区块链论文速读 CCF A--USENIX Security 2025(6)

Conference:34th USENIX Security Symposium
CCF level:CCF A
Year:2025
Conference time:August 13–15, 2025 Seattle, WA, USA
区块链可投会议CCF A--Security 2026 截止2.5 附录用率
区块链论文速读 CCF A--USENIX Security 2025(1)
区块链论文速读 CCF A--USENIX Security 2025(2)
区块链论文速读 CCF A--USENIX Security 2025(3)
区块链论文速读 CCF A--USENIX Security 2025(4)
区块链论文速读 CCF A--USENIX Security 2025(5)
17
Title:
TockOwl: Asynchronous Consensus with Fault and Network Adaptability
TockOwl:具有故障和网络适应性的异步共识
Authors:

Abstract:
BFT protocols usually have a waterfall-like degradation in performance in the face of crash faults. Some BFT protocols may not experience sudden performance degradation under crash faults. They achieve this at the expense of increased communication and round complexity in fault-free scenarios. In a nutshell, existing protocols lack the adaptability needed to perform optimally under varying conditions.
We propose TockOwl, the first asynchronous consensus protocol with fault adaptability. TockOwl features quadratic communication and constant round complexity, allowing it to remain efficient in fault-free scenarios. TockOwl also possesses crash robustness, enabling it to maintain stable performance when facing crash faults. These properties collectively ensure the fault adaptability of TockOwl.
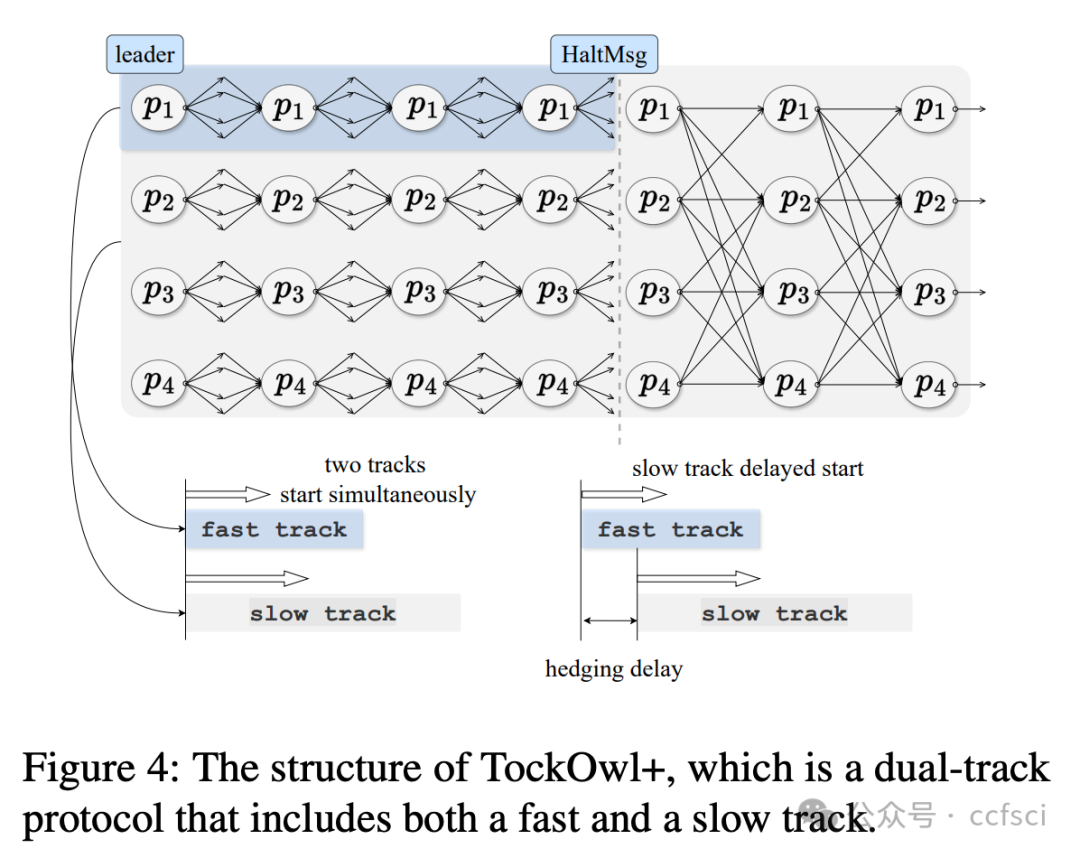
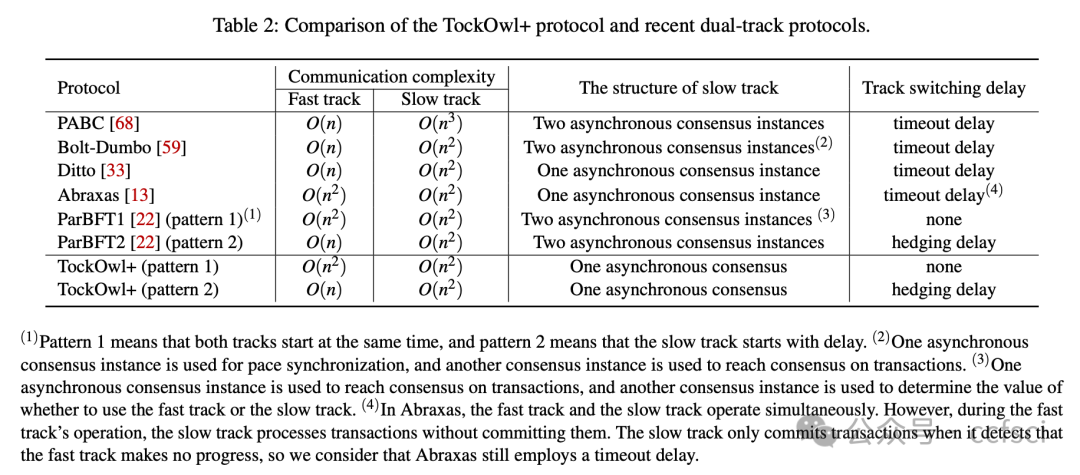
Furthermore, we propose TockOwl+ that has network adaptability. TockOwl+ incorporates both fast and slow tracks and employs hedging delays, allowing it to achieve low latency comparable to partially synchronous protocols without waiting for timeouts in asynchronous environments. Compared to the latest dual-track protocols, the slow track of TockOwl+ is simpler, implying shorter latency in fully asynchronous environments.
面对崩溃故障,BFT协议的性能通常会呈瀑布式下降。某些BFT协议在崩溃故障下可能不会出现性能骤降,但它们是以在无故障场景下增加通信复杂度和轮复杂度为代价的。简而言之,现有协议缺乏在不同条件下实现最佳性能所需的适应性。
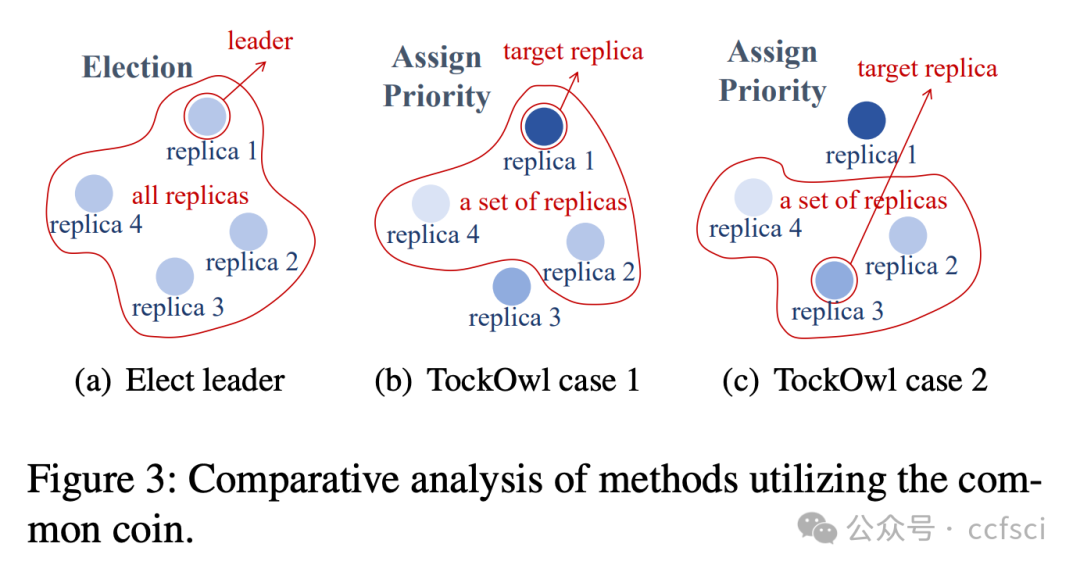
我们提出了TockOwl,这是首个具有故障适应性的异步共识协议。TockOwl采用二次通信复杂度和恒定轮复杂度,使其在无故障场景下保持高效。TockOwl还具有崩溃鲁棒性,使其在面对崩溃故障时也能保持稳定的性能。这些特性共同确保了TockOwl的故障适应性。
此外,我们还提出了具有网络适应性的TockOwl+。TockOwl+同时包含快速和慢速轨道,并采用延迟对冲机制,使其能够在异步环境中实现与部分同步协议相当的低延迟,而无需等待超时。与最新的双轨协议相比,TockOwl+ 的慢速轨道更简单,这意味着在完全异步的环境中延迟更短。
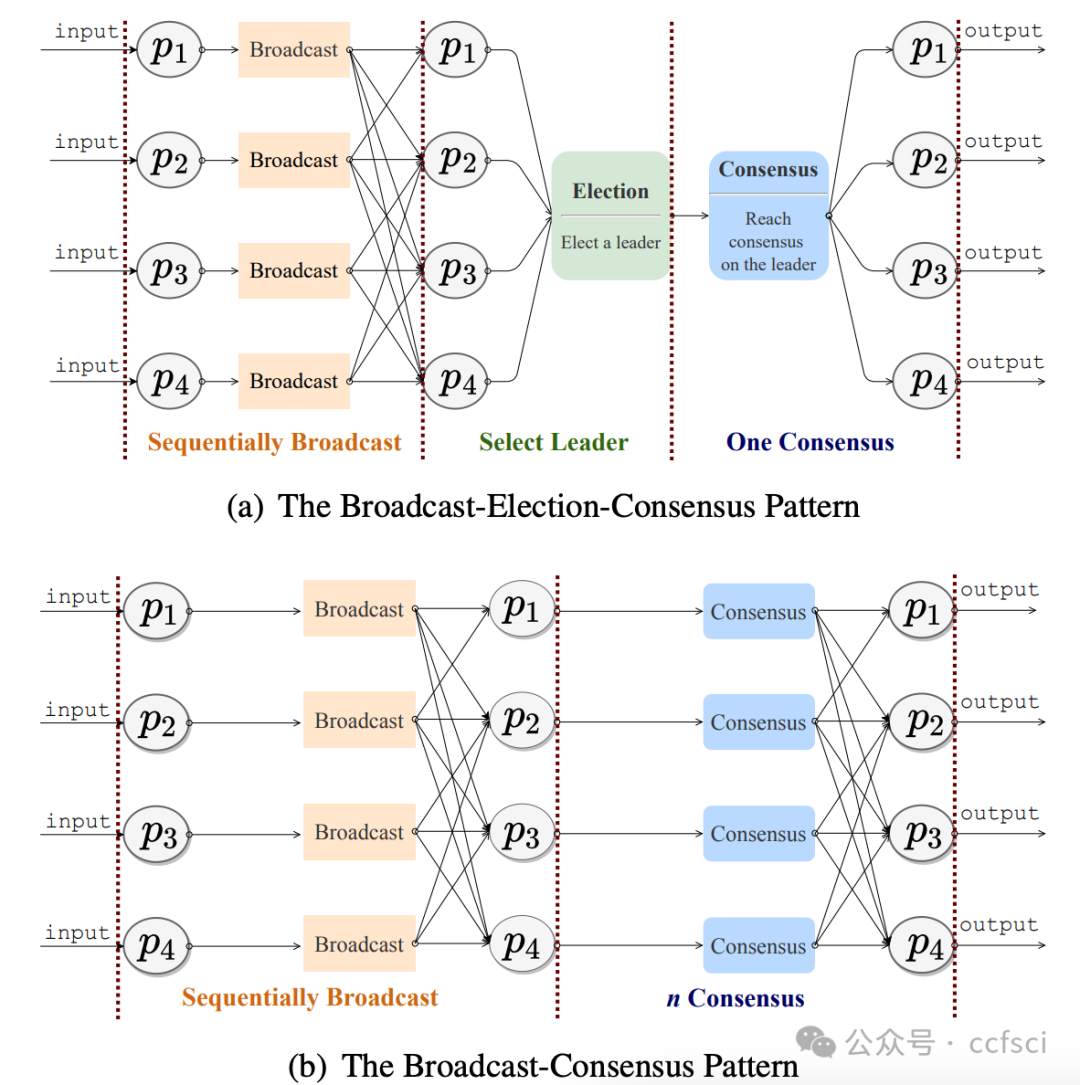
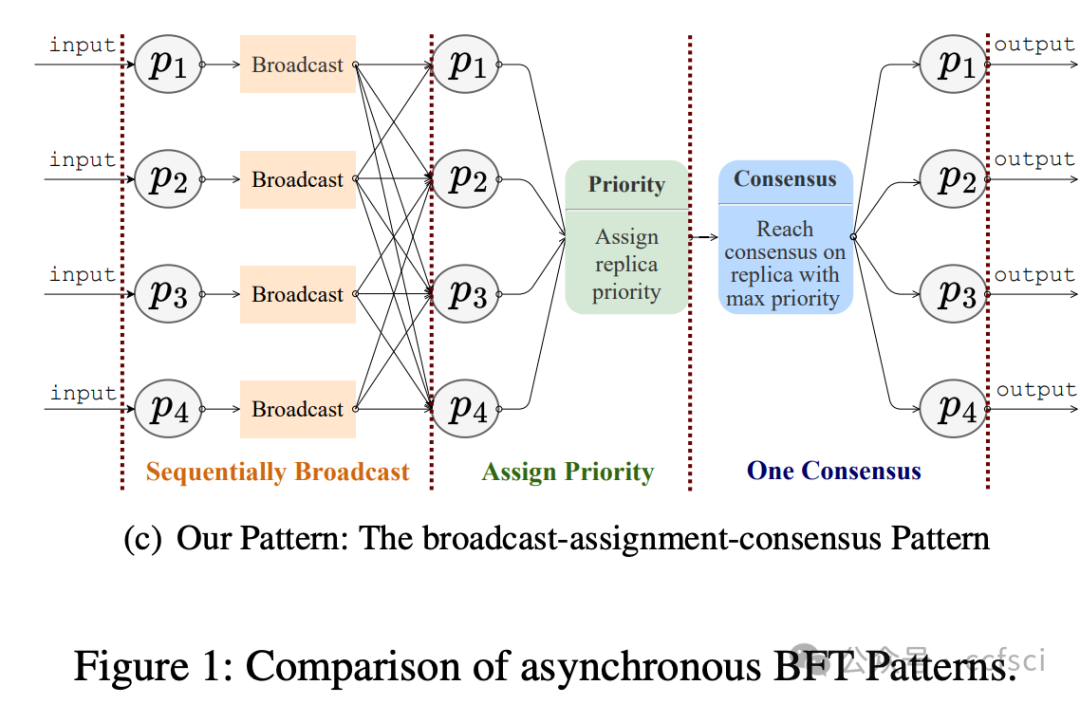
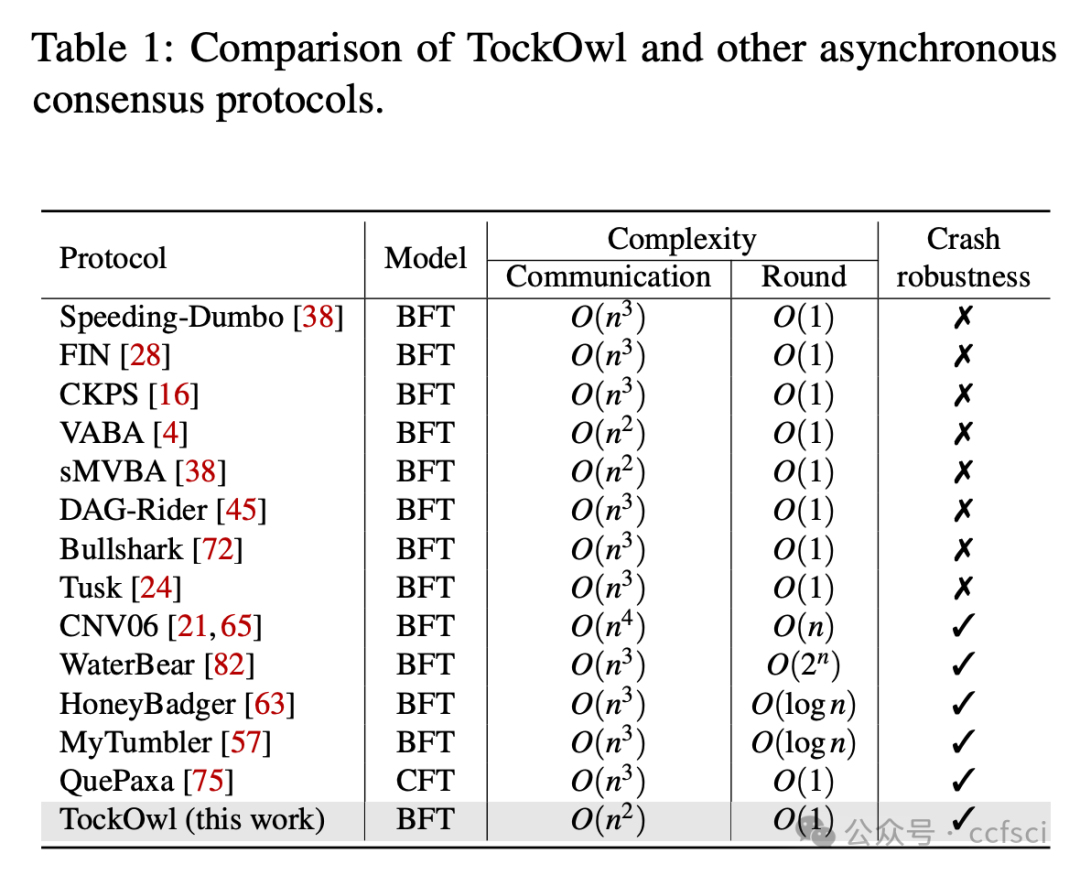
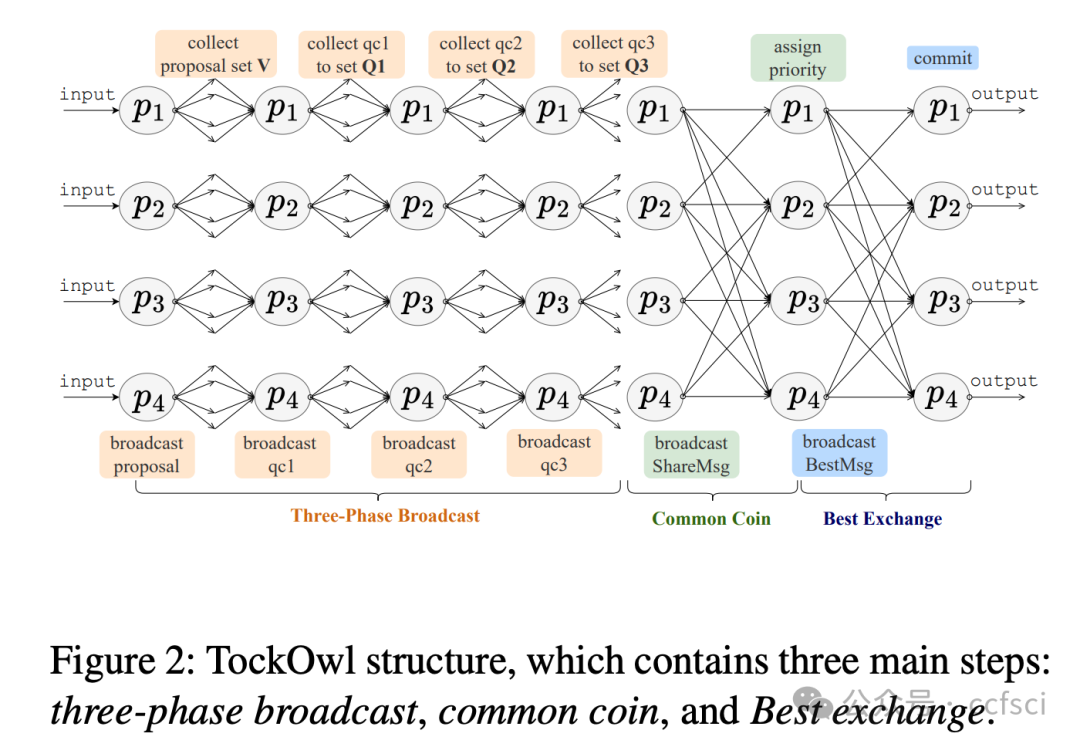



Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-li-minghang.pdf
18
Title:
Thunderdome: Timelock-Free Rationally-Secure Virtual Channels
雷霆穹顶:无时间锁定的理性安全虚拟通道
Authors:

Abstract:
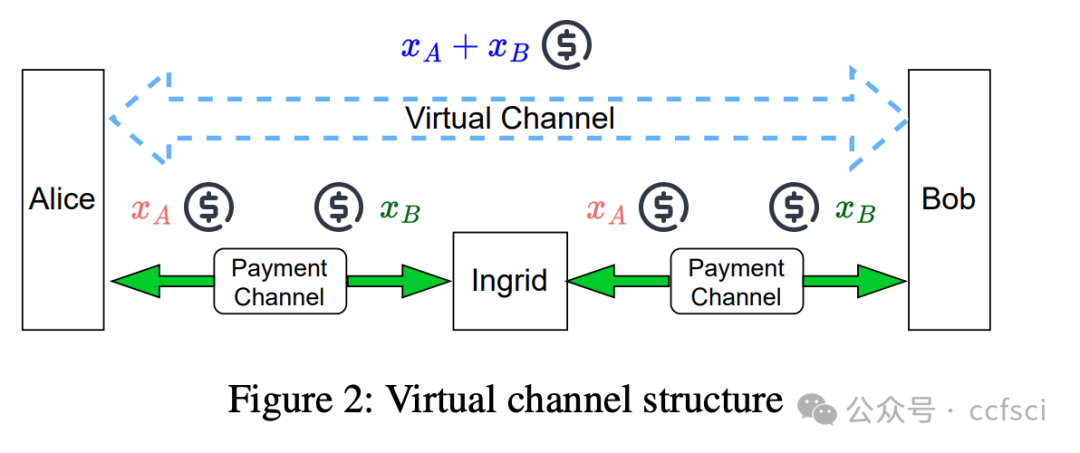
