GCM-SHA256, bits: 128)
Type "help" for help.csdn=>
csdn=>csdn=> create user mary password '*******';
CREATE ROLE
csdn=> create user tom password '*******';
CREATE ROLE
csdn=> grant usage on schema csdn to mary;
GRANT
csdn=> grant usage on schema csdn to tom;
GRANT
csdn=> grant select on csdn.pat_info to tom;
GRANT
csdn=> grant select on csdn.pat_info to mary;
GRANT
csdn=> \q
4)验证一下tom、mary用户查询结果
mary只能看到peter、bob两个病人。
[Ruby@dtest1 ~]$ gsql -h 192.168.0.71 -dcsdn -p8000 -U mary -W '******' -ar
gsql ((GaussDB Kernel 505.2.1 build 159cea95) compiled at 2024-12-27 09:22:44 commit 10161 last mr 21504 release)
SSL connection (cipher: ECDHE-RSA-AES128-GCM-SHA256, bits: 128)
Type "help" for help.csdn=> set search_path=csdn;
SET
csdn=> select * from pat_info;patient | doctor | age
---------+--------+-----peter | mary | 25bob | mary | 56
(2 rows)csdn=> \q
tom只能看到julie
[Ruby@dtest1 ~]$ gsql -h 192.168.0.71 -dcsdn -p8000 -U tom -W '*****' -ar
gsql ((GaussDB Kernel 505.2.1 build 159cea95) compiled at 2024-12-27 09:22:44 commit 10161 last mr 21504 release)
SSL connection (cipher: ECDHE-RSA-AES128-GCM-SHA256, bits: 128)
Type "help" for help.csdn=> set search_path=csdn;
SET
csdn=> select * from pat_info;patient | doctor | age
---------+--------+-----julie | tom | 38
(1 row)csdn=>
3 行级别安全实现原理
1)行级访问控制的目的是控制表中行级数据可见性,通过在数据表上预定义Filter,在查询优化阶段将满足条件 的表达式应用到执行计划上,影响最终的执行结果。
2)当前受影响的SQL语句包括SELECT, UPDATE, DELETE 。
3)用户可以在数据表创建行访问控制( Row Level Security)策略,当数据库用户对数据表访问时,若SQL满足 数据表特定的RLS策略,在查询优化阶段将满足条件的表达式,按照属性( PERMISSIVE | RESTRICTIVE)类 型,通过OR或AND方式拼接,应用到执行计划上。
4 实现操作步骤
步骤1:打开行访问控制策略开关:
ALTER TABLE tablename ENABLE ROW LEVEL SECURITY;步骤2:创建行访问控制策略,当前用户只能查看用户自身的数据:
CREATE ROW LEVEL SECURITY POLICY tablename_rls ON tablename USING(role = CURRENT_USER);注意:tablename为所创建的表名, tablename_rls为创建的行级访问控制策略名。
