区块链论文速读 CCF A--USENIX Security 2025(3)

Conference:34th USENIX Security Symposium
CCF level:CCF A
Year:2025
Conference time:August 13–15, 2025 Seattle, WA, USA
区块链可投会议CCF A--Security 2026 截止2.5 附录用率
区块链论文速读 CCF A--USENIX Security 2025(1)
区块链论文速读 CCF A--USENIX Security 2025(2)
8
Title:
Ghost Clusters: Evaluating Attribution of Illicit Services through Cryptocurrency Tracing
幽灵集群:通过加密货币追踪评估非法服务的归因
Authors:

Abstract:
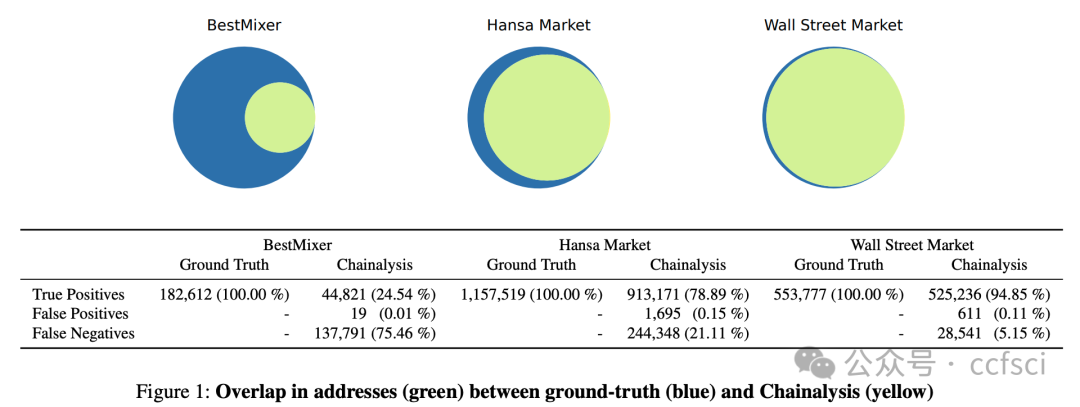
One of the principles in cryptocurrency tracing is putting a name to an address—a process called attribution. Attribution is key for both law enforcement and compliance professionals. Blockchain intelligence companies sell attribution as a service by leveraging pseudonymous blockchains, clustering heuristics, and labeling of addresses. In this paper, we perform a case study on Chainalysis, the market leader, and evaluate its attribution by comparing it against ground-truth data on three seized illicit services—BestMixer, Hansa Market, and Wall Street Market. To design the evaluation, we interview