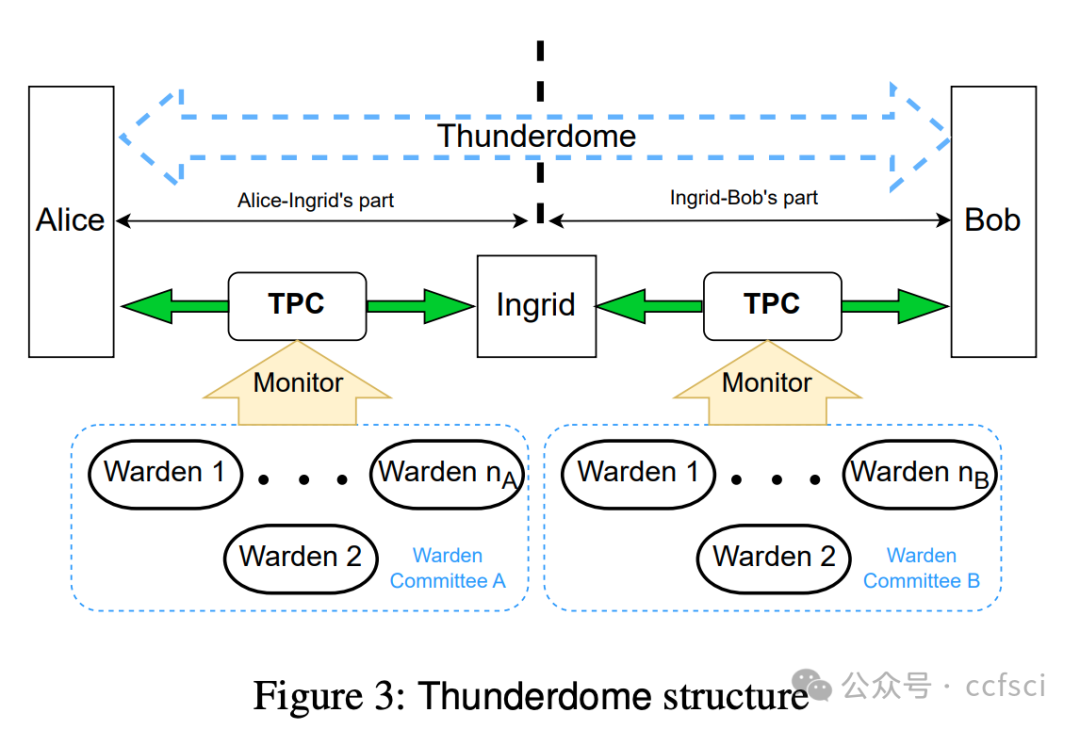
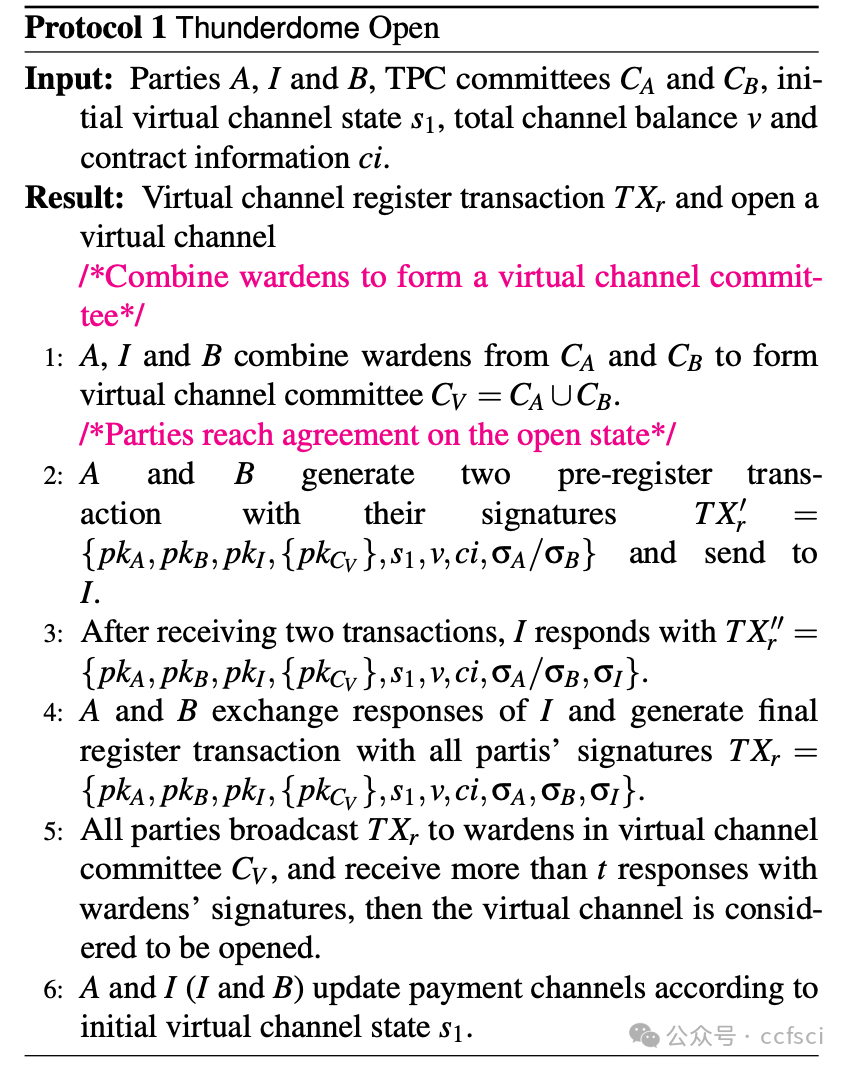
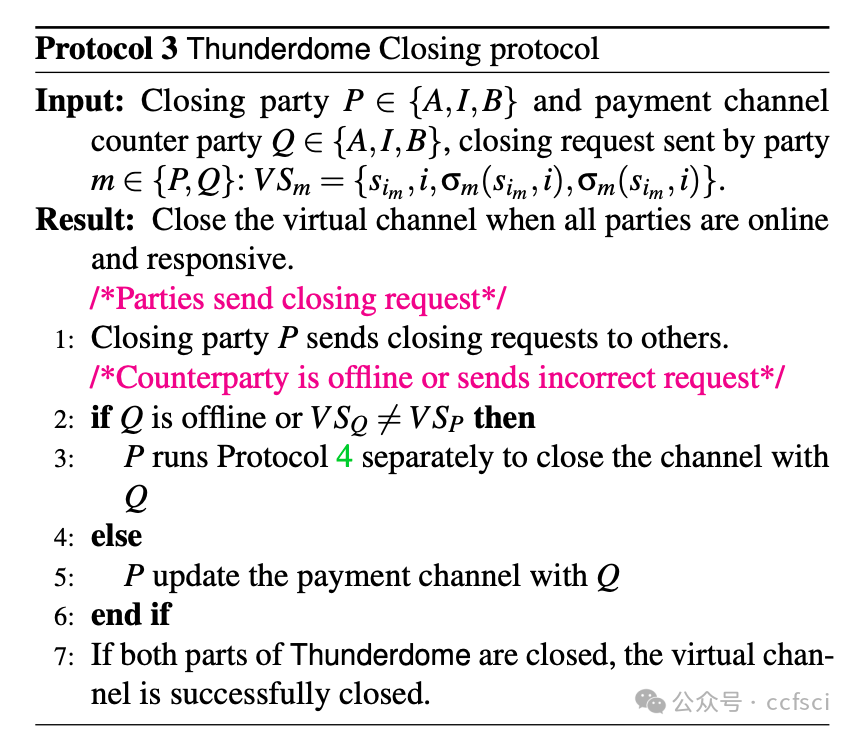
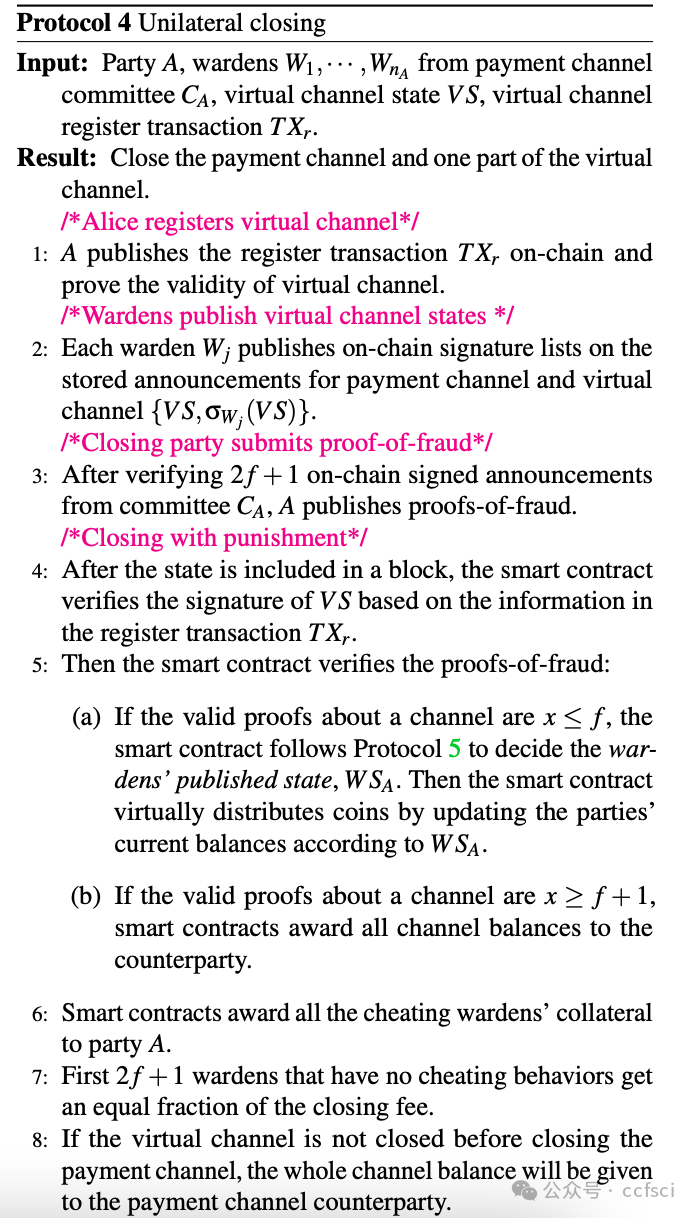
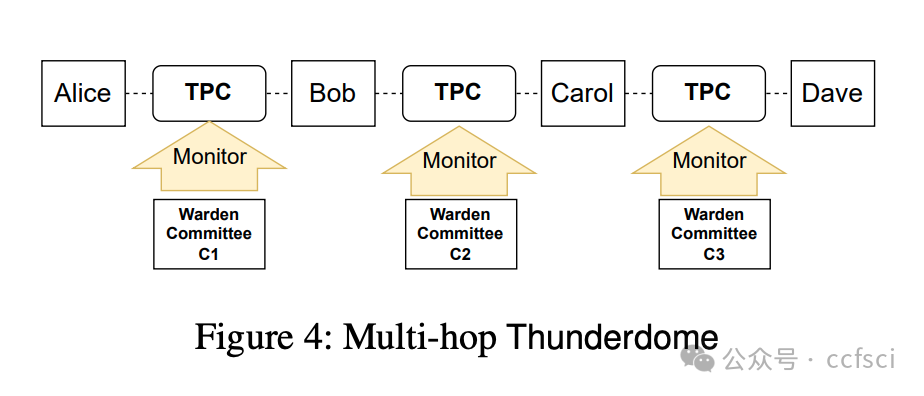
Payment channel networks (PCNs) offer a promising solution to address the limited transaction throughput of deployed blockchains. However, several attacks have recently been proposed that stress the vulnerability of PCNs to timelock and censoring attacks. To address such attacks, we introduce Thunderdome, the first timelock-free PCN. Instead, Thunderdome leverages the design rationale of virtual channels to extend a timelock-free payment channel primitive, thereby enabling multi-hop transactions without timelocks. Previous works either utilize timelocks or do not accommodate transactions between parties that do not share a channel.
