防御保护第三次练习
一、实验拓扑

二、实验要求
完成基础配置,配置真实DNS服务信息,创建虚拟服务,配置DNS透明代理功能并进行合理需求的补充
三、需求分析
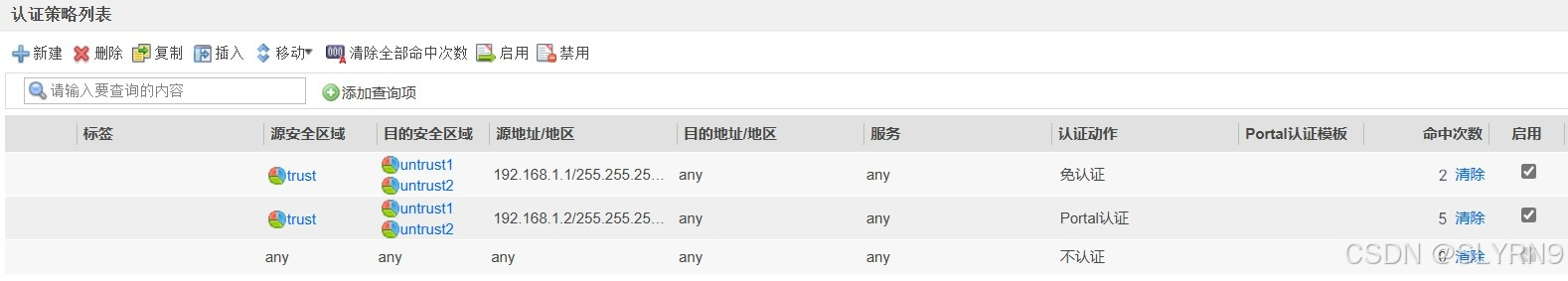
1.创建用户并进行认证策略
2.安全策略划分接口
3.ip与策略配置(为增强熟练度倾向使用代码配置)包括安全策略,nat策略,透明dns等
四、实验步骤
1.划分安全策略接口
[FW]firewall zone name untrust1
[FW-zone-untrust1]add int g1/0/1
[FW]firewall zone trust
[FW-zone-trust]add interface GigabitEthernet 1/0/0
[FW]firewall zone untrust1
[FW-zone-untrust1]set priority 10
[FW]firewall zone name untrust2
[FW-zone-untrust2]set priority 15
[FW-zone-untrust2]add int g1/0/2
2.创建用户并进行策略认证

分免认证与portal认证

3.路由ip
[FW]int g 1/0/0
[FW-GigabitEthernet1/0/0]ip add 192.168.1.254 24
[FW-GigabitEthernet1/0/0]int g 1/0/1
[FW-GigabitEthernet1/0/1]ip add 11.0.0.1 24
[FW-GigabitEthernet1/0/1]int g 1/0/2
[FW-GigabitEthernet1/0/2]ip add 12.0.0.1 24
[r1]int g 0/0/0
[r1-GigabitEthernet0/0/0]ip add 11.0.0.2 24
[r1-GigabitEthernet0/0/0]int g 0/0/1
[r1-GigabitEthernet0/0/1]ip add 100.1.1.254 24
[r1-GigabitEthernet0/0/1]int g 0/0/2
[r1-GigabitEthernet0/0/2]ip add 110.1.1.254 24
[r2]int g 0/0/0
[r2-GigabitEthernet0/0/0]ip add 12.0.0.2 24
[r2-GigabitEthernet0/0/0]int g 0/0/1
[r2-GigabitEthernet0/0/1]ip add 210.1.1.254 24
[r2-GigabitEthernet0/0/1]int g 0/0/2
[r2-GigabitEthernet0/0/2]ip add 200.1.1.254 24
4.配置安全策略
[FW]security-policy
[FW-policy-security]rule name dns
[FW-policy-security-rule-dns]source-zone trust
[FW-policy-security-rule-dns]destination-zone untrust1 untrust2
[FW-policy-security-rule-dns]source-address 192.168.1.0 mask 255.255.255.0
[FW-policy-security-rule-dns]action permit
[FW-policy-security-rule-dns]rule name web
[FW-policy-security-rule-web]source-zone trust
[FW-policy-security-rule-web]destination-zone untrust1 untrust2
[FW-policy-security-rule-web]source-address 192.168.1.0 mask 255.255.255.0
[FW-policy-security-rule-web]action permit

5.NAT配置
[FW]nat address-group nat_1
[FW-address-group-nat_1]section 11.0.0.10 11.0.0.10
[FW-address-group-nat_1]mode pat
[FW-address-group-nat_1]route enable
[FW-address-group-nat_1]nat address-group nat_2
[FW-address-group-nat_2]section 12.0.0.10 12.0.0.10
[FW-address-group-nat_2]mode pat
[FW-address-group-nat_2]route enable
[FW-address-group-nat_2]nat-policy
[FW-policy-nat]rule name policy_1
[FW-policy-nat-rule-policy_1]source-zone trust
[FW-policy-nat-rule-policy_1]destination-zone untrust1
[FW-policy-nat-rule-policy_1]source-address 192.168.1.0 24
[FW-policy-nat-rule-policy_1]action source-nat address-group nat_1
[FW-policy-nat]rule name policy_2
[FW-policy-nat-rule-policy_2]source-zone trust
[FW-policy-nat-rule-policy_2]destination-zone untrust2
[FW-policy-nat-rule-policy_2]source-address 192.168.1.0 24
[FW-policy-nat-rule-policy_2]action source-nat address-group nat_2

6.透明DNS
[FW]slb enable
[FW]slb
[FW-slb]group 0 dns
[FW-slb-group-0]metric roundrobin
[FW-slb-group-0]rserver 1 rip 100.1.1.1 port 53
[FW-slb-group-0]rserver 2 rip 200.1.1.1 port 53
[FW-slb]vserver 0 dns
[FW-slb-vserver-0]vip 10.10.10.10
[FW-slb-vserver-0]group dns
[FW-slb-vserver-0]dns-transparent-policy
[FW-policy-dns]dns transparent-proxy enable
[FW-policy-dns]dns server bind interface GigabitEthernet 1/0/1 preferred 100.1.1.1
[FW-policy-dns]dns server bind interface GigabitEthernet 1/0/2 preferred 200.1.1.1
[FW-policy-dns]rule name dnspolicy_1
[FW-policy-dns-rule-dnspolicy_1]source-address 192.168.1.0 24
[FW-policy-dns-rule-dnspolicy_1]enable
[FW-policy-dns-rule-dnspolicy_1]action tpdns

补.isp选路
[FW]healthcheck enable
[FW]healthcheck name dianxin
[FW-healthcheck-dianxin]destination 110.1.1.1 interface GigabitEthernet 1/0/1 protocol tcp-simple destination-port 80

[FW]int g 1/0/1
[FW-GigabitEthernet1/0/1]healthcheck dianxin
[FW-GigabitEthernet1/0/1]int g 1/0/2
[FW-GigabitEthernet1/0/2]healthcheck liantong



五、结果测试
1.免认证直接访问

2.protal认证无用户名密码无法访问