front-line law enforcement professionals and learn how they trace cryptocurrencies using blockchain intelligence providers. We identify three evaluation techniques— i.e., address overlap, money flows, and address roles—that realistically measure attribution in line with law enforcement use cases. Using these techniques, we show that for our three illicit services, Chainalysis provides a reliable lower bound (24.54 to 94.85 percent accurate), and produces very few false positives (less than 0.5 percent). Also, we find that coverage changes over time. We reason about factors that influence attribution and demonstrate the importance of attributing certain key addresses to achieve high coverage, and with that, show that when including a second blockchain intelligence provider, the difficulties in generalizing results.
加密货币追踪的一项基本原则是为地址赋予名称——这一过程称为归因。归因对于执法和合规专业人员都至关重要。区块链情报公司利用匿名区块链、聚类启发式算法和地址标记等技术,提供归因服务。本文以市场领导者 Chainalysis 为例,通过将其归因结果与三个被查获的非法服务(BestMixer、Hansa Market 和 Wall Street Market)的真实数据进行比较,评估其归因能力。为了设计评估方案,我们采访了多位一线执法人员,了解他们如何利用区块链情报提供商追踪加密货币。我们确定了三种评估技术——地址重叠、资金流向和地址角色——这些技术能够根据执法用例真实地衡量归因效果。运用这些技术,我们证明,对于这三个非法服务,Chainalysis 能够提供可靠的归因下限(准确率在 24.54% 到 94.85% 之间),并且误报率极低(低于 0.5%)。此外,我们发现覆盖率会随时间变化。我们分析了影响归因的因素,并论证了对某些关键地址进行归因以实现高覆盖率的重要性。由此,我们还发现,当引入第二个区块链情报提供商时,结果的普适性会受到影响。
Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-lubbertsen.pdf
9
Title:
Surviving in Dark Forest: Towards Evading the Attacks from Front-Running Bots in Application Layer
在黑暗森林中生存:如何规避应用层中抢跑机器人的攻击
Authors:

Abstract:
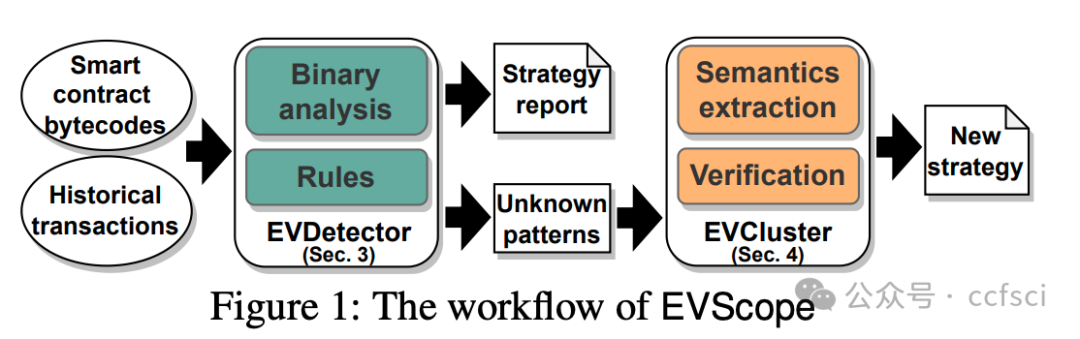
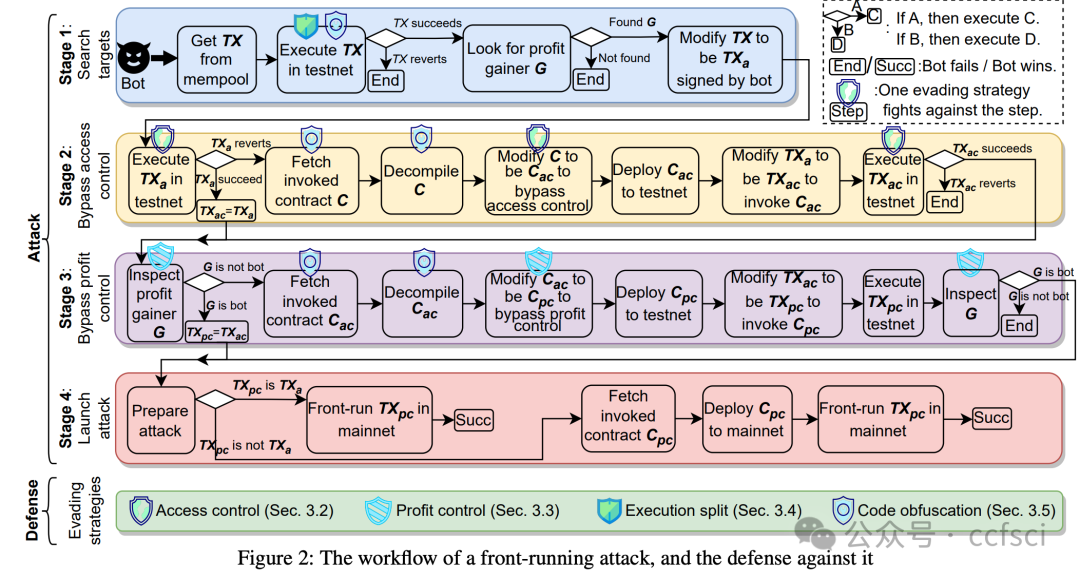
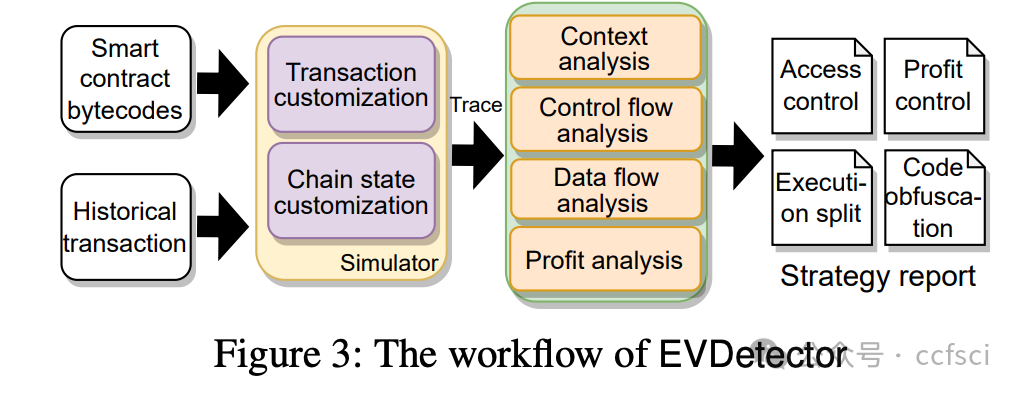
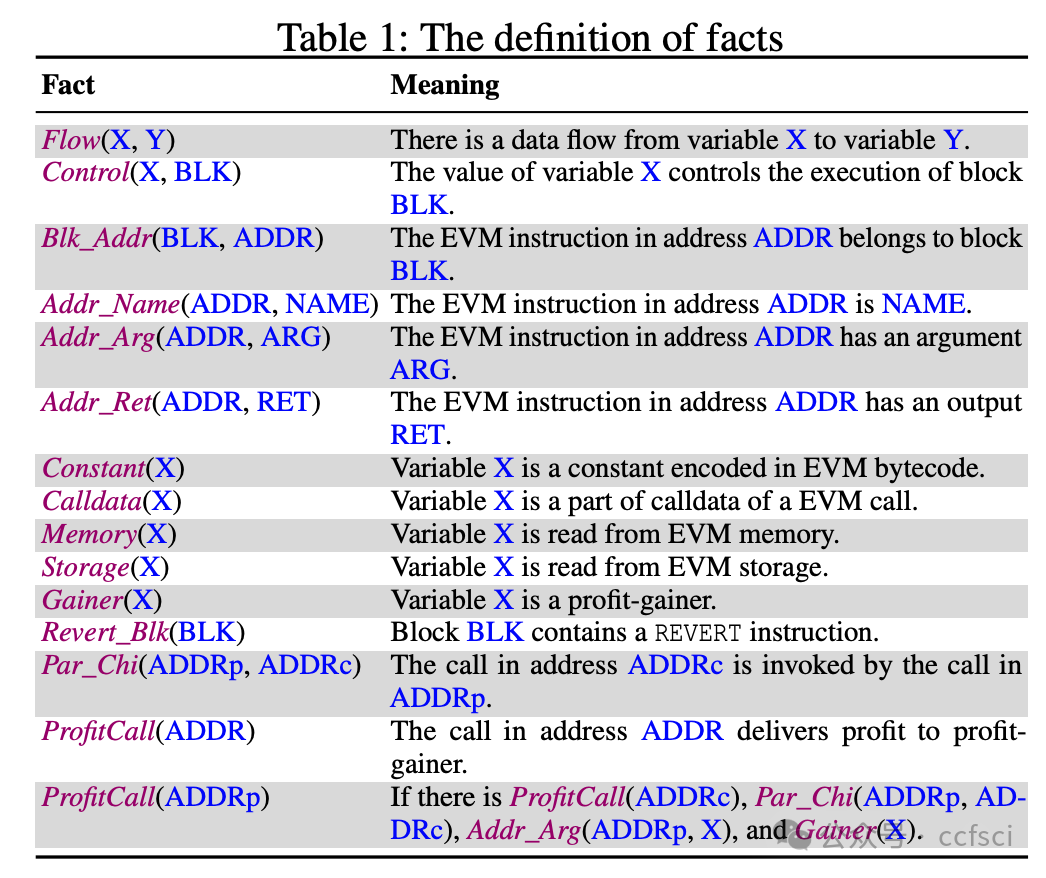
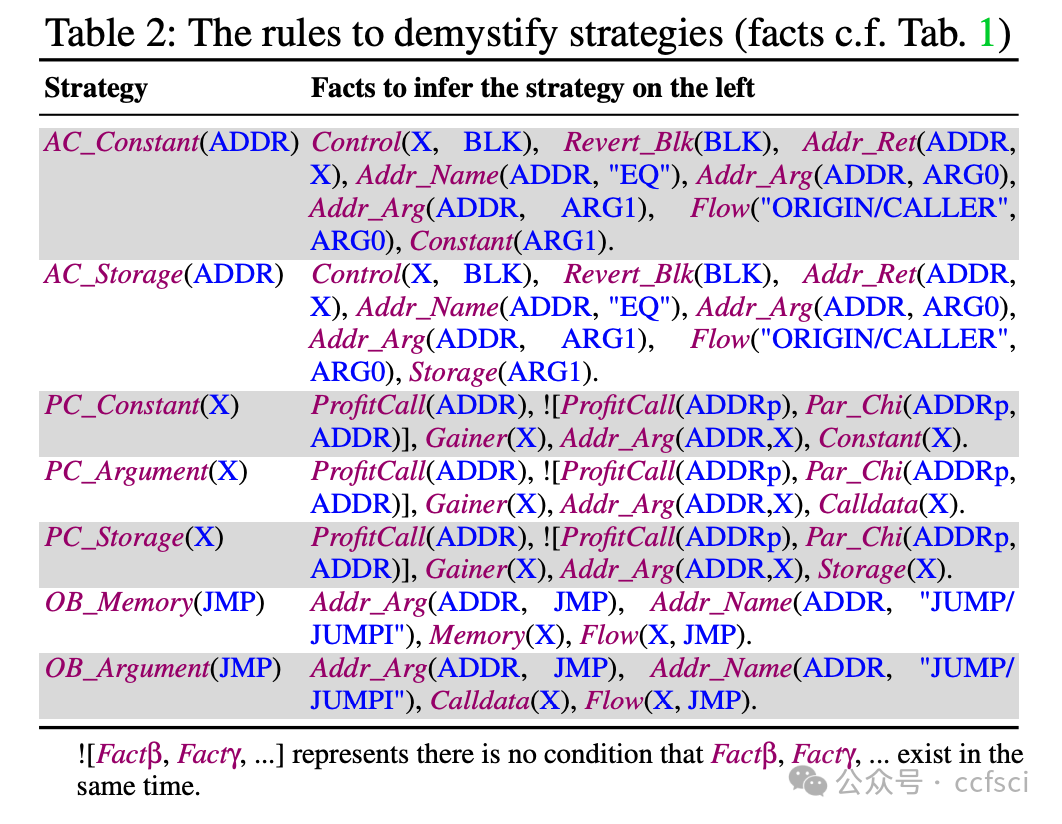
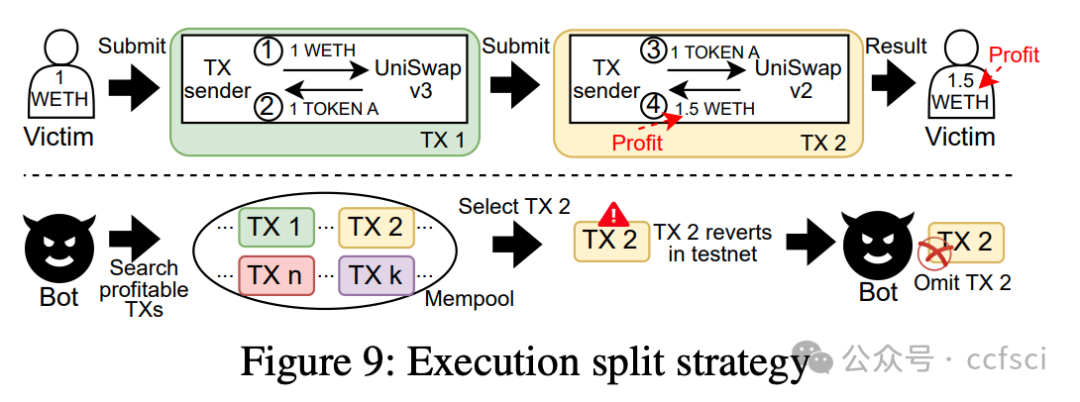
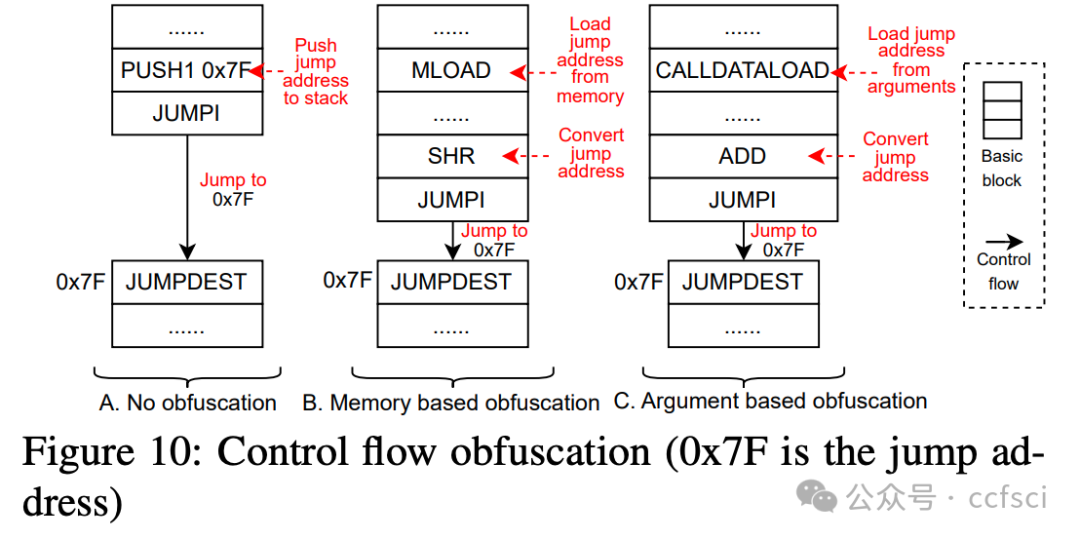
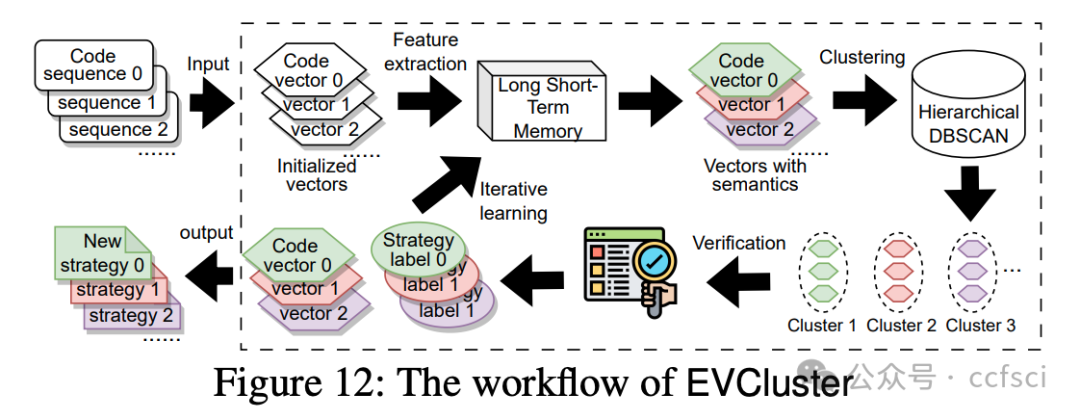
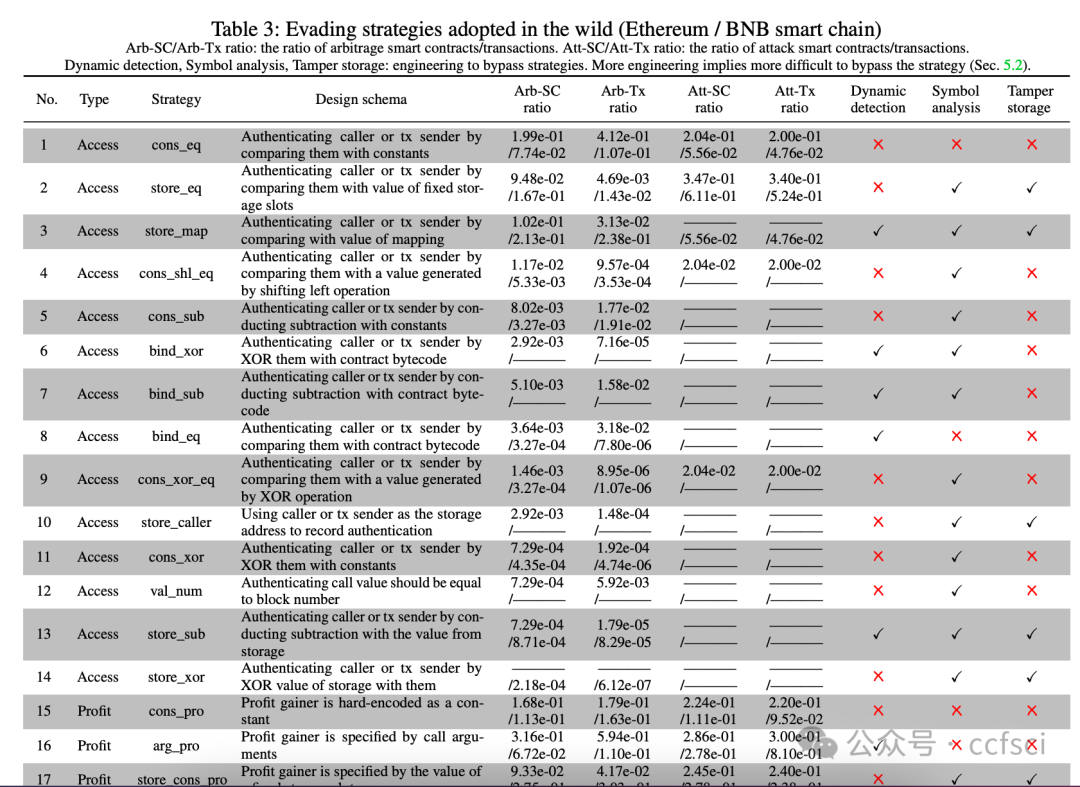
Blockchains face significant risks from front-running attacks, leading to multi-billion USD losses. These attacks are often executed by front-running bots, automated tools that operate at high speed to execute transactions, exacerbating