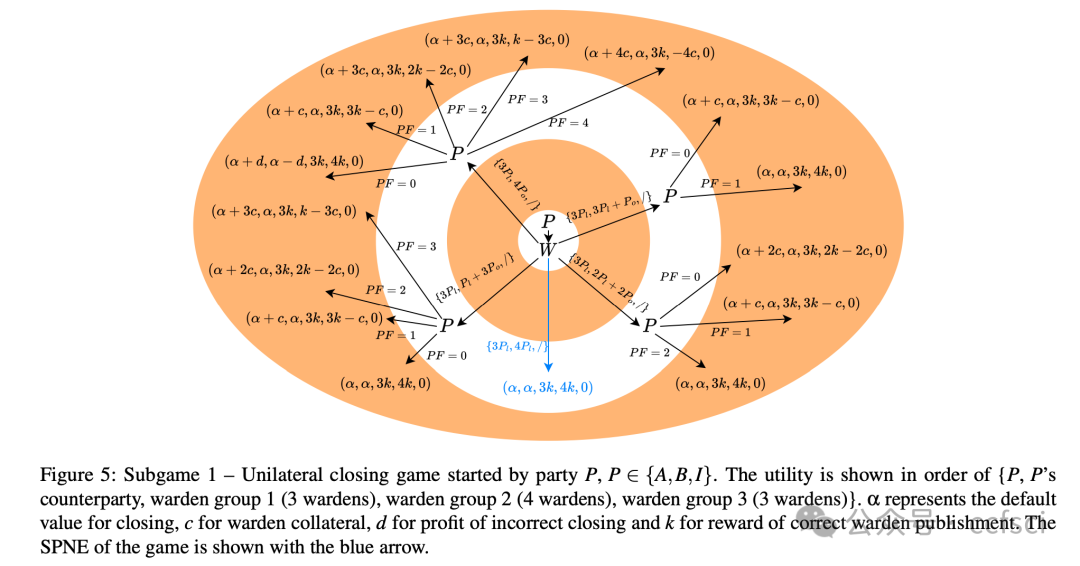
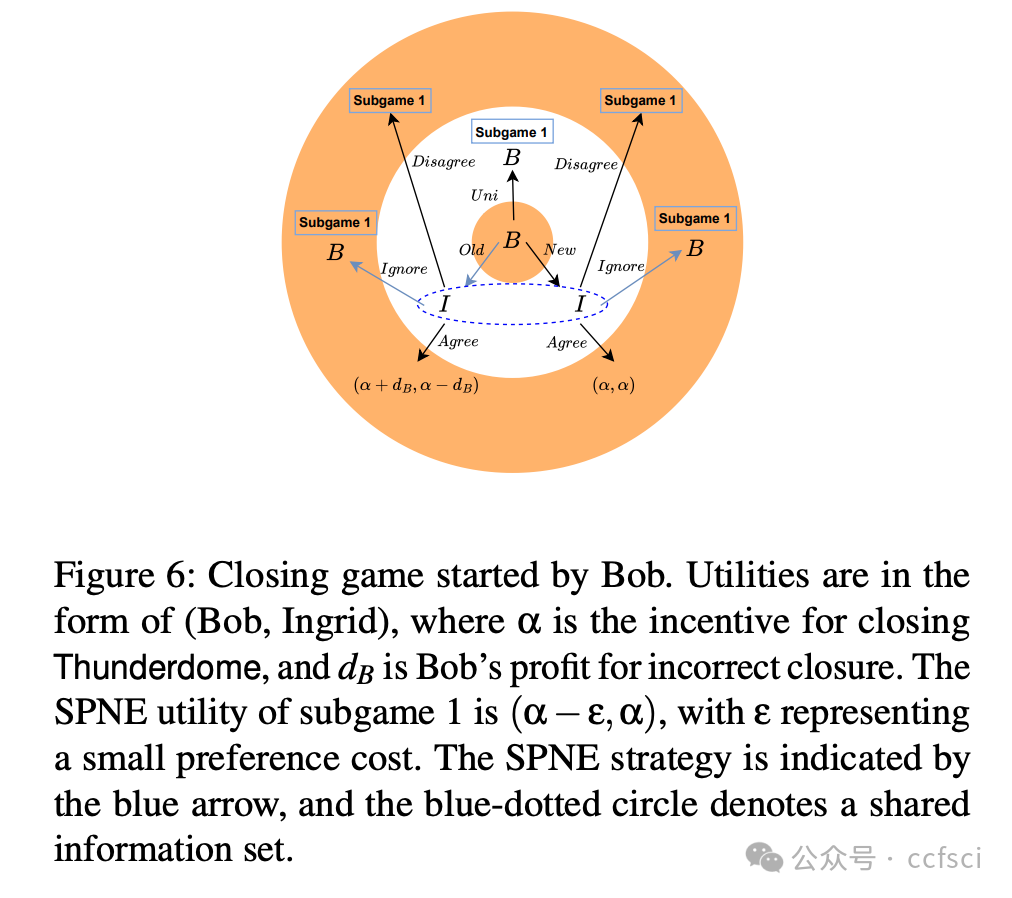
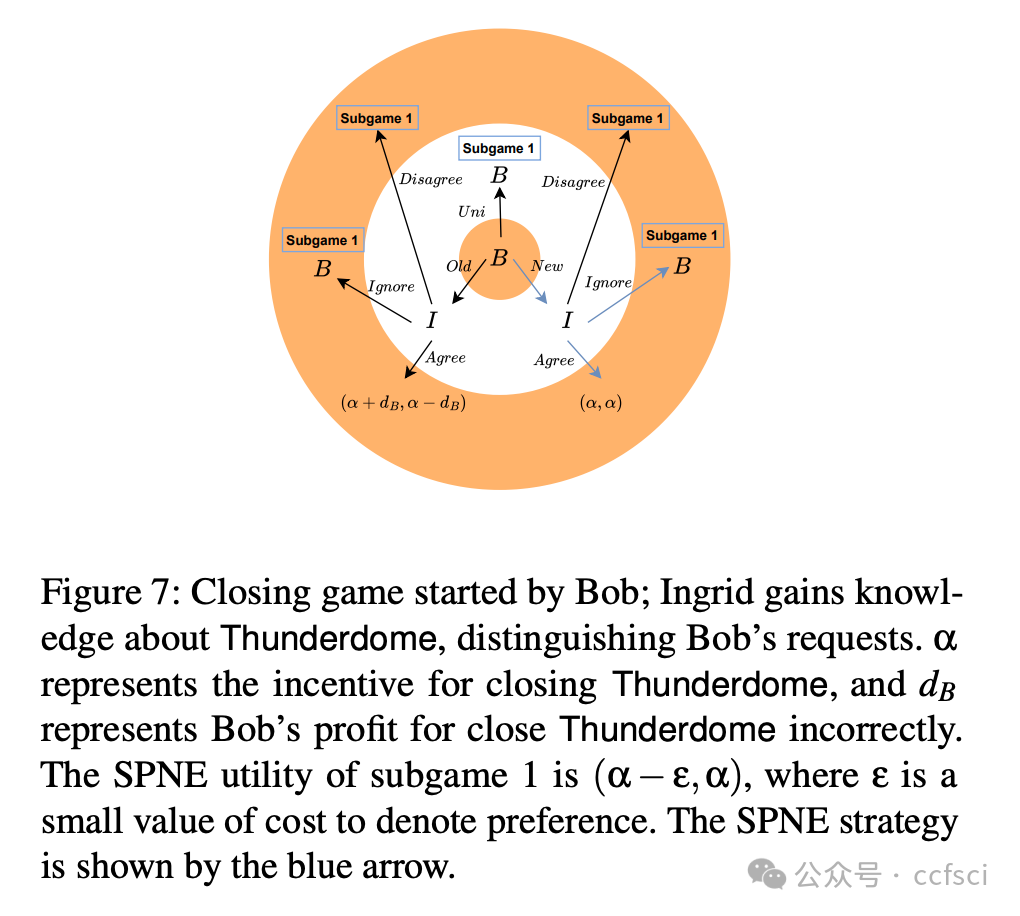
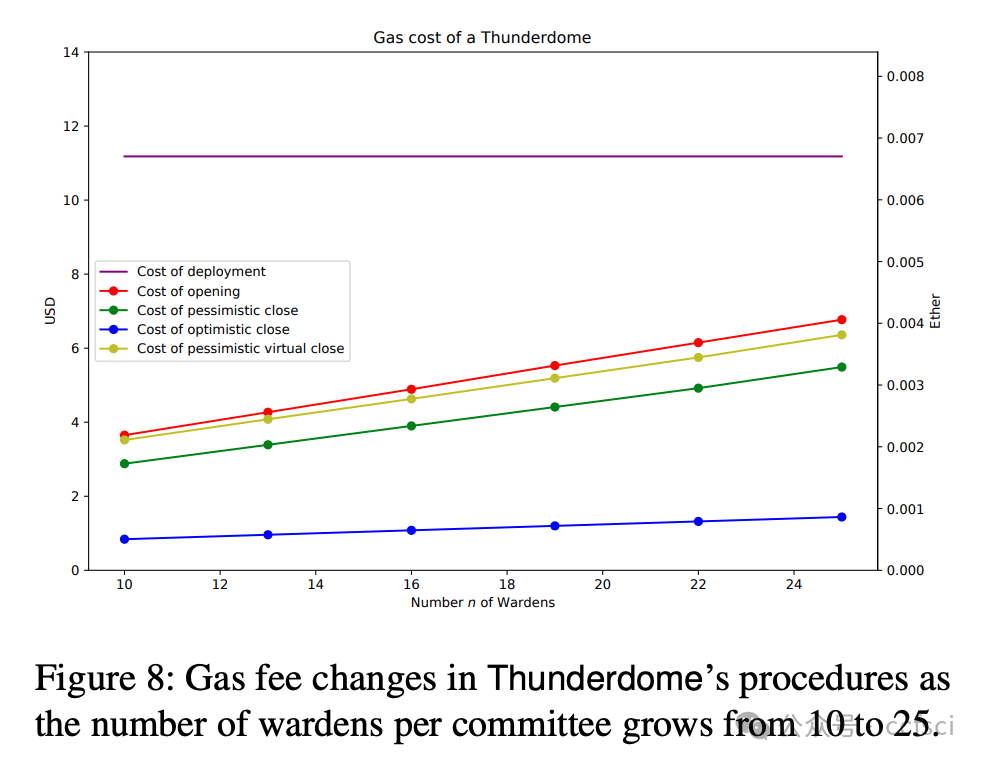
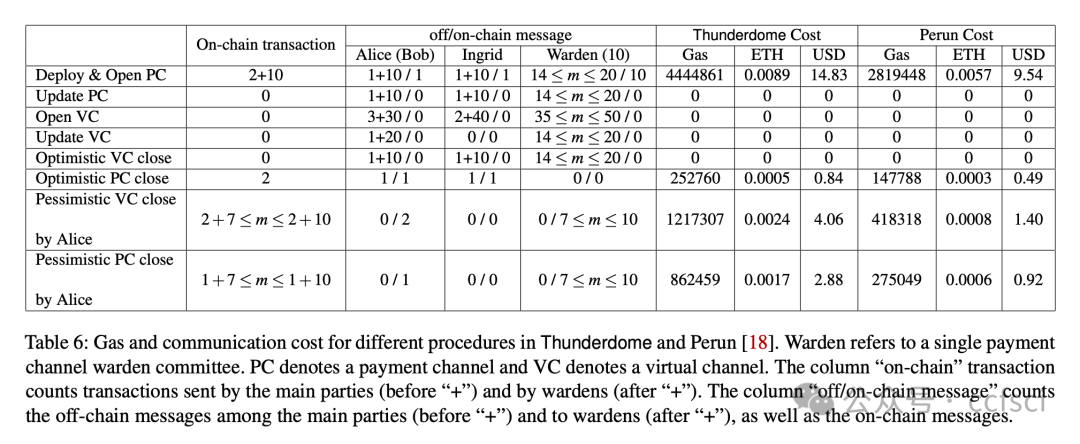
At its core, Thunderdome relies on a committee of non-trusted watchtowers, known as wardens, who ensure that no honest party loses funds, even when offline, during the channel closure process. We introduce tailored incentive mechanisms to ensure that all participants follow the protocol's correct execution. Besides a traditional security proof that assumes an honest majority of the committee, we conduct a formal game-theoretic analysis to demonstrate the security of Thunderdome when all participants, including wardens, act rationally. We implement a proof of concept of Thunderdome on Ethereum to validate its feasibility and evaluate its costs. Our evaluation shows that deploying Thunderdome, including opening the underlying payment channel, costs approximately $15 (0.0089 ETH), while the worst-case cost for closing a channel is about $7 (0.004 ETH).
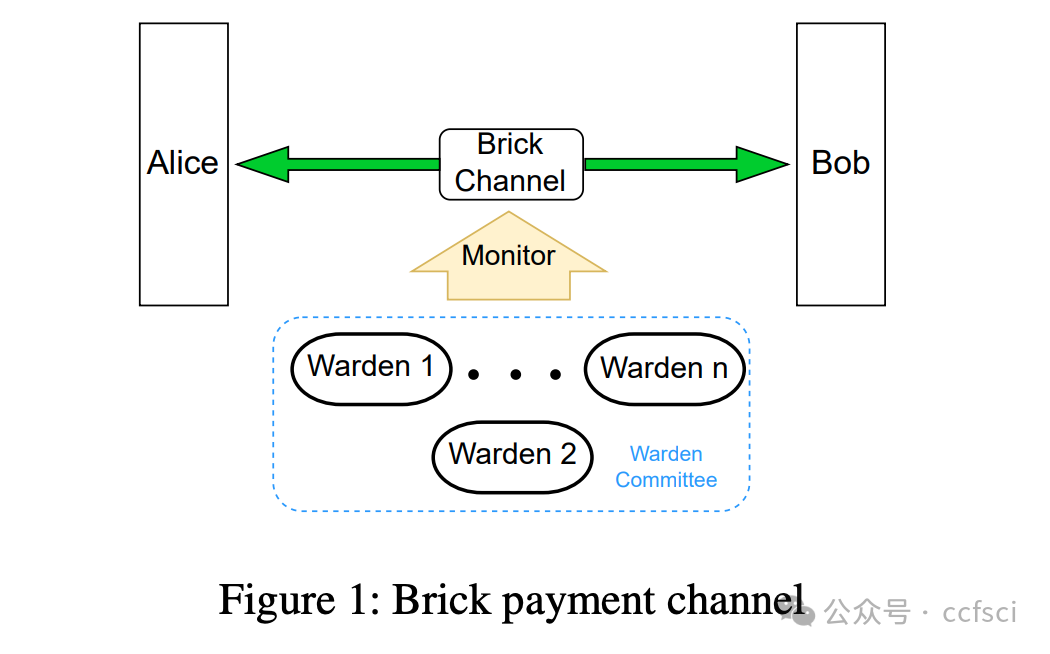
支付通道网络 (PCN) 为解决已部署区块链交易吞吐量有限的问题提供了一种很有前景的方案。然而,近期提出的多种攻击凸显了 PCN 易受时间锁攻击和审查攻击的脆弱性。为了应对这些攻击,我们提出了 Thunderdome,这是首个无时间锁的 PCN。Thunderdome 利用虚拟通道的设计理念扩展了无时间锁的支付通道原语,从而实现了无需时间锁的多跳交易。以往的工作要么使用时间锁,要么无法处理不共享通道的参与方之间的交易。
Thunderdome 的核心在于一个由非可信的“守卫者”组成的委员会,这些“守卫者”确保在通道关闭过程中,即使离线,任何诚实参与方也不会损失资金。我们引入了定制的激励机制,以确保所有参与者都遵循协议的正确执行。除了假设委员会中大多数成员诚实的传统安全证明之外,我们还进行了形式化的博弈论分析,以证明当所有参与者(包括“守卫者”)都理性行事时,Thunderdome 的安全性依然存在。我们在以太坊上实现了 Thunderdome 的概念验证,以验证其可行性并评估其成本。我们的评估表明,部署 Thunderdome(包括开通底层支付通道)的成本约为 15 美元(0.0089 ETH),而关闭通道的最坏情况成本约为 7 美元(0.004 ETH)。


Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-avarikioti.pdf
19
Title:
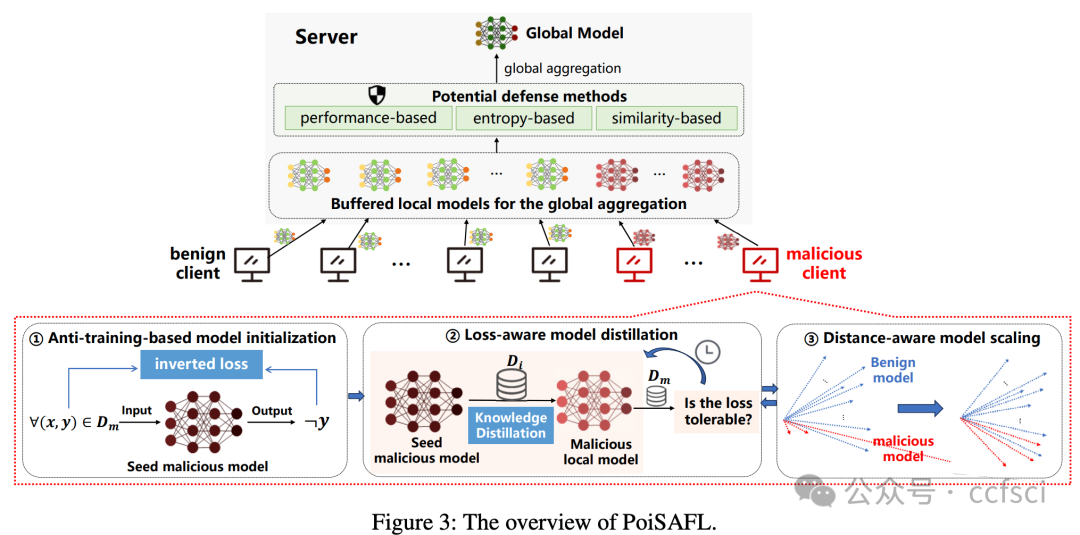
PoiSAFL: Scalable Poisoning Attack Framework to Byzantine-resilient Semi-asynchronous Federated Learning
PoiSAFL:可扩展的投毒攻击框架,用于抗拜占庭攻击的半异步联邦学习
Authors:

Abstract:
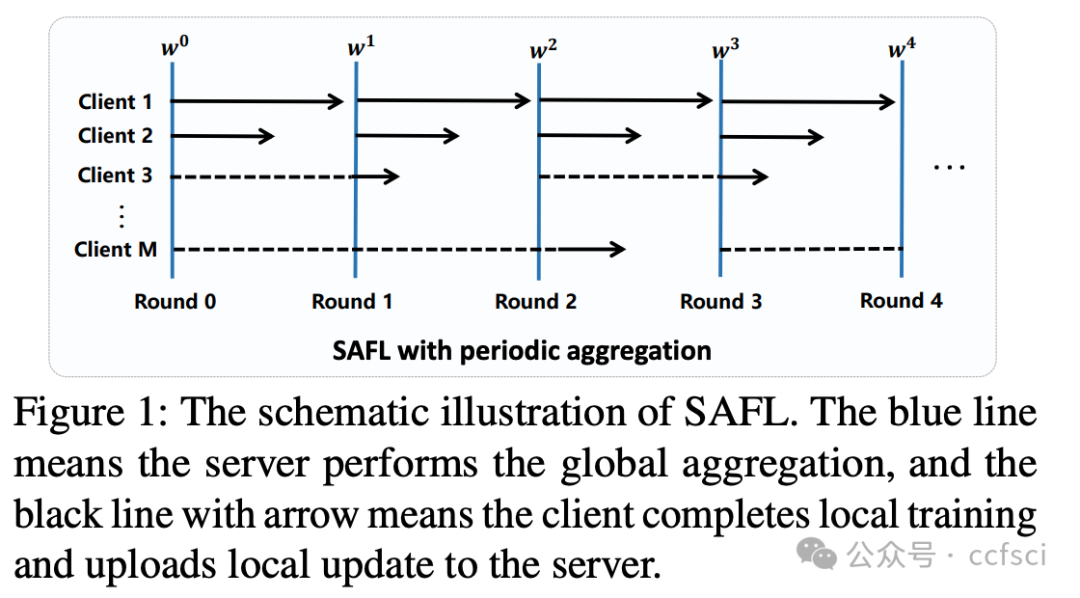
Semi-asynchronous federated learning (SAFL) enhances the efficiency of privacy-preserving collaborative learning across clients with diverse processing capabilities. It updates the global model by aggregating local models from only partial fast clients without waiting for all clients to synchronize. We realize that such semi-asynchronous aggregation may expose the system to serious poisoning risks, even when defenses are in place, since it introduces considerable inconsistency among local models, giving chances for attackers to inject inconspicuous malicious ones. However, such risks remain largely underexplored. To plug this gap and fully explore the vulnerability of SAFL, in this paper, we propose a scalable stealth poisoning attack framework for Byzantine-resilient SAFL, called PoiSAFL. It can effectively impair SAFL's learning performance while bypassing three typical kinds of Byzantine-resilient defenses by strategically controlling malicious clients to upload