the threat landscape. Consequently, it is crucial for blockchain developers to design strategies at the application layer to mitigate these attacks. Interestingly, real-world strategies for evading front-running remain under-explored in their taxonomy and distribution due to their covert nature. Understanding these evasion tactics is vital for assessing the resilience of the current blockchain application layer and identifying areas for potential enhancement, thereby strengthening the ecosystem. In this work, we take the first step to demystify evading strategies in Ethereum and BNB Smart Chain. We propose EVScope, a novel framework combining binary analysis and machine learning to detect known and unknown evading strategies. Using EVScope, we examine 6,761,186 arbitrage transactions and 71 significant attack transactions that evaded the front-running attacks from bots in the wild. Our findings uncover 32 refined strategies involving access control, profit control, execution split, and code obfuscation. 25/32 are first introduced in this work, and 28/32 are first applied in evading front-running, which fills a critical gap in the literature.
区块链面临着抢先交易攻击的巨大风险,这些攻击可能导致数十亿美元的损失。此类攻击通常由抢先交易机器人执行,这些自动化工具高速运行以执行交易,加剧了威胁形势。因此,区块链开发者必须在应用层设计策略来缓解这些攻击。有趣的是,由于抢先交易的隐蔽性,现实世界中规避抢先交易的策略在分类和分布方面仍未得到充分研究。了解这些规避策略对于评估当前区块链应用层的韧性以及确定潜在的改进领域至关重要,从而增强整个生态系统。本文旨在揭开以太坊和 BNB 智能链中规避策略的神秘面纱。我们提出了 EVScope,这是一个结合了二进制分析和机器学习的新型框架,用于检测已知和未知的规避策略。利用 EVScope,我们分析了 6,761,186 笔套利交易和 71 笔成功规避了来自机器人抢先交易攻击的重大攻击交易。我们的研究结果揭示了32种精细化的策略,涉及访问控制、利润控制、执行分离和代码混淆。其中25种策略是首次在本文中提出,28种策略是首次应用于规避抢先交易,填补了现有文献中的一个关键空白。

Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-ma-zuchao.pdf
10
Title:
CollisionRepair: First-Aid and Automated Patching for Storage Collision Vulnerabilities in Smart Contracts
碰撞修复:智能合约中存储碰撞漏洞的急救和自动修补
Authors:

Abstract:
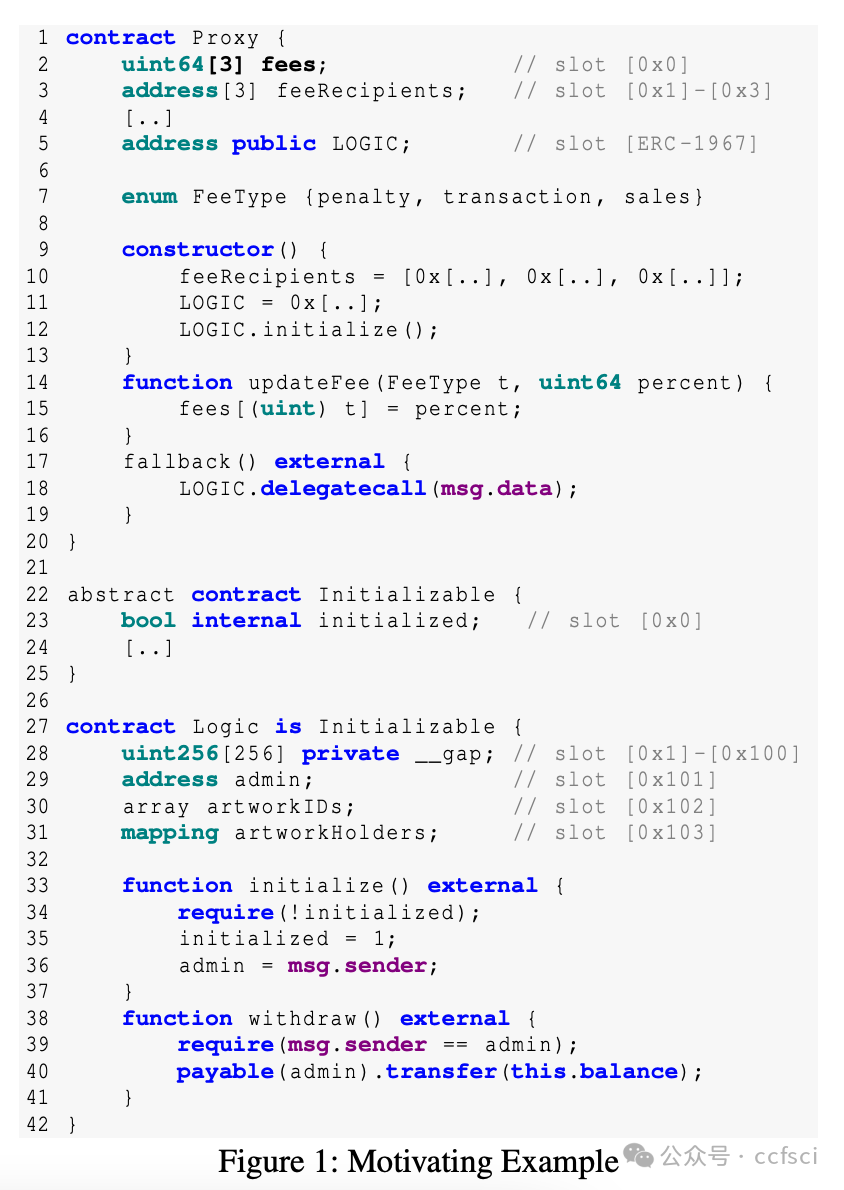
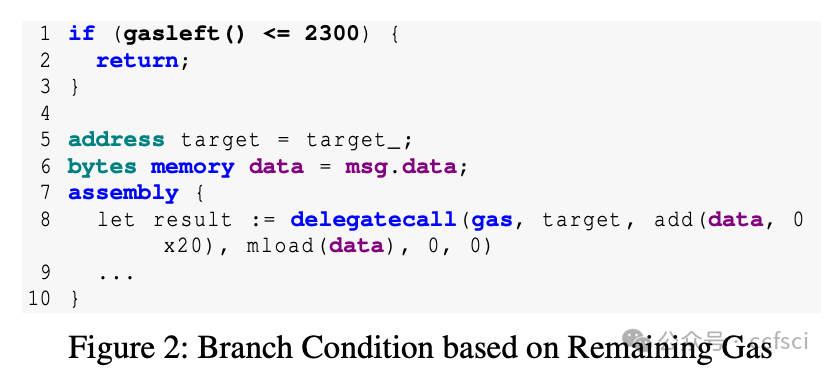
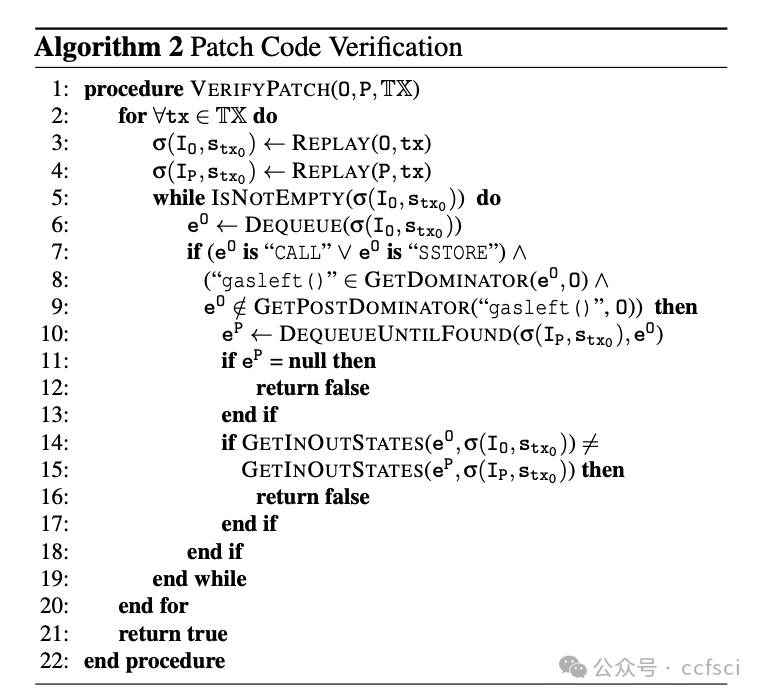
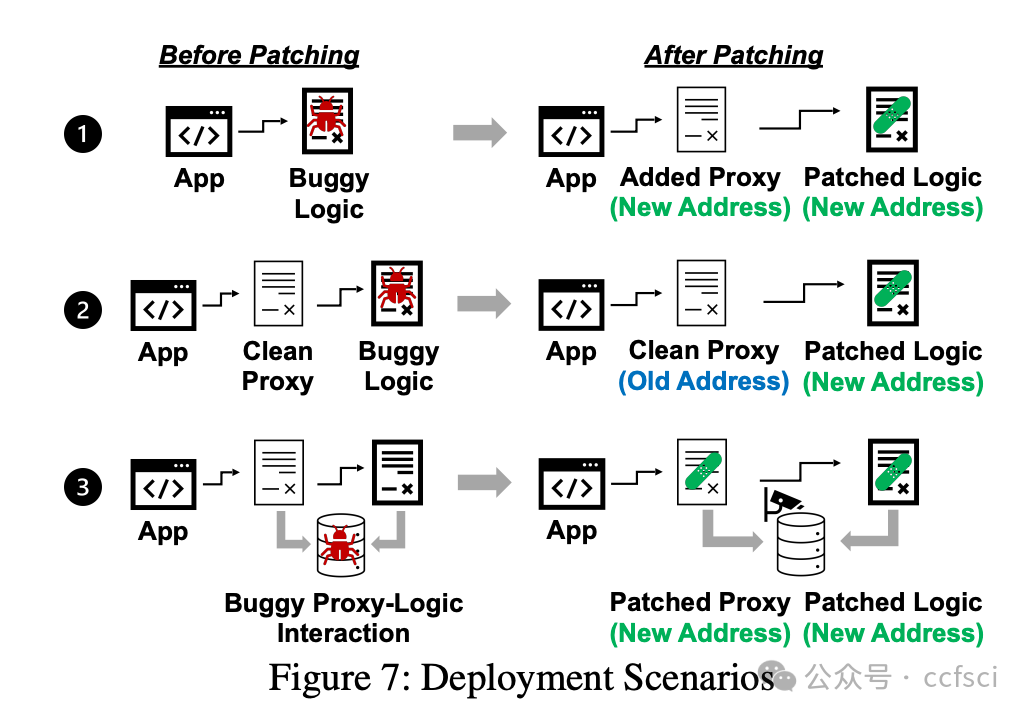
Storage collision vulnerabilities, a significant security risk in upgradeable smart contracts, often arise when a user-facing proxy contract and a backend logic contract share storage space. While static analysis techniques can detect such issues, they often over-approximate program states, leading to false positives and requiring developers to manually verify each issue, giving attackers time to exploit any overlooked vulnerabilities. To address this, we propose CollisionRepair, an automated patching technique for mitigating storage collision risks. CollisionRepair monitors storage access sequences between proxy and logic contracts by defining an "ownership" property for storage locations. It then replays historical transactions to recover existing storage ownership, ensuring the patched code aligns with the current state. A gas impact-aware differential analysis is applied to verify the patch, distinguishing genuine behavioral changes from variations caused by gas usage. Our evaluation on 12,526 real-world vulnerable upgradeable contracts shows that CollisionRepair effectively detects and mitigates storage collision attacks without interfering with normal contract operations.
存储冲突漏洞是可升级智能合约中一个重大的安全风险,通常发生在面向用户的代理合约和后端逻辑合约共享存储空间时。虽然静态分析技术可以检测到此类问题,但它们往往会过度近似程序状态,导致误报,并需要开发人员手动验证每个问题,从而给攻击者利用任何被忽略的漏洞的机会。为了解决这个问题,我们提出了 CollisionRepair,一种用于缓解存储冲突风险的自动化补丁技术。CollisionRepair 通过为存储位置定义“所有权”属性来监控代理合约和逻辑合约之间的存储访问序列。然后,它重放历史交易以恢复现有的存储所有权,确保修补后的代码与当前状态保持一致。我们应用了一种考虑 gas 影响的差异分析来验证补丁,从而区分真正的行为变化和 gas 使用引起的波动。我们对 12,526 个真实存在的易受攻击的可升级合约进行了评估,结果表明 CollisionRepair 能够有效地检测和缓解存储冲突攻击,而不会干扰合约的正常操作。
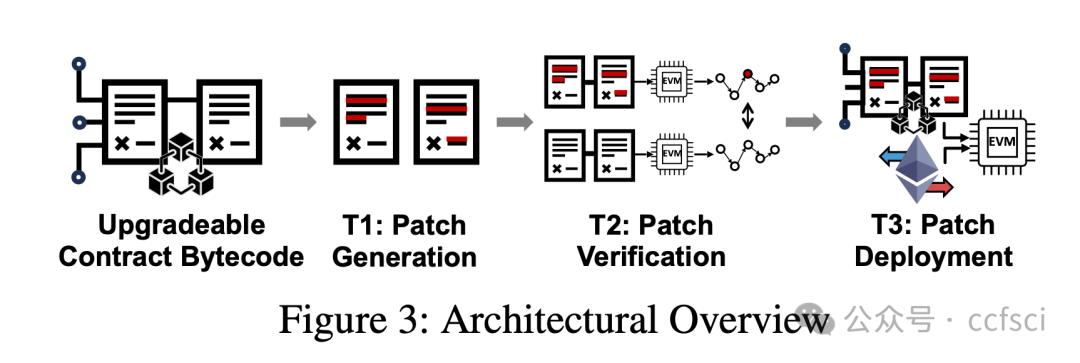
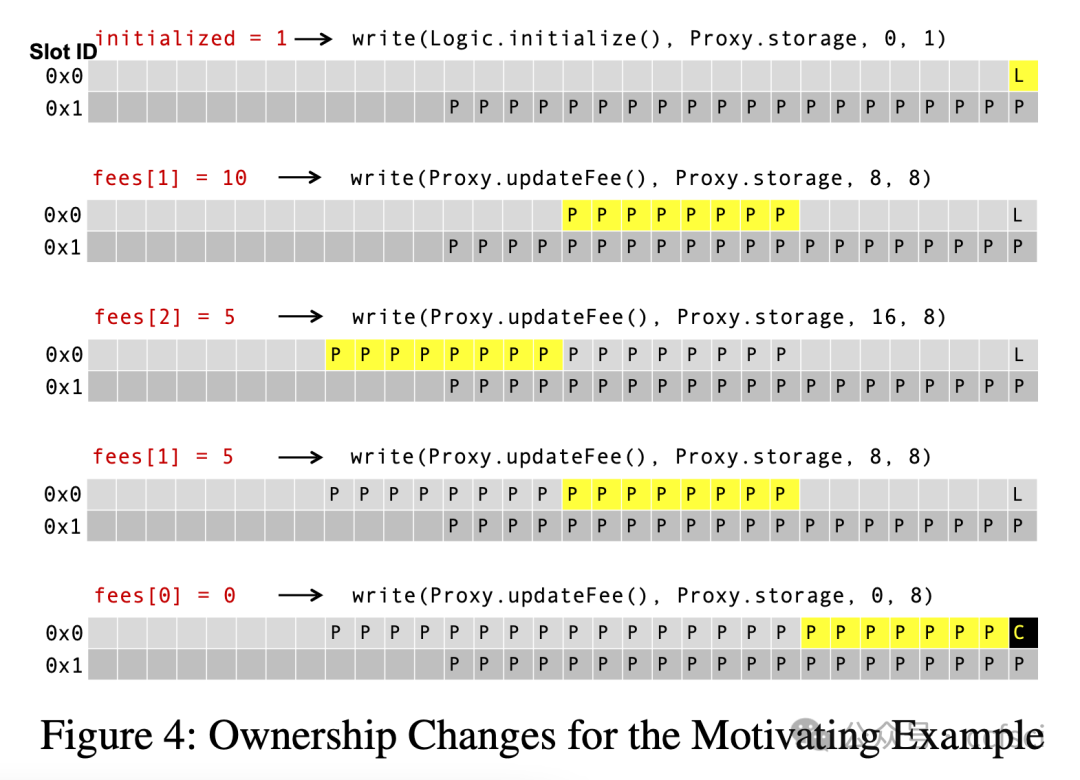

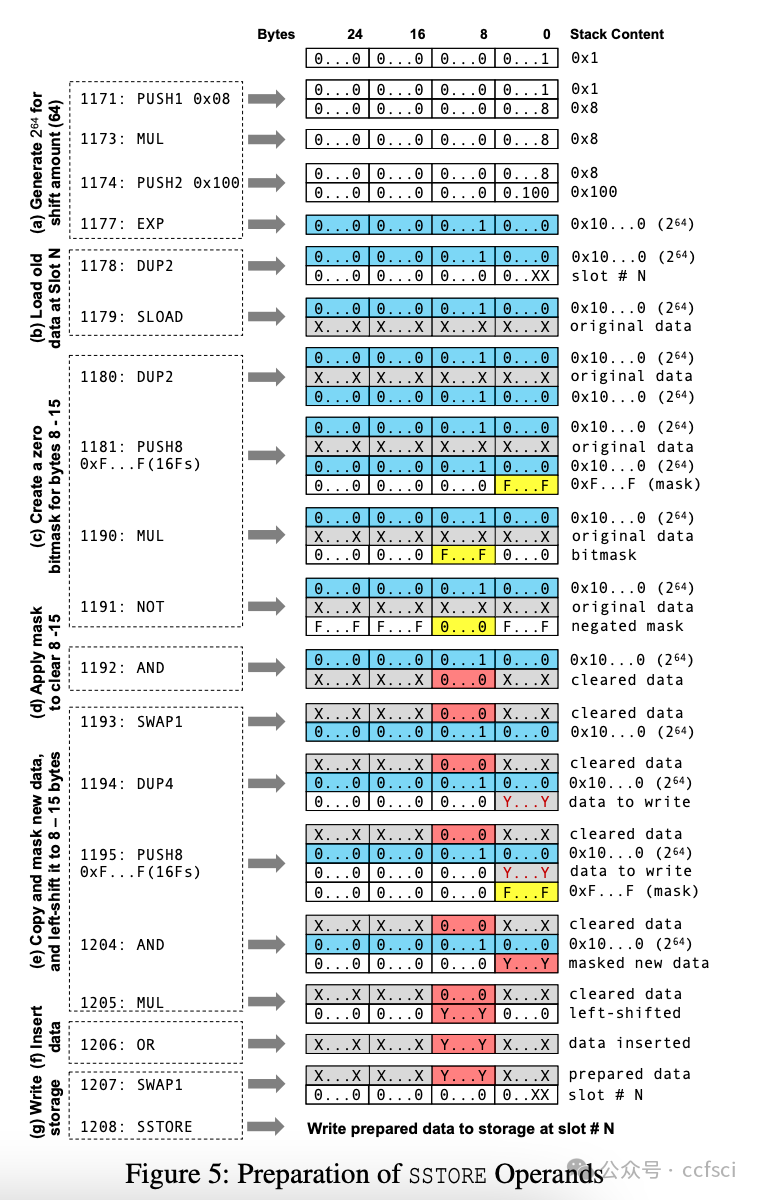
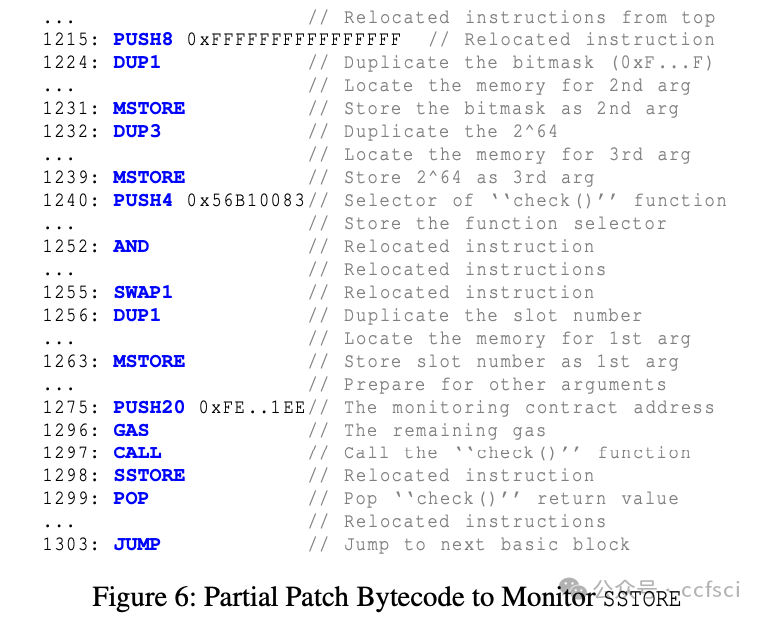
Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-pan-yu.pdf