undetectable malicious local models. The challenge lies in crafting malicious models that evade detection yet remain destructive. We construct a constrained optimization problem and propose three modules to approximate the optimization objective: the anti-training-based model initialization, loss-aware model distillation, and distance-aware model scaling. These modules initialize and refine malicious models with desired poisoning ability while keeping their performance, prediction entropy, and dissimilarity within benign ranges to bypass detection. Extensive experiments demonstrate that PoiSAFL can defeat three typical categories of defenses. Besides, PoiSAFL can further amplify its attack impact by flexibly executing three proposed modules. Note that PoiSAFL is scalable and can incorporate new modules to defeat future new types of defenses.
半异步联邦学习(SAFL)能够提升跨客户端(处理能力各异)的隐私保护协作学习效率。它通过聚合部分快速客户端的本地模型来更新全局模型,无需等待所有客户端同步。我们意识到,即使采取了防御措施,这种半异步聚合仍可能使系统面临严重的投毒风险,因为它会在本地模型之间引入相当大的不一致性,从而为攻击者注入不易察觉的恶意模型提供了机会。然而,此类风险仍未得到充分研究。为了弥补这一空白并全面探索SAFL的脆弱性,本文提出了一种可扩展的、针对拜占庭防御的SAFL的隐蔽投毒攻击框架,称为PoiSAFL。它能够通过策略性地控制恶意客户端上传无法检测的恶意本地模型,从而有效降低SAFL的学习性能,同时绕过三种典型的拜占庭防御机制。其挑战在于如何构建既能逃避检测又能保持破坏性的恶意模型。我们构建了一个约束优化问题,并提出了三个模块来逼近优化目标:基于反训练的模型初始化、损失感知模型蒸馏和距离感知模型缩放。这些模块初始化并优化具有所需投毒能力的恶意模型,同时将其性能、预测熵和差异性保持在良性范围内,从而绕过检测。大量实验表明,PoiSAFL 可以突破三种典型的防御措施。此外,PoiSAFL 还可以通过灵活执行这三个模块来进一步增强其攻击效果。值得注意的是,PoiSAFL 具有可扩展性,可以集成新的模块来应对未来新型的防御措施。
Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-pang-xiaoyi.